Over at Donna’s.
Patch patch patch.
Alex Eckelberry
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
Did you know there’s a list of people and companies that you’re not supposed to buy from?
It’s here.
Washington Post article here via Bruce Schneier.
Alex Eckelberry
If you pass around Office documents (or many other types of files, including even digital camera files), make sure they’re clean of metadata before you send them out. FCW has an article out today which discusses this very issue:
A new front line of national and corporate security is emerging, and some of the most common document applications, including Microsoft Word documents and PDFs, are putting people on it without their knowledge. In the past several years, federal agencies and private-sector companies have released documents on the Internet that they thought did not contain sensitive content, but they actually did. That has led to embarrassment, scandals, firings and national security breaches when unintended readers discovered the hidden data.
The article discusses tools such as the free Remove Hidden Data tool, something useful to have in your arsenal.
Article link here via beSpacific.
Alex
In a bizarre story, Chris Julian (incidentally, a neighbor of someone I know) was apparently caught up in a 419 scam and started to fear for his life.
The Topanga Canyon resident found a distraught Christian Julian Irwin saying he feared he was being pursued by Nigerians who had contacted him in an Internet scam, sheriff’s Capt. Ray Peavy said.
Link here.
Alex Eckelberry
How to Use Content Advisor in IE 6.0
If you share a home computer with your kids, you can control access to web sites with Internet Explorer’s Content Advisor, by using rating systems or by specifying sites that users can or cannot view. Here’s how:
You can also create a supervisor password so others who use the computer won’t be able to change these settings: Click the General tab, then the Create Password button and type in and confirm your password.
How to Disable Office Online Featured Links
Microsoft Office 2003 includes the featured links in Microsoft Office Online that lets you view new and updated information about Office, but some folks prefer to disable this feature. You can do this by editing the registry. Here’s how:
You can also use the Help menu to modify Online Content settings. For instructions on this and other ways to control these settings, see KB article 891158 here.
How to help protect yourself from spoofed web sites and malicious links
Web spoofing is a tactic used by phishers to create web pages that look like those of a legitimate company or individual, usually for the purpose of getting you to enter information such as credit card numbers or passwords that they can then use for fraud or identity theft. IE 7.0 contains the anti-phishing filters to help protect you, but what can you do while you’re still using IE 6.0? KB article 833786 contains tips for steps you can take to protect against this threat. Link here.
“Access Denied” error when you try to open or save a file in Office
If you try to open or save a file in a Microsoft Office program such as Word or Excel, and you get an error message that says “Access Denied,” then the program closes unexpectedly, it may be an issue with permissions on redirected folders. You can resolve the problem by following the instructions in KB Article 891636 here.
Error Event occurs if you repeatedly restart the computer
If you restart your Windows XP computer several times, you may find an error event added to the System log that says the System Restore filter encountered the unexpected error ‘0xC0000035’. This happens because System Restore can’t successfully rename the Change.log file. You can work around the problem by turning System Restore off and then back on, but you’ll lose your existing restore points if you do this. For more information, see KB article 903264 here.
Having someone obsessed with you – whether out of anger or unwanted affections – can be a real ordeal, and it’s not just high-profile celebrities who find themselves dealing with a foe or “fan” who won’t let go. Even if the person doesn’t physically threaten you, the fact that someone is following you around, keeping tabs on what you do, and/or contacting you when you want to be left alone is annoying at best and can disrupt your life.
The Internet has opened up a whole new world of opportunities for those with a propensity for this sort of behavior. If you visit chat rooms, participate in discussion boards and email lists, have a web site or otherwise interact with other people on the ‘net, you may eventually find yourself the target of a cyberstalker. Someone who gets angry at you because of the political views you express on your webpage or a list message may start bombarding you with nasty email messages, or someone who likes your web page photo may start sending love letters.
That’s bad enough, but sometimes it escalates beyond online harassment – your stalker may be able to use online resources such as Zabasearch to find out your address and/or phone number. And once he/she knows where you live, if you own your home it’s easy in some places to look you up on the county property tax rolls, many of which are online. These sites include the value of your home, and sometimes also show the floor plans and photos of your home. And if your car happened to be sitting in the driveway the day the tax assessor’s personnel took the picture, your stalker may now know what kind of vehicle you drive and the license plate number. Oh, joy.
Most jurisdictions have laws against harassment and stalking, and these usually are worded to include online activities. For instance, The Texas Stalking By Electronic Communications Act, enacted in 2001, covers sending of any repeated electronic communications in a manner likely to harass, annoy, alarm, abuse, torment, embarrass or offend another. There are a few states that don’t yet have laws that specifically pertain to electronic harassment, but most do. To find out what the law is in your state, see the list of U.S. laws here.
Bills have also been introduced in Congress to make cyberstalking a federal offense, due to the interstate nature of Internet communications. In January 2006, a new Violence Against Women Act was signed into law that amends the federal telecommunications harassment laws in the Communications Act of 1934. The new law makes it a federal crime (punishable by two years in prison and large fines) to anonymously annoy another person using any device or software that can be used to originate telecommunications or other types of communications that are transmitted, in whole or in part, by the Internet.
If you’ve ever been the victim of harassment, this sounds like a good thing – but it has engendered a lot of controversy. Some legal experts argue that this will stifle freedom of speech on the Internet, making it illegal to post “annoying” or “offensive” criticism of a politician on a blog. There is indeed a difference between being offensive and harassing or stalking: someone who flames you on a mailing list is being offensive; someone who sends you dozens of hate mails privately is harassing. The new law doesn’t seem to distinguish between the two.
Others worry that even correctly written laws have a high potential for abuse. If a former boyfriend or girlfriend gets angry at you, he/she could use the emails sent during your relationship (perhaps editing them) and claim that they were unwanted. In fact, anyone who wanted to cause you trouble could send forged threatening or obscene messages to him/herself from a free web mail service and claim you sent them. Other laws, such as the domestic assault laws, have already been misused in this way and the potential for false accusations is even greater when fake evidence is so easy to create.
It’s a fine line to walk. How do we make the Internet a safe place without going too far and creating cures that are worse than the disease? What do you think? Should there be penalties for saying anything offensive about anyone, anytime? Should anonymous email be outlawed altogether? Should there be federal legislation addressing this or is a matter that should be left up to the states? Have you ever been the victim of cyberstalking – or of overly broad cyberstalking laws? Tell us your opinions.
Deb Shinder
Microsoft research has released a new tool, URL Tracer, which reveals third party domains:
When a user visits a Web site, her browser may be instructed to visit other third-party domains without her knowledge. Some of these third-party domains raise security, privacy, and safety concerns. The Strider URL Tracer, available for download, is a tool that reveals these third-party domains, and it includes a Typo-Patrol feature that generates and scans sites that capitalize on inadvertent URL misspellings, a process known as typo-squatting. The tool also enables parents to block typo-squatting domains that serve adult ads on typos of children’s Web sites.
Alex Eckelberry
You can see the possible future of Google through a little string of code.
There’s these little green bars on the side, which ostensibly show the amount of content available on the various sections of Google.
Google US users can see this by going to Google, then entering the text on this page into your browser address bar.
After entering the text, refresh the page and go searching.
(If you’re in the UK, you would replace google.com with google.co.uk, and if you’re in Australia, google.co.au, other countries the same thing).
Via LifeHacker, but Digg is where I got this code. Other reference sites: imilly.com and Google Blogoscoped.
Good luck.
Alex Eckelberry
Back in February of last year, I blogged about “Why Adware works”. The answer was simple: It’s very profitable. I detailed how much money Claria had made, based on information from their S-1 (the initial filing made with the SEC to go public).
It’s not only Claria. 180Solutions is quite profitable, and has some flashy offices to show for it:
I notice that each of the company’s departments is fitted with large, wall-mounted plasma screen televisions that display graphs charting 180’s daily and weekly sales and revenue numbers. The display nearest the marketing department showed that 180 pulled in more than $1 million in the past week alone serving ads to people who have its adware installed on their computers. Today’s estimated revenue is slightly more than $100,000; the graph showing how much the company has actually earned so far today reads $2,966, but then again it is just after 10 a.m.
Link here.
The profit extends throughout the entire distribution chain. A fellow can set up a crappy little website with some stupid videos, and require that in order to watch the videos, you have to download a piece of adware. For each adware install, he gets $.25 from the adware company. It’s small, but consider some guy with 5 websites that each have 1,000 downloads a day. That’s $1,250 a day in almost pure profit. The adware company then sells advertising inventory (inventory that happens to be on the desktops of millions of PCs) for big bucks.
Now, we see Direct Revenue was awash in cash, at least in one year we examine. In 2004, the company made almost $30 million dollars in pre-tax profit on $38 million in revenue.
Link here.
Of course, this was back in the heyday of DR’s madness, and the numbers are certainly lower now.
The owners can also do well. While salaries are just great, sometimes VCs will enter the picture, purchasing stock from the owners (this is usually done as an investment into the company and then the owners get the money distributed to them). We know of three major adware players that have done distributions in this manner. (By the way, the VCs investing in these firms are not small time players, as we can see here, a list which has not been updated with the ABS Capital investment in WhenU and the follow-on investment by Trident.)
To wit, our Dear Friends Alan Murray, Daniel Kaufman, Joshua Abram and Rodney hook got a total of $12 million distributed to them from an investment by Insight Venture Partners back in 2004:
Link here.
It’s all about the money, idn’t it?
Alex Eckelberry
(With thanks to Ben Edelman)
(If you’ve come here from the PC Magazine story, you can find more of our posts on fake Codecs here.)
Emcodec, of the same ilk as Vcodec, is one of these fake “codecs” that doesn’t do any good for you. (Google search here).
It’s used as a way to get spyware on your machine.
Update: I had graphics on here but had to remove them as they were live linked to another site and not getting update.
Not surprisingly, V-Codec.com is hosted on Intercage, a notoriously spyware friendly ISP.
Beware of these fake codecs. They are bad news.
Alex Eckelberry
(Thanks to Sunbelt spyware researcher Adam Thomas and a hat tip to WinHelp2002 at SpywareWarrior.com)
Many of my faithful blog readers already know about this, but I thought I’d bring it up just in case.
There are two tools that Eric Howes, Sunbelt’s Director of Malware Research, has developed for the good of the community.
IE-SPYAD adds a long list of bad domains to the Restricted sites zone.
Enough is Enough (EiE) securely configures the Internet zone. It is a pretty significant “lock-down” of IE and will give a system a much more secure configuration than the default options in IE, but many won’t be able to handle the hassle of adding frequently visited sites to the Trusted sites zone. In such cases, IE-SPYAD is a good alternative — less intrusive, yet still protective against known nasty sites.
Alex Eckelberry
Pretty interesting today from the EFF:
“The evidence that we are filing supports our claim that AT&T is diverting Internet traffic into the hands of the NSA wholesale, in violation of federal wiretapping laws and the Fourth Amendment,” said EFF Staff Attorney Kevin Bankston. “More than just threatening individuals’ privacy, AT&T’s apparent choice to give the government secret, direct access to millions of ordinary Americans’ Internet communications is a threat to the Constitution itself. We are asking the Court to put a stop to it now.”
Link here.
Alex Eckelberry
(Thanks Jarrett)
Amazing but true. DR is bombastically and self-rightously rebutting the NY AG’s lawsuit. It’s almost funny if it weren’t so sad.
“This lawsuit is a baseless attempt by the Office of the Attorney General to rewrite the rules of the adware business. It focuses exclusively on the company’s past practices – practices we and other industry leaders changed long ago [how long is “long ago”? The AG’s investigation has evidence from as late as June of last year of pernicious practices – ed] – and says not a word about what we’re doing today,” said a company spokesperson. “We are proud of our products and the value they bring to both advertisers and consumers — the former by delivering positive, measurable results for their ad dollars, and the latter by offering free content and applications in exchange for viewing a few targeted advertisements per day.
“Mislabeling our products as ‘spyware’ does a disservice not only to our company, but also to the public by creating an atmosphere of hysteria, confusion and inaccuracy.” Direct Revenue’s software adheres to the following fundamental principles:
Consumer Consent: we obtain explicit and affirmative consent from the computer user prior to installation, and we tell the user–in plain English–that the software they are about to download is advertising-supported. Easy Removal: we make it easy to remove our software, both by supplying a link directly from every advertisement to a consumer opt-out process, and by being listed in Add/Remove Programs. No Personally Identifiable Information: We collect no Personally Identifiable Information (PII) about our users. Control of Distribution: We do not use third-party affiliates to distribute our software. “Moreover, Direct Revenue is a member of the Network Advertising Initiative, has pledged to adhere to TRUSTe’s proposed adware guidelines, and already adheres to HR 2929, even though it has not been enacted. This suit complains solely about past practices – practices, in fact, that were consistent with those of virtually all of the leading players in the rapidly evolving adware industry, including some publicly-traded companies much larger than Direct Revenue. The OAG knows that none of the challenged practices have been in use for at least six months and that this case will change nothing about our business model going forward.”
Direct Revenue is represented by the Andrew G. Celli, Jr. of New York law firm Emery Celli Brinckerhoff & Abady LLP.
“While we emphatically believe that all of the contested past practices were in fact legal, we have made a good faith effort to settle this matter with the Office of the Attorney General. To that end, we offered the Office of the Attorney General a resolution of this matter which would provide a blueprint for other adware companies to comply with the Attorney General’s view of the law and afford the broadest possible protection to consumers. The Office of the Attorney General refused,” said Celli. “Accordingly, we will defend our conduct vigorously and we are confident that the courts will bring clarity and a satisfactory conclusion to our case.”
Direct Revenue’s founders are represented by Richard Strassberg and David Goldstone of Goodwin Procter LLP.
Link here.
While DR may have changed its ways, the Spitzer lawsuit is about a fairly staggering amount of things that occurred during their investigative period last year. A review of the evidence is damming.
Alex Eckelberry
There is a new paper out by Lih Wern Wong that I would recommend that dissects the Registry. While the viewpoint is primarily forensics-based, it’s a worthwhile read for general security researchers who want to learn more about the subject.
Windows registry contains lots of information that are of potential evidential value or helpful in aiding forensic examiners on other aspects of forensic analysis. This paper discusses the basics of Windows XP registry and its structure, data hiding techniques in registry, and analysis on potential Windows XP registry entries that are of forensic values.
Link here, with a hat tip to Jamie Morris.
Update: From Jamie Morris at ForensicFocus:
One of our list members, David, has very kindly created and supplied me with a PDF
version of the paper. It can be downloaded here. Thanks David!
Alex Eckelberry
Ben Edelman has been posting new documents from the New York Attny General’s lawsuit as fast as he can. There’s much more that’s been posted, including a couple of emails from one of the VC firms that invested in them (here and here).
There’s also a number of references to “WebHelper”, who is actually now our spyware researcher Patrick Jordan (he joined us in July of last year but had been doing consulting work for us several months prior to his coming on board), and we now find he was being researched by a private investigator, as this email from Gary Kibel at Direct Revenue’s law firm shows:
But there’s so much more.
Sit back this weekend, grab a big cup of coffee and read these documents. They are just unbelievable. And to those adware “apologists” who read my blog and occasionally post, these exhibits are your homework.
You’ll understand why we’re all such “zealots”.
Alex Eckelberry
Patrick Jordan, one of our senior spyware researchers, is listed as a stalker (webhelper4u.com) by Direct Revenue (this was prior to him being employed by Sunbelt).
Stalker? Jeez, I thought the term “zealot” was the preferred term by adware guys.
Alex Eckelberry
We have not seen any cases of this exploit in the wild, but there’s a proof of concept at the Secunia site and it’s something to be aware of.
There is a new exploit which allows hackers to obfuscate the real URL being shown, useful for phishing attacks. This is a practice called address bar spoofing, and enables the hacker to make an address bar show a different URL than what is actually loading. This particular exploit creates a race condition between a Macromedia Flash file and web content being loaded.
In a test available at Secunia, Google is showing, but the page is different:
The way to mitigate this exploit is to turn off active scripting, which is also a valid mitigator for the currently active “createTextRange()” vulnerability (in fact, turning off Active Scripting in general is a very good idea, if you can handle the hassle).
Suzi over at Spywarewarrior told me that she had success mitigating the exploit by simply setting “Allow sub-frames to navigate across different domains” to Disable (or Prompt). Screen shot below:
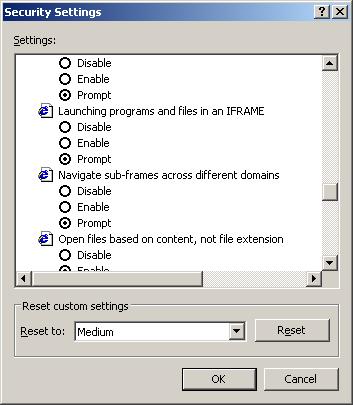
I tested this fix and it works on this test case, but there are no guarantees. Disabling Active Scripting is your best bet.
Secunia advisory here via CNET.
Alex Eckelberry
Well, nothing like the Direct Revenue documents just exposed on Ben Edelman’s site. We have obtained, from an anonymous source in the advertising industry, an email that Bill Day, CEO of WhenU, sent out today to advertisers who have a relationship with WhenU.
From: Bill Day
Sent: Wednesday, April 05, 2006 11:24 AM
To: Bill Day
Subject: WhenU, “adware” and youHi,
Many of you know me from my days as CEO and founder of About.com, and you may also know what I’ve done at WhenU – not just talked about doing, but actually done – to demonstrate that “adware” can show respect for a consumers’ right to control the desktop and be a valued part of the behavioral targeting mix.
You also probably know that NY’s Attorney General just sued Direct Revenue, that the Center for Democracy and Technology recently “outed” advertisers who work with 180solutions, and that Claria is trying to unload its desktop advertising assets.
Looks like the other players are mortally wounded or limping away – all except WhenU.
WhenU is growing. Why? And what does it mean to you and the rest of the online advertising industry?
When I took over as CEO in late 2004, WhenU was already better than the other guys, and ready to take innovative new steps to provide even greater transparency in getting and keeping permisson from consumers to deliver targeted advertising. We eliminated affiliate distribution, put our toll-free number on every ad served, capped frequency to an average of 1-3 ads per day, and made it even easier for people to opt-out than to opt-in. As a result, we have a better business than the other players . Our click-through and conversion rates are rising; our revenue and reach are growing. Last week, we even got a nice nod in the New York Times and a great write up in this month’s Inc. Magazine.
The moral of the story is: good business practices equal good business.
Leaders lead. Count on us to continue to be a leader here. WhenU’s goal isn’t to be the last man standing in the “adware” space. Our goal is to change the space – so that truly permission-based desktop advertising earns its place in the behavioral targeting mix and the Internet becomes a safer place for users and marketers alike.
All of us at WhenU look forward to continuing to treat our twin masters – consumers and advertisers – with the utmost respect and transparency. I encourage you to contact me directly if you have any questions or comments.
Best,
Bill
Alex Eckelberry
Ben Edelman has been putting up additional documents from Elliot Spitzer’s suite against Direct Revenue as fast as he can. These are the exhibits referenced in the highly damning affirmation and petition written by NY AG attorney Justin Brookman. There’s more being put up regularly, so check back.
Here is the documentation of a completely corrupt organization. Solely for personal gain, officers of Direct Revenue lived, ate and breathed to rape the machines of unknowing Internet users.
Some tasty snippets:
Exhibit 2 -146-page compilation of December 1, 2005 interrogatory responses and attachments. Includes the following:
Discusses Direct Revenue’s installation counts. (2)
Discloses revenues ($6.9 million in 2003, $39 million in 2004, $33 million in January-October 2005). (4) Discloses revenues from installing other vendors’ software ($4 million for January-October 2005). (4)
Discusses the role and effects of Insight Venture Partners’ 2004 purchase of 25% of Direct Revenue for $12 million, and Direct Revenue’s borrowing from Insight and Technology Investment Capital Corp (TICC), $21.7 million total in 2004. (4-5) Shows specific 2004-2005 distributions to Direct Revenue’s senior staff, totaling more than $27 million. (6)
Discusses the ad networks used to track advertising display, including Aquantive’s Atlas and DoubleClick. (8) Discusses other sources from which Direct Revenue receives ads, including LinkShare and eBay Shopping.com .(8)
Exhibit 4 – Direct Revenue LLC agreement. Reports Joshua Abram as 36% owner, Daniel Kaufman as 32% owner, Alan Murray as 27% owner, and Rodney Hook as 5% owner.
Exhibit 5 – User complaints and threats, and Direct Revenue’s responses (including jokes)….
Exhibit 6 – 122-page compilation of January 17, 2006 interrogatory responses and attachments….
Discusses the limited circumstances in which Direct Revenue elected to automatically remove its software from users’ computers after concluding that installations were nonconsensual. Argues that such automated removal constitutes “throw[ing] the baby out with the bathwater” because it would (purportedly) not be “in the best interests of the many users who had accepted [Direct Revenue’s] value proposition.” (2-6)
Discusses disclosures shown to Lycos users as to “the search panel feature of your Internet Explorer program” being “under new ownership.” (11-13)
…Discusses a “KZ Torpedo” to remove unknown other software. (23-34)
…Presents Direct Revenue’s records of specific users, including users’ IP addresses. (36)
Exhibit 18 – Discussion with Holistyc of distribution methods. Discusses possible use of “tricks” to improve installation rates, as well as methods of “dogting SP2 and anti-virus programs ”
Exhibit 19 – Discussion of a Microsoft invitation to a September 2004 “Microsoft VC Roundtable.” Admits that Direct Revenue “takes advantage of their [Microsoft’s] vulnerability and poor design.”
Two words: Treasure trove.
Link here.
Alex Eckelberry