Hopefully the two Yahoo phish pages listed below won’t be online for too long:
They’re located at
nudeyahoo(dot)hi2(dot)ro/foto/
and
maill-yahoo(dot)com
Christopher Boyd (Thanks to Wendy for finding these)
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
Hopefully the two Yahoo phish pages listed below won’t be online for too long:
They’re located at
nudeyahoo(dot)hi2(dot)ro/foto/
and
maill-yahoo(dot)com
Christopher Boyd (Thanks to Wendy for finding these)
Batman. His interests include being vengeance, the night and also kicking people in the face.
Something Batman probably doesn’t enjoy so much is seeing the trailer for his new film leak, then be turned into an instrument of evil (or at least poor web marketing and cheap tricks). In fact, you know it’s time to strap yourself in for another security trainwreck when you hear about the leaked Dark Knight Rises trailer, fire up Youtube and see…
Batman, everybody!
There’s a similarly authentic looking Youtube clip here:
Clicking the link takes you from xisworld(dot)com to rrgr(dot)info/news(dot)php where the Dark Knight is apparently being hunted by, er, FOX News:
You’re offered an install of FREEzeFrog, ShopperReports, QuestScan address bar and blinkX Beat. Readers will be familiar with these types of install. As you may have already guessed, there is no Batman trailer or any FOX News for that matter.
Here’s an example of a site offering “the full movie”.
I’m not sure which I trust less, the clipart logo or the fact that the trailer is the fake one containing Robin Williams and clips lifted from Se7en and Aeon Flux. Clicking the links take to to various sites wanting you to “sign up” to watch the movie, often asking the user to provide card details and validate their account.
Good luck with that.
I’m going to go out on a Batman snapped limb here and take a wild guess that you won’t be seeing the full version of Dark Knight Rises anytime soon – certainly not from random Youtube vids promoting installs, surveys and “watch movies anytime” services.
You don’t have to be the World’s Greatest Detective to work that one out.
Christopher Boyd
Here we have a website claiming you can “Play Super Mario Online”, complete with looped Youtube video and a large “Start Here” button at the bottom of the page.
playmario4free(dot)com/networks/vc/index(dot)html
As you’re about to see, The Princess is most definitely in another Castle.
Hitting the “Start Here” button downloads a file called “SuperMario.exe”. However, this isn’t so much “It’s a me, Mario” as it is “It’s a me, a bunch of other stuff instead”.
We’re still looking at it, but the “competitor killer” file has a rather interesting name – especially if you remember these antics from 2004/05. Here’s an example of adverts appearing on Facebook with this installed:
We informed Zugo about this bundle, and they reported to us that they were in the process of identifying and terminating the affiliate responsible. At time of writing, our US based researchers confirm Zugo is still appearing in testing, whereas other regions end up with something altogether different. For example, this one is from the UK – say hello to “FaceTheme”:
Christopher Boyd (Thanks to Matthew for finding this one)
Update 1: Matthew performed some additional analysis on the competitor_killer.exe. Here’s a list of the apps it targets (based on strings found in the file) – notice FaceTheme is listed, even though it is appearing in installs alongside Web Essentials above…
FBLayouts
GamePlayLabs
Yontoo/PageRage
FaceTheme
Cartoonly
Our friends at Commtouch have blogged about something that is no surprise — spammers using compromised accounts vs. bots (their latest threat report is quite good and worth reading btw).
While compromised email accounts (hotmail, yahoo, gmail, etc.) are not new, there is a little more to it: There was a massive takedown of a major spam operation by Microsoft several months ago. This led to spam levels dropping to their lowest rate in three years. Gamechanger for the spammers. So what we’re likely seeing is a) the percentage of spam from compromised accounts increasing, because Rustock is out of the equation (the mix of compromised accounts vs. legitimate has changed) and b) it’s just getting harder to use botnets, so they’re going after compromising existing accounts. Since Commtouch didn’t publish data as to the raw actual numbers of compromised accounts vs. bot spam, it’s difficult to tell.
Nevertheless, bots are still out there. But compromised accounts gives spammers the ability to hijack the reputation of an existing user and service (hard to blacklist all of Hotmail, for example). You could spoof an email to look like it’s from gmail or Hotmail (and there is a lot of that), but that’s not nearly as powerful as a compromised account, because the IP ranges are trusted by spam filters, and generally, the sender is trusted by you (it could be a family member, or a friend).
You can see in the chart below that Hotmail is more compromised than Gmail. Gmail spam is almost all spoofed — simply creating a fake gmail address in the From address — a poor way of getting by spam filters.
However, it’s not necessarily pharmacy ads and the like. There’s plenty of malwere. There’s also malicious links, which themselves can pose a greater problem, because malware is often caught going through an antivirus filter (either because of attachment policies or because the malware itself are caught). However, malicious links from a trusted sender present a far bigger problem.
For example, here’s a current spam run using a compromised Hotmail account we saw yesterday (they simply stole the user credentials), pushing a rogue antivirus product:
Same spam run, both with the same results – clicking on the link redirects one to a page that looks like this:
This pushes a download of WinWebSec SecurityShield, with atrocious detection by AV vendors. So antivirus detection being awful in this case, the emphasis becomes on defense-in-depth. A good spam filter may or may not help, because this email comes from one of your trusted senders and may be ignored, depending on your policies. A good web filter would certainly help significantly. And so on. However, since social engineering is at play here, education is of tremendous importance.
Alex Eckelberry
Last week, you could (in theory) been searching for the country singer Katie Armiger.
No, I have no idea who she is. Anyway, this is what you would have seen:
Number One with a bullet, or at least a baseball. At time of writing, the site seems to be fixed (there’s a lot of pink and frilly dresses on it, so I assume it’s fixed).
Elsewhere, we’re seeing quite a few phishing pages pretending to be Facebook security checks.
“Did you log into Facebook from somewhere new?”
Over at the Malware Protection Center, we’ve seen a steady stream of Privacy Center clones and the odd FakeVimes Variant. Sporting names such as Windows Armature Master, Windows Accurate Protector and Windows Test Master, you can be fairly certain that seeing the below is a sign of infection:
Finally, another example of why you shouldn’t reuse passwords. I’m willing to bet a lot of people use the same password for both their Steam account and the EMail address associated with it. This makes you easy pickings if you lose either one to a phisher. However, split those logins up and should the evil Steam phisher grab your Steam details, when logging in on their PC they’ll see this appear:
Yes, Steam will pull them up about logging in from a new computer. At this point, an EMail is fired to your associated account and the phisher isn’t going to get very far without access to your mailbox:
Good, eh?
Of course, this security procedure isn’t going to help the user much if they reuse passwords. For everyone else, it’s one last chance to regain control of a compromised account.
You don’t reuse passwords, do you?
Christopher Boyd
Update: Looks like we’re all clear — all links have been removed.
Well, this is certainly a busy time for the porn/malware bad guys. The same folks who apparently spammed Sourceforce with porn and mawlare redirects are now doing it on, of all places, Flickr.
Instead of posting photos, however, they’re posting links, like this:
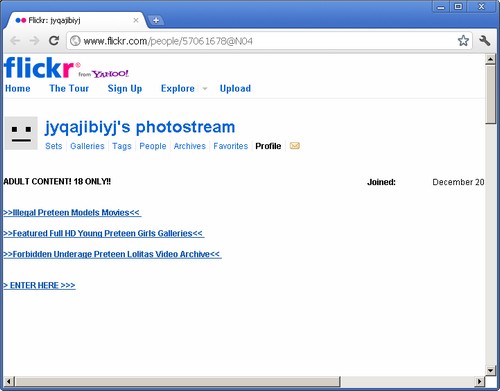
The links point to a URL shortener (for example, hxxp://1k.pl/ flickr), which then redirects through an interim page to something like this:
(We’ve removed the images, of course.)
Clicking on one of those links will give you malware — not a pleasant thing.
A list of the malicious URLs we were able to find are here.
Alex Eckelberry
(Hat tip to Patrick Jordan)
Recent reports of “imported hardware entering the US with hidden malware” are grossly exaggerated.
Occasionally, a virus creeps into some piece of hardware or software, but that’s because of shoddy manufacturing or just honest mistakes (it’s for this reason that every piece of software that Microsoft releases goes through a multi-engine virus check).
Sometimes, there’s just a blatant, err, false alarm. Then there’s the idiotic “Dell ships with a keylogger” hoaxes.
The supply chain is not inviolate, and there is a cyber security risk. However, there have been very, very few — if any – reports of malicious software being embedded maliciously into imported hardware.
I’m not going to be a pollyanna and say it can’t happen. But there’s a difference between “it could happen” and “it has happened”.
If you want to understand where this all comes from, it’s from a short exchange between Representative Chaffetz (who clearly believes this is happening daily) and DHS National Protection and Programs Directorate Greg Schaffer.
Schaffer actually missed the original question, and then, appearing a bit flatfooted, answers in the affirmative, and then Chaffetz states rhetorically that this is a problem. You can see the exchange for yourself at the 51 minute mark.
From this pebble we get a mountain?
Alex Eckelberry
Browser specific scams have mostly been seen in the realm of rogue AV attacks, but here’s one (located at update-center(dot)myftp(dot)org) that checks out your browsing credentials then sends you to one of the below locations for a fake flash update:
IE8: Redirected to usa(dot)gov. No fake flash for IE users. It’s a different story for Chome and Firefox, though.
Chrome 12.0.742.112: You’ll be asked to run “v11_flash_AV.exe”
Firefox 5.0: You’ll be asked to run “ff-update.exe”
According to our man Patrick Jordan, these slices of Malware are 2GCash variants. Breaking out the history books, he tells us:
“2GCash began around July 2008, and started with:
A) FakeCodec sites
B) Online Scanner Scam sites
C) Fake Crack Serial sites.
The primary function has always been click fraud transmission and Search Engine Results hijackings.
Their secondary function is to potentially bring down PDF exploits, rogues, and other types of malware.
In 2010 they started monitoring for VMware so you can only install them in a normal computer.
They also tend to rotate variants almost every 6 to 12 hours as a method to try and evade detection.”
We detect these as VirTool.Win32.Obfuscator.hg!b1 (v). Steer clear!
Christopher Boyd (thanks to Adam, Wendy and Patrick for finding this one & additional research)
However, should you arrive at the following link, you’ll be bounced to one of those “Earn a fortune working from home” websites:
simpleonlinecareerlibrarydv(dot)tumblr(dot)com/Yz3Em
“Working from home leads to shocking money results”. It probably does if you get involved with one of these things.
Of course, they use geolocation to make it look like the “news site” is local to you – and it goes without saying the offer they have for you expires today. Move quickly!
In the opposite direction…
Christopher Boyd
Follow-up from our blog yesterday: The Search option is now no longer available on the Microsoft Safety and Security center.
The searches themselves are still there, just checking on Google.
Nevertheless, I have every reason to believe that Microsoft will sort this out fast. My personal experiences with their malware research and security teams have always been positive and I am certain they will get this issue resolved rapidly.
Alex Eckelberry
Update: Looks like we’re all clear — the searches have been cleaned-up.
.
The Microsoft Safety and Security Center has become a hot bed of porn redirects, and sleazy porn sites invariably lead to malware.
And there’s an interesting twist to how this occurred. Search poisoning, on its own, is no big deal. But in this case, something else is going on.
Since we’re a (sort of) PG 13 blog, I’ll give a mundane example: A person goes to the Microsoft Safety and Security center and types in “girl” in search box.
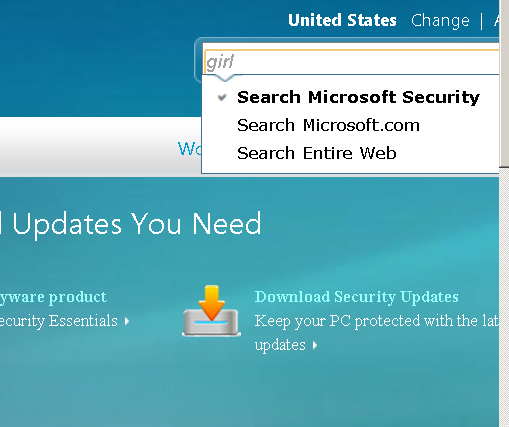
The search results have been poisoned. Even an innocous search such as this one returns nasty results (don’t click on the thumbnail if you’re offended by foul language):
(Searching for porn terms will yield some very nasty results. Most of the stuff is far too disturbing to post on this blog.)
Interesting SEO blackhatting: Why is this different? Normal search poisoning is where results come up that directly link to a site. However, blackhat SEOs have created Microsoft Security Center search results on specific terms. These terms include things like:
porn
you porn
free porn
free filipino porn video
prnhub
streaming
you tube sex
And even: “baby girl names”
You can see this with a Google search on microsoft.com:
(It’s ironic that only Microsoft Safety and Security Center searches are returning porn results. Nothing else at Microsoft.)
Since only specific terms are used, if you search using a different term, say “united nations”, you’ll get real, normal results.
In other words, blackhat SEOs are seeding illegimate search results within the Microsoft search results. Pretty tricky and impressive. There are a number of ways this could be done (for example, using the ability on the site to Twitter a search result).
Confused? You don’t need to be. Just know that inevitably, these types of things can lead to malware.
Just a bit of hunting around on the search results, and you might find something like this:
And pressing download gets you to a fake codec site, which pushes malware:
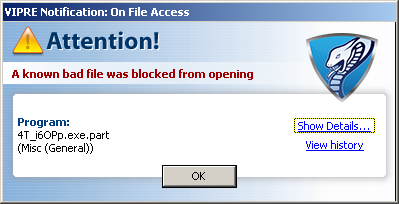
It’s Zugo,a Bing-branded search toolbar with a history of being installed through exploits and other misleading/deceptive means. It’s a a rather poetic twist of irony (unrelated to the search story here), that Zugo is a Microsoft Bing partner.
At any rate, let’s hope this all gets cleaned up soon…
Update: Looks like we’re all clear — malicious links have been removed.
A month ago, we blogged about FakeRean (a very nasty malware/rogue antivirus) being served by PHP spam off of Sourceforge.net. We figured something would happen.
Well, nothing happened.
We’re still seeing hardcore and lolita porn spam on Sourceforge. It’s all PHP hacks, which points to sloppy moderation and site stewardship; worse, this is not just junk spam like “buy Russian handbags”, but rather, redirects to sites that often serve malware.
Case in point is this spam promising lolita porn.
In this case, clicking “Yes I am 18+” (which a majority of under 18’s do anyway), you get redirected to one of a variety of porn sites, often serving malware. (In fact, it doesn’t really matter if you click “No” or “Yes”, you still get redirected.)
Using basic reputation hijacking, a Google search redirect is used:
hxxp://www.google.com/url?sa=D&q=http:// seoholding. com/12/commonground&usg=AFQjCNGnwpgXRDmIHULLMas4fJSt0f3FSg
And this all lands one at a variety of sites, of which we show a few (we’ve turned off images in the browswer as it’s all a bit ghastly).
These sites will either push a download of the “movie” or ask to “update your flash player”. In any event, it’s malware.
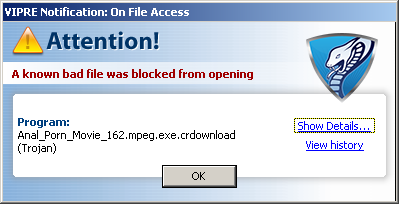
Detection rates are fairly poor: Fake MPEG, Fake Flash Player.
Another reason why doing some basic google searches on your own site can really help clean things up for the Internet at large.
Alex Eckelberry
You’ll also see this:
“Free Google+ invites instantly”?
Opening the short URL presents you with – oh, I’ll let you take a wild guess:
Yes, it’s survey time. Once you’ve finished winning Starbucks gift cards and have decided who would win in a fight between Ronald McDonald and The King, you’re left with the following download:
“Googleplus2.rar”? Well, that sounds dubious – especially as the uploader is also promoting what appears to be a collection of stolen RuneScape accounts. There seemed to be an issue with the surveys on offer, so we couldn’t download the .rar to see what was inside but we’re guessing either 1) garbage or 2) pilfered accounts from, well, anywhere really.
Elsewhere there are some interesting profiles starting to appear on G+. Here’s one promoting a “free iPhone apps” website:
Visit the link, and you’re presented with numerous programs to download.
As you can see, they have your sword…and your bow…and your Golden Axe.
It’s also listed as “cracked”, and as you well know randomly downloading “cracked” programs can often turn out to be a bad idea. Depending on which download links you use, you may also be presented with requests for payment before downloading.
£10 for premium access through SMS? Not so much “free iPhone apps” as “sort of free iPhone apps if you click the right link, maybe”.
Spammers are already firing fake invite emails around for pharma sites, and you can bet the Youtube scam videos and G+ profiles linking to potentially unsafe downloads will start to increase in frequency as the days roll by.
Let’s hope the scammers don’t pile in wholesale on one of the more entertaining services I’ve seen launched in recent months.
Christopher Boyd
There’s a Spanish language Facebook fakeout knocking around this week, a variation on a tried and tested scam theme (aren’t they all?)
Here’s a “Facebook Dislike Button” site, located at descargarapida(dot)es:
A Justin Bieber themed Dislike scam, no less! Well, we can all get behind that.
Anyway, according to my reasonably decent translation program the text reads:
“New Button: Do not like! Install on your Facebook profile now”
Meme fans will no doubt be giggling away at the “Me Gusta / No Me Gusta” buttons. Everyone else should be making a mental note never to fall for the “Click here to install a no like button” scams, regardless of language or how many pictures of Justin Bieber they splash across the screen. A few days ago it was serving up a “login to see these girls in a pool” page – however, at time of writing the page cannot be reached and loops you back to the Bieber boobery. Thanks to the magic of Google Cache, we can take a look at what was taking place:
If I had to guess at what this one involves when fully working, I’d be tempted to say “pops up a survey”. Who knows, but I’m nominating all of the above for a definite “Not Like”. In fact, you could say….
Christopher Boyd (Thanks to Robert for sending this one over)
Our friends at Sophos has found what we consider as, probably, the first crime ever targeting Google+: fake pharma spam. Due to the high demand of G+ invites being thrown at Google, to the point that the company actually had to cease the invitation process for the beta release of their fledgling social networking site, it is no surprise that spammers have latched onto this one as their latest target (and growing favourite?) to date.
Better than having malware there, if you ask me.
That, of course, does not change the fact that receiving supposed G+ invitations leading to fake pharma site is annoying.
“The spammers are no doubt hoping that the email will be too hard to resist for many people eager to see Google’s new social network, although just how many users will be tempted to buy drugs online is a mystery.” concludes Sophos regarding this report.
Indeed.
Screenshot of the G+ spam from Sophos
Personally, I am a bit jolted by the fact that spammers didn’t take long before they push a campaign to take advantage of Internet users badly wanting to be put in circles. It’s the current “it” thing, after all. Not to mention the current perfect target of any threat attack, and spamming was the first. I can only guess what could come next after that.
It’s a jungle out there, folks. As always, please stay safe. 🙂
Jovi Umawing
A hazard of cloud-based services is reputation hijacking — using the cover of a legitimate cloud service to do bad things. For example, you can’t block the domain “Google.com”, because it has legitimate purposes. So a network administrator is left in a difficult quandrary.
As an example, Google Docs (specifically, Spreadsheets), is a playpen for phishers. We have found a very large number of phishing sites using Spreadsheets, especially for stealing credentials.
These phishing sites all use the ability of Google Spreadsheets to create forms. These Google forms have wonderful legitimate uses, such as empowering teachers with the ability to collect data from students. But their ease of creation makes for a dangerous situation.
Since all of these forms use the “formkey” parameter in the URL, searching for them is trivial, using a simple google search like this one.
Schools are a particular target, but it’s not limited to just that area.
One major area of popularity for this use is in Indonesia, where these phishing sites are setup to steal credentials for various games. Gemscool (an Indonesian gaming site) is a particular target, such as for the Point Blank (PB) and Lost Saga games.
Some examples:
If it only takes a simple Google search to find these, one wonders exactly why these aren’t being policed more aggressively. This is trivial stuff to find.
Alex Eckelberry
(With thanks to Sonny Discini)
1) “Facebook Survey Gift Invite”.
“You’ve been invited to participate in our short Facebook survey”, they say. Considerably shorter than they expected:
Let’s not and say we did.
2) An interesting attempt at sending users to a Paypal phish:
“Unfortunately, your recent transaction was declined because your PayPal account is currently restricted. PayPal may restrict accounts for a variety of reasons to prevent fraud and verify the identity of users.”
Yes, they want to play on your fears of having a restricted PayPal account to send you to a phish page located at zurl(dot)biz/www(dot)paypal(dot)com. Avoid.
3) World of Warcraft phish mails. The site listed in the below example is currently offline, but it’s a pretty standard (and popular) template.
Click to Enlarge
“You’re trying to sell your account which is breaking the EULA, confirm you’re the original owner by visiting this link…”
As you’ve likely guessed, this is the last thing you should be doing.
That concludes our spam roundup. Stay safe…
Christopher Boyd
WWF Philippines’ site is hacked by some Madoka (it’s an anime) fan. I don’t know whether to laugh or cry.
The above was the actual tweet from a chain of retweets that reached my stream and got us (Chris and I) looking into this matter. This one below was the screenshot we captured:
Click to enlarge
The Earth Hour section seems back to normal now.
GMANews.TV has given us an interesting news angle to chew on. According to them, the individual behind the WWF and Bureau of Customs Web page facelifts are one and the same given their reference to the keyword “mahou shoujo”, a term used to classify a sub-genre of Japanese anime and manga, found in both attacks. We can neither confirm nor deny this, but it is a good point to keep in mind.
You can read more about this story on this GMANews.TV Web page.
Other grueling stories of defacements in the GFILabs Blog:
Jovi Umawing
How does it work?
It’s a simple enough attack, luring Tumblr users with the promise of “hidden” pornographic content that requires entering login credentials to view. “This page contains adult content. Please revalidate your credentials”:
The pages involved are all regular Tumblr users who have previously been compromised. Once hijacked, their pages are converted into the fake logins and then sent into the world following regular Tumblr accounts. At that point, the phisher hopes those same accounts will visit the fake login, enter their details and keep the cycle going.
What sites are involved?
A handful of domains have revealed themselves to be at the heart of this scam, domains which we’ve previously written about.
tumblriq(dot)com
tumblrlogin(dot)com
tumblrsecurity(dot)com
Tumblriq(dot)com was registered on the 15th of June to someone called “Jack Alimae”, and the other two URLs were registered on the 25th to “Mike Alexander” – however, both sets of registration use the same address which suggests potentially fake data was used somewhere down the line.
Tumblriq(dot)com started out here on the 23rd of June, serving up various adverts to users clicking on compromised Tumblr accounts promoting a “Tumblr IQ Society”.
Not long after this, the additional domains started to appear and then the full scale phish invasion took things up a level, with compromised accounts serving up a mixture of Tumblr hosted text and login credential submission forms served up by free webhosting accounts. While many of the compromised Tumblr accounts wanted you to login on the same page, many more besides were redirecting end-users to the tumblrlogin(dot)com website.
If ever a scam page had a name that implied you should do the exact opposite of what it suggested, it would be that one. The problem has become so pervasive that regular Tumblr users are setting up dedicated anti phishing sites to advise users of the problem. One of these sites actually pointed us in the direction of one of the dropzones used for the stolen logins, and the problem does indeed seem to be out of control at this point.
The data we saw contained 8,200 lines of text stretched across 304 pages of Microsoft Word, and even accounting for the inevitable duplicates and fake data that’s still quite the goldmine of pilfered login credentials.
There have been other data drops, but the scammers keep moving them around. We have of course notified Tumblr in relation to the hijacked accounts.
Why Tumblr?
What does somebody want with that many Tumblr logins? We can only guess. The stolen accounts could be used as some form of advert affiliate money making scam, or maybe we could see lots of pages with survey popups pasted over them. There is the very real possibility that the Tumblr accounts are simply a way to test if those users are logging into other services with the same credentials – at that point, everything from email accounts to internet banking sites could be fair game.
At time of writing, all three .com URLs are not resolving, although whack-a-mole has been taking place with these sites for a few days now. They could well return at some point (indeed, one of the free webhost phish pages is still alive despite countless reports to the host) and Tumblr users would do well to verse themselves in the art of phishing scams, and fast. These issues make the recent messaging spamrun on Tumblr look like a very small drop in the ocean at this point.
Christopher Boyd and Jovi Umawing
(Thanks to Steven Burn for takedown assistance and Antiphishing on Tumblr for their work in tracking the scammers).