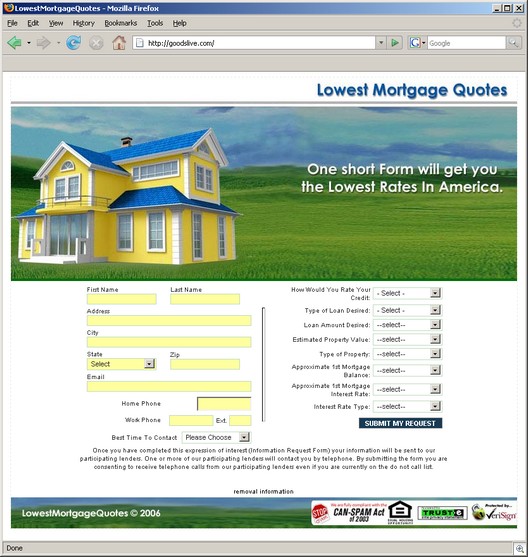
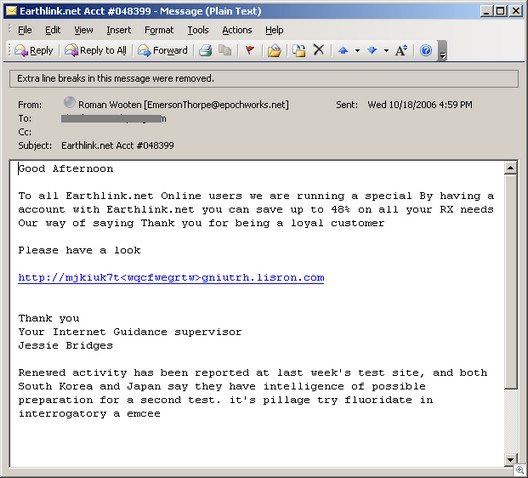
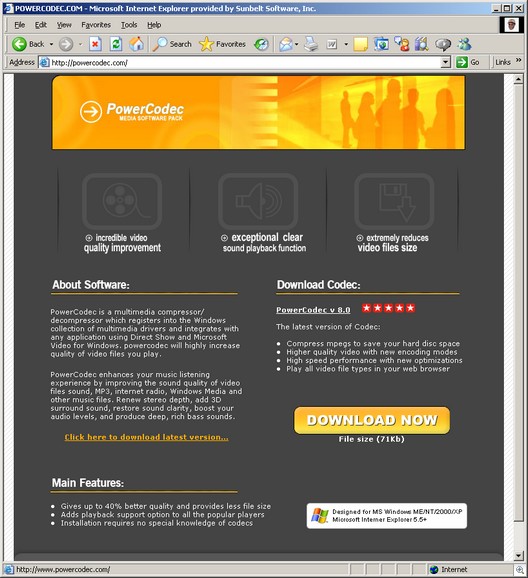
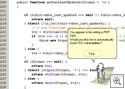
Our new sandbox technology was officially announced this morning at the Infosec conference in New York.
Sunbelt Software today announced the availability of Sunbelt CWSandbox, a powerful tool for the automatic analysis of malware samples. The technology was originally developed by noted security expert Carsten Willems while at the University of Mannheim and is under exclusive license to Sunbelt Software.
CWSandbox provides technology providers and corporations the ability to rapidly analyze malware for a number of different purposes — security research, creation of new signatures, forensic/criminal analysis and improved threat protection. Malware samples submitted to the sandbox are executed in a controlled environment, with a comprehensive analysis provided of the malware’s execution in XML, HTML or text format.
How CWSandbox Works
Using a comprehensive automated system, CWSandbox uses unique technology to execute malware in a controlled environment for behavior analysis. The application provides fast analysis of large volumes of malware samples in a short period of time, capable of automatic collection of malware from different inputs including Nepenthes (a tool for automated collection of autonomous spreading malware), a web server/interface, or a directory.The CWSandbox is an awesome tool for malware analysis. Submit a piece of malware, and you’ll get a detailed report back as to what the malware is actually doing. In addition, the sandbox will also run the malware through several different AV engines to give you a feel as to what the in-the-wild detection is.
Link here.
Try the sandbox out youself — go to www.sunbeltsandbox.com and submit a malware sample.
Our business model for the sandbox is simple: Anyone can freely use our public sandbox for malware analysis. If commercial entities want to bring the power of the sandbox in-house, they can purchase a reasonably priced license. Entities involved in pure research (e.g. no commercial intent) can license the sandbox at no-charge. More information can be had by contacting a specialist.
Alex Eckelberry
![Chimage[2]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/chimage%5B2%5D.gif)