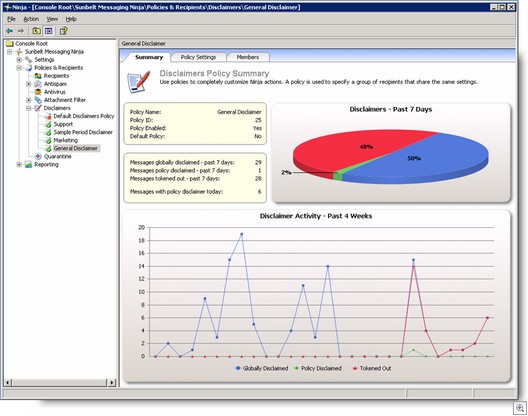
I’m getting ready to spend next week in Seattle and in Redmond at the Microsoft main campus. It’s that time of the year again, when Microsoft hosts the annual MVP Summit, and it’s a time when I not only get to meet in person some of my fellow MVPs from around the world, but also get some great “inside information” on upcoming Microsoft products, some of which I’ll be able to share with readers.
It’s always interesting being inside the belly of the beast, and this year – for the first time in several years due to scheduling conflicts – Bill Gates will once again be with us for the festivities (not that I didn’t enjoy Steve Ballmer’s dynamic speeches). We leave early Monday morning and come back Thursday night, and we have a very full schedule – from 8:00 a.m. to 11:00 p.m. every day (that includes the official dinners and parties, which provide great opportunities for networking and finding out what’s going on “under the hood”).
There are different tracks for different specialties, and mine is security so I’m hoping to learn more about how Microsoft plans to make future products even more secure, but I’m also hoping to find out a little bit about some of the features that will be included in those products. Everything that doesn’t fall under the non-disclosure agreement, I’ll be writing about in the next few weeks, here and on my blog. While on the road, I’m planning to take advantage of T-Mobile’s offer of free HotSpot wireless for Vista users, and I’ll be reporting back to you on that.
Meanwhile, last week I was invited to partake of the Windows Home Server private beta. WHS is an interesting concept and we got a first look at it at the Consumer Electronics Show (CES) in January. This is an operating system that’s based on Windows Server 2003 R2, Microsoft’s enterprise-level server OS – but it’s designed for home use and is supposed to be so simple your grandmother can administer it.
Why would anyone need a server at home? Remember that only a few decades ago, the idea of home computers was dismissed by many as a flight of fancy. Now, according to recent statistics there are at least 40 million households all over the world that have high speed Internet access and at least two computers in their homes. Where there are two or more computers, sooner or later there’s likely to be a home network. And once there’s a network, a server can’t be far behind.
The main purpose of a server is to provide a centralized place for storing files so multiple users can access them easily. This also makes it much easier to back them up, since they’re all in one place, and that makes it less likely that you’ll lose important data.
Of course, you can share files on a home network without having a server. All you need to do is set up a peer to peer network and make your computers members of the same workgroup. The problem with this scenario is that the shared files stay on individual workstations. That means they may not always be available when you need them. If mom turns off her PC at night, or dad disconnects his laptop and takes it to the office with him, or Junior’s system crashes, others on the home network lose access to any shared files on those computers.
That’s the reason many families are already using de facto servers. They designate one computer, often an old desktop PC that’s left over after someone gets a new one, put it in a central location, leave it on all the time and have everyone save the files they want to share to a shared folder on that system. This works, in a crude fashion. What Microsoft aims to do with WHS is take the idea a step or two further.
WHS uses a brand new technology to aggregate all the files that are stored on the server into a single “storage pool” so you don’t have to worry about drive letters and which drive you saved something to. It also mirrors the data to two different disks, so that you have fault tolerance similar to what businesses and techies get with RAID, but it’s set up automatically and much easier to work with – no advanced technical knowledge is required. And when you outgrow the disks in the system, you can swap out your 200 GB drive for a 500 using a wizard that preserves your files and keeps them accessible.
The Windows Home Server also automatically backs up not just everything on the server, but files on all the other PCs on the home network, too. There’s a full PC image of each computer so that if any computer has to be restored, it’s easy to do. And WHS monitors security related settings on all the PCs so that you can know whether all the computers have their anti-virus software turned on, for example.
One great use for a home server is to share media files such as music and recorded TV programs. And it’s not just other computers that can access these files on WHS. Media Center PCs and Xbox 360s can also play songs and shows from the server. And if you’re at the office or out there on the road, you can access the information on WHS remotely over the Internet.
Note that the server doesn’t function as a regular computer in that you can’t sit down at it and work at it. It doesn’t have a monitor or keyboard or even a place to plug them in. The hardware connections are as simple as it gets: other than the power cord there’s only one jack, an RJ45 Ethernet port. You plug the server into your network’s hub or router and set it up through another PC on the network.
I’ll be reporting more on WHS in the future. Meanwhile, tell us what you think about the idea. Is it another solution in search of a problem, or a great idea? Do you run a server on your home network now? Would you if it were easier to do? Or are servers just for businesses? What’s your “wish list” for a home server (what do you want it to do for you)?
Deb Shinder, MVP