Someone I know and trust has decided to use mailinfo. It’s obnoxious.
Helpful tip: If you want to me to respond to your email, please don’t do this.

Alex Eckelberry
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
Someone I know and trust has decided to use mailinfo. It’s obnoxious.
Helpful tip: If you want to me to respond to your email, please don’t do this.

Alex Eckelberry
Craig Crossman has been kind enough to allow me to become a malware correspondent on his radio show.
Alex Eckelberry
Chances are they spent a good part of the weekend patching…
This patch was a hassle. It’s an emergency patch, it has to be installed asap, but it requires a reboot. Imagine that with a bunch of servers, desktops, without a lot of time to plan… Yikes.
Alex Eckelberry
Multiple vendors’ web browsers are prone a cross-site scripting vulnerability that arises because the software fails to handle specially crafted files served using the FTP protocol.
Successfully exploiting this issue may allow an attacker to execute arbitrary script code in the browser of an unsuspecting user in the context of an FTP session. This may allow the attacker to perform malicious actions in a user’s browser or redirect the user to a malicious site; other attacks are also possible.
PS: Firefox 3.0.1 – 3.0.3 affected. Firefox 3.0.4 is in works.
Signing Off,
Michael St. Neitzel
Thanks to Patrick Jordan for the information.
Zlob Trojan Distributing site:
91.203.92.12 Bsplware. com
91.203.92.12 Softwmpdll. com
Scam Internet Security Page:
91.203.92.12 Safesurfingpage. com
404ErrorpageScam:
91.203.92.12 404mispage. com
Security Guide Scam Page:
91.203.92.11 Screenshortcuts. com
Ad-Server-Gate Pages:
91.203.92.12 Ghjyt. com
91.203.92.12 Bnmhg. com
Protection Center Scam Page:
91.203.92.11 Securesurface. com
Scam Security Toolbar site:
91.203.92.11 Selectedtoolbar. com
IE AntiSpywareStore site:
208.72.168.92 Onlyiesettings. com
Please stay clear of these sites.
Bharath M N
As we march forward inexorably into our technology Bold New World, we find cracks in all parts of the plan, continuing to reveal the maxim that the path to hell is littered with good intentions.
Consider the following bizarre video, on one side promoting the benefits of “Talivans” in reducing speeding accidents, and on the other, showing two clear examples where Talivans caused accidents (because drivers going high speed slam on the brakes). Here, via TTAC.
There’s more, as TTAC says:
A UK Department for Transport-funded report suggests that the panic braking seen in the Norfolk footage may not be an uncommon response. A study of speed camera usage in 29 highway construction zone projects over 450 miles of road from November 2001 to July 2003 showed that accidents increased by 55 percent in the locations where speed camera vans were used. The DfT unsuccessfully attempted to prevent publication of the report.
Speedcameras.org even has a slightly risque print campaign on the matter. And there’s even a controversy as to whether or not the speed cameras, errr, actually work correctly.
Alex Eckelberry
Shelly Palmer blogs about privacy and Twitter, as regards marketing companies mining the data:
But those systems pale in comparison to the kinds of data we’re giving about ourselves on personalized media like social networks and Twitter. Imagine if through some sort of Semantic Web application a company could glean information not only on what info you offered, and tags you’d left, but also the things you were passionate about, what you’d been writing and saying, asking for and complaining about. Imagine if the company could handle the complaint or fuel the delight of that passionate, highly involved (ok, “engaged”) fan — how much might she crow about you, then, an not only increase her loyalty but also help spur others into the fold?
Then a report that aspiring applicants to colleges may be using Facebook to sabatoge in other potential classmates.
And finally a report (in Hungarian, alas) reporting an “exploit” in Twitter. It’s really simple, actually. Apparently subscribing to a feed of a friend of a person who has a “protected status” (meaning, only friends can see what they’re saying) provides a view into the “protected” conversation. A yawn compared to the current top-of-mind exploit, but it’s worth noting, in case you haven’t noticed: There is no privacy.
Alex Eckelberry
Correction: There is a worm component. (Yes, the trojan itself isn’t a worm. But that overlooks the behavior of a dll, a dll dropped by Gimmiv, which is a worm. Now, that doesn’t mean we’re at a SQL Slammer type worm stage. This Trojan has to get into a system. But, nevertheless, I stand corrected.)
There’s some misinformation going on out there that there is already a worm targeting MS08–067. We haven’t been able to verify this.
Looking at the particular trojan that blog mentioned, it seems to me to be a trojan related to the MS08–067 attacks that I took a quick look at this morning:
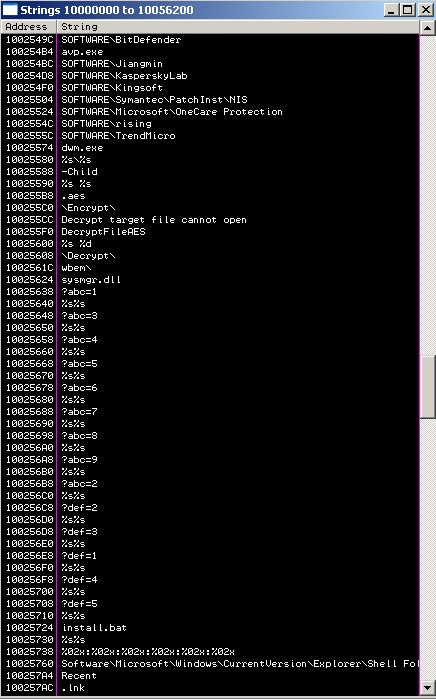
You can see it targeting antivirus vendors like Bitdefender, Jiangnmin, Kingsoft, Symantec, Microsoft, Rising and Trend.
And in this screen, you can see some pretty ugly stuff. This is not a nice trojan:
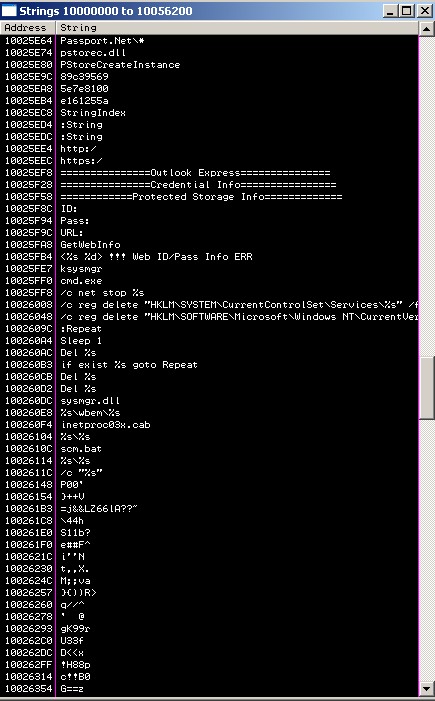
At any rate, I don’t want to de-emphasize the absolutely vital need to patch systems ASAP.
And, we would make an educated guess that a worm will hit soon (maybe in the next day or so).
Alex Eckelberry
I was stuck in meetings today and didn’t get a chance to write much more than I did earlier.
Just some quick notes on MS08-067.
– We have samples in-house of the trojans in-the-wild that are being used in targeted attacks, taking advantage of this exploit. These are currently only targeted attacks, not being used broadly by malware authors.
– It is not a light thing. The urgency is quite real — unpatched, you’ve got the spectre of another SQL Slammer, Code Red type of scenario if the malware writers create a worm. The other issue with this patch is that it affects a broad number of systems (XP, Windows 2000 and 2003 — the Vista/2008 platform isn’t at the same level of risk).
– It is an extraordinary event that pushes Microsoft to do an out-of-band update. This is a big deal for them — each update is tested on a vast number of machines. It underscores the potential seriousness of this vulnerability.
Patch like hell and let’s hope everything will be ok in the morning.
Alex Eckelbery
After moving to moderation (because of so much spam) I, well, err, accidently deleted a number of comments. Some are already suspecting a conspiracy. But no, that’s not the case. Just a simple screw-up.
If you’ve posted a comment in the past couple of days and you see it mysteriously gone, feel free to repost. My apologies for the error.
Alex Eckelberry
VOIP security is an issue, but it is often overhyped (and often, misunderstood). However, “security breaches” in this area should be analyzed carefully to understand the potential issues as VOIP is rapidly rolled-out.
In September, “attacks” against German VOIP users were first reported by Heise in Germany. This attack didn’t get much attention in the US, which is understandable, since almost all of the coverage was in German.
It’s clear that the motive behind these attacks was to check for unsecured gateways. As to why they were checking for unsecured gateways, it seems reasonable to assume that the attackers were looking to make free calls (that conclusion was reached by HoneyNor for a similar series of attacks in Norway). Or, as VOIP expert Klaus Darilion said after analyzing the attack “I only saw the single INVITE request, thus the final PSTN target (Jamaica, Malaysia, …African destination are also often used) was not visible for me. But once the attacker found an “insecure” gateway – that means the gateway forwarded the request, the attacker can use it for making phone calls into the PSTN.”
However, safeguarding against such attacks isn’t that hard. Darilion has provided an excellent writeup on what happened, along with tips on how to protect an organization. I would recommend reading the “Countermeasures” section of his writeup for a fairly simple set of steps to protect your organization. Also, there’s more discussion on this issue at VOIPSEC.
Alex Eckelberry
Nifty, the Windefender 2008 has a pretty little sidebar to add to the illusion that it’s a normal product (Windefender isn’t itself a new rogue security program, we just thought the sidebar was something interesting).
Along with the usual fake scanning application:

Sites Associated:
207.226.179.163 webscanneronline. com
207.226.179.163 internetscannerlive. com
207.226.179.162 win-defender. com
207.226.179.166 update1.win-defender. com
207.226.179.148 registerwindefender. com
Fake 404 page pushing scam:
dns-problem. com/?sid=ar&gid=ma
Online scanner scam
update1.win-defender. com/scanner/scanner.php
Running the free VIPRE trial will remove this threat from a computer.
Alex Eckelberry
(thanks, Patrick Jordan)
AntiSpyware XP 2009 is a clone of XP AntiSpyware 2009 rogue security application. This rogue belongs to WinReanimator family.
AntiSpyware XP 2009 also drops a set of fake files into both windows and system32 folders.
Sites Associated
92.48.201.43 Antispyware-xp2009.com
92.48.201.43 Asxp-2009.com
92.48.201.43 Asxp2009.com
92.48.201.44 Antispywarexp-2009.com
92.48.201.44 As-xp2009.com
92.48.201.46 Antispyware-xp-2009.com
92.48.201.46 As-xp-2009.com
216.195.41.59 Downloadsoftindex.com
216.195.41.60 Downsoftindex.com
216.195.41.61 Downsofthome.com
216.195.41.62 Downloadsofhome.com
216.195.41.63 Updatesofthome.com
Bharath M N
 Something on the social side today:
Something on the social side today:
Happy birthday to Alex Eckelberry, Amy Rolak and Melissa Aull!
We’re glad you showed up for work today and on Behalf of Sunbelt Software enjoy your very special day. All the best for you.
PS: Alex, stop complaining, you’re not going to die very soon and according to a office voting you still look young and handsome.
Signing off,
Michael St. Neitzel
Pro Antispyware 2009 is new rogue clone from WinSpywareProtect family.
Thanks to Patrick Jordan for the information.
Sites Associated
216.195.50.87 Proantispyware2009. com
78.157.142.76 Scan. Freeantispywarescanner. com
78.157.142.81 Files. Proas2009dl. com
78.157.142.88 dl. Proas2009storage. com
Bharath M N
Richard Stiennon sent this one over to me.
It’s not malware, per se. But it’s completely fraudulent.
[4:40:27 PM] Update Alarm ® says: WINDOWS REQUIRES IMMEDIATE ATTENTION =============================
ATTENTION ! Security Center has detected malware on your computer !
Affected Software:
Microsoft Windows Vista
Microsoft Windows XP
Microsoft Windows 2000
Microsoft Windows NT Server 4.0
Microsoft Windows Win98
Microsoft Windows Server 2003Impact of Vulnerability: Remote Code Execution / Virus Infection / Unexpected shutdowns
Recommendation: Users running vulnerable version should install a repair utility immediately
Your system IS affected, download the patch from the address below !
Failure to do so may result in severe computer malfunction.http: //www. registryscan. cc/?q=scan
The page goes to a typical fake scan page.
However, unlike many rogues, it won’t download anything without payment first.
Complete fraud. Server hosted in the state of Washington. Anyone listening?
Alex Eckelberry
Cooperation improves phishing takedowns. No surprise.
When we examined our data more carefully we found that we were receiving “feeds” of phishing website URLs from several different sources — and the “take-down” companies that were passing the data to us were not passing the data to each other.
So it often occurs that take-down company A knows about a phishing website targeting a particular bank, but take-down company B is ignorant of its existence. If it is company B that has the contract for removing sites for that bank then, since they don’t know the website exists, they take no action and the site stays up.
Since we were receiving data feeds from both company A and company B, we knew the site existed and we measured its lifetime — which is much extended. In fact, it’s somewhat of a mystery why it is removed at all! Our best guess is that reports made directly to ISPs trigger removal.
Link here.
Alex Eckelberry
(thanks, Jose)
Innovagest 2000 group comes up with couple of new rogue security applications.
Spy Protector Home page
208.85.178.140 Spyprotector. org
Fake/Scare scan page used by Spy Protector
208.85.178.140 Win-security-scanner.com
Security 2009 Home page
208.85.178.140 Security-2009. com
Fake/Scare scan page used by Security 2009
208.85.178.140 Security-center-scanner. com
Detection by existing antivirus engines on these rogues is really poor.
Bharath M N