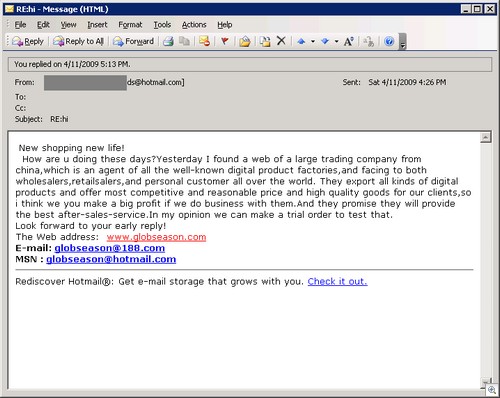
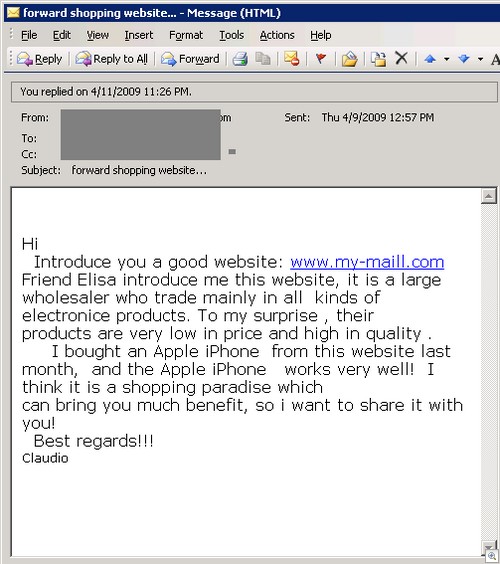
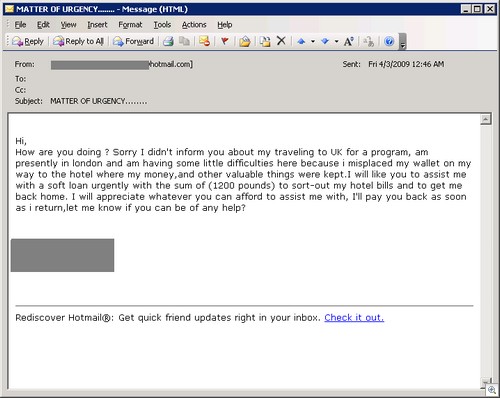
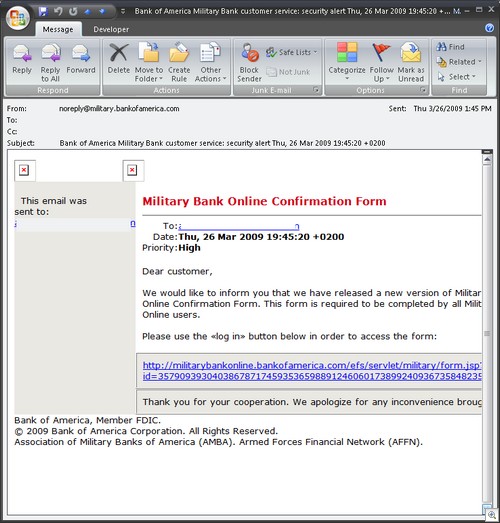
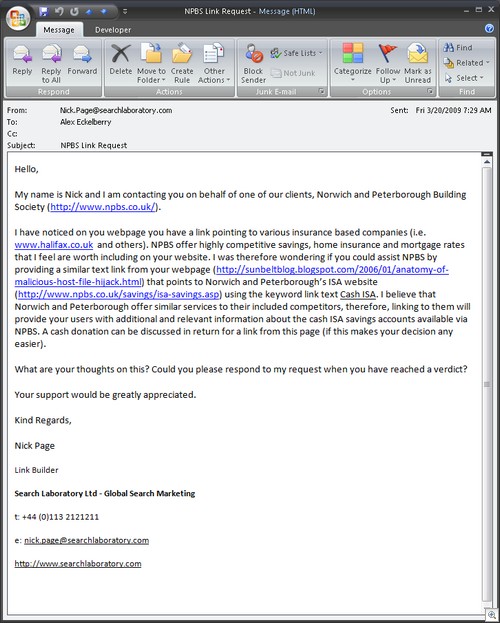
I think this one takes the cake.
From: FEDERAL BUREAU OF INVESTIGATION [mailto:fbisecuritydeptoffice@org]
Sent: Tuesday, April 07, 2009 9:40 AM
Subject: FEDERAL BUREAU OF INVESTIGATION HELP STOP SCAMS ON INTERNET
Federal Bureau of Investigation
J. Edgar Hoover Building
935 Pennsylvania Avenue, NW Washington, D.C. 20535-0001, USA
FEDERAL BUREAU OF INVESTIGATION SEEKING TO WIRETAP THE INTERNET
The Federal Bureau of Investigation (F.B.I) write to you in correspondence to the meeting we recently had with the Federal Republic of Nigeria Government on the ERADICATION of SCAMS on the internet, Federal Bureau of Investigation
(FBI) Washington, DC in conjunction with some other relevant Investigation Agencies like Internal Revenue Service here in the United states of America have recently been informed through our Global intelligence monitoring network that you presently have a transaction with the Central Bank of Nigeria (CBN) as regards to your over-due contract payment which was fully endorsed in your favor accordingly.
After the meeting held on Monday 31st March 2009 at the Bank Auditorium Center , the whole conflict of SCAMS was revealed to us by the Board of Truste of Federal Republic of Nigeria mostly by the three arms of Government.
(The Judiciary, the Legislature and the Executive).
These three arms of Government has made us realize that the rampad of SCAMS over floating around the United State of America and some other part of the world was been set up by the root of some CBN Ex-Workers that have been suspended for sometimes due to their dubious characters of initiating people to impersonate the Government Workers to receive peoples hard earn money from them, mostly with the Executive Governor identity.
For these reasons, the Central Bank Executive Governor was invited to this office to defend the allegation against Him while he made complain that his office was not in charge of foreign transfer of funds, that the accredited office was Federal Ministry of Finance Department (FEDMINAP) in person of (Rev.Paul Badmus) as the Accountant General in charge of all foreign transfer payment files.
They also told us that the only problem they are facing right now is that some unscrupulous element are using this project as an avenue to scam innocent people off their hard earned money by impersonating the Executive Governor that is why the Federal Government has appoint Rev. Paul Badmus as the Payment Director of the Central Bank office.
The Federal government of Nigeria has approved that all overdue outstanding payments must be Paid on OR before 25th, April 2009, for the preparation of their next category to be paid which might leads to recalling of funds back to the Bank Treasury.
Meanwhile, we are also informed that a Man with an America passport number
(3028882234) came to the Central Bank affiliated bank office in U.K few days ago with a letter, claiming to be your true representative.
Here are the man informations bellow:
Name: Denis Marion
Bank Name: City Bank
Bank Address: Arizona, USA
Account Number: 6503809008.
INSTRUCTION/WARNING FROM ROBERT S. MUELLER III.
NB: You are urgently advised to please reconfirm the following to the Office of the Accountant General, as a matter of urgency if this Man is from you so that this office will not issue your fund and be held responsible, If this man isn’t of your true representative, you are requested to contact for your inheritance claim valued of US$12,500,000.00M (Twelve Million, Five hundred thousand United States Dollars)only will be remitted into your nominated bank account.
1) Your full name.
2) Phone, fax and mobile #.
3) Residential address.
4) Company name, Office position and Company address.
5) Profession, Age and marital status.
6) Working I’d / Int’l passport.
And should incase you are already dealing with anybody or office claiming to be from the Central Bank of Nigeria, you are further advised to STOP further contact with in person from africa in your best interest and then contact immediately the real office of the Central Bank of Nigeria (CBN) only with the below information’s accordingly:
NAME: REV. PAUL BADMUS
OFFICE ADDRESS: Central Bank of Nigeria,
Central Business District,
Cadastral Zone,
Abuja, Federal Capital Territory,
Nigeria.
TEL: 001234-01-4328033
0012347032032230
Email: paulbadmus_desk@live.com
IMPORTANT NOTICE.
Note: we are on investigation and security watch over any message with Central Bank, to benefit the satisfaction of all the United States Citizen by seeking to wiretap scams on the internet with the help of Nigeria Government and also with the assistance of all United states Citizen, by listening to the instructions we give out to avoid falling for SCAMS on INTERNET.
All modalities has already been worked out even before you were contacted and note that we will be monitoring all your dealings with them as you proceed so you don’t have anything to worry about, All we require from you henceforth is an update so as to enable us be on track with you and the Central Bank of Nigeria, without wasting much time, will want you to contact them immediately with the above email address so as to enable them attend to your case accordingly without any further delay as time is already running out.
Should in case you need any more information’s in regards to this notification, be free to get back to us so that we can brief you more as we are here to guide you during and after this project has been completely perfected and you have received your contract fund as stated.
Thank you very much for your co-operation in advance as we earnestly await your urgent response to this matter.
Best Regards,
Robert S. Mueller III
Federal Bureau of Investigation
J. Edgar Hoover Building
935 Pennsylvania Avenue, NW Washington, D.C. 20535-0001, USA internet.securitys_federalbureauofinvestigation@live.com