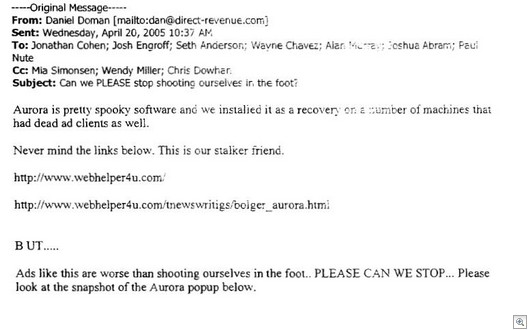
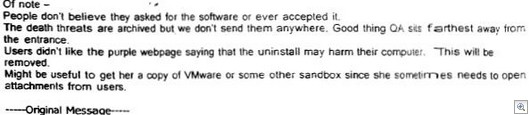
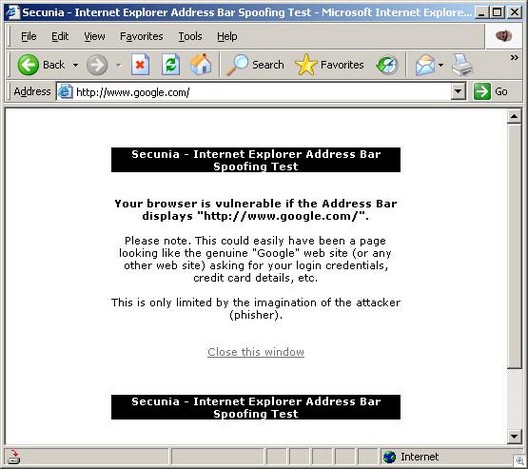
CastleCops and Sunbelt Software are announcing a new anti-phishing community, the Phishing Incident Reporting and Termination (PIRT) Squad. This will be a community at CastleCops solely dedicated to taking down phishing sites. It’s the first public takedown community that I know of, and we are going to start nailing these sites. You can read the press release here. Zdnet article here. You can register to help us here.
The PIRT Squad works as a complement to existing organizations such as the Anti-Phishing Working Group (APWG). The primary difference between PIRT and other organizations is that PIRT is focused solely on aggressively terminating phishing sites. PIRT will work with other security organizations and, if necessary, law enforcement, to provide information for security and forensic analysis.
With this new service, you can report a phish via email or through a web tool. And we’re recruting volunteers to help, too.
But here’s a little background: A while back, Paul Laudanski and I worked together to shut down a phishing site on a financial services company. What did we do? We called them aggressively by phone. We contacted their ISP. We contacted the brokerage firm they used to clear their orders. In just a few hours, the thing was shut down.
This got us talking about the problem of phishing. Very few people report these phishing sites immediately and get them shut down. There’s a lot of experts involved in phish fighting, but they’re primarily dealing with the important security research and forensics angle of the business.
There are companies like Cyota, who contract with financial institutions to protect them from phishing, and they do takedown. Maybe their clients’ sites get taken down. But those who aren’t their clients? What happens?
This situation brings to mind those old TV shows, where a camera crew would have someone pretend to break into a car on a busy street, and no one around would call the cops. It’s not because no one cared, it’s because all the neighbors assumed someone else must be calling. So, no cops were called.
Well, it’s a relevant analogy for phishing. There’s an obvious solution to shutting down a phishing site that many people don’t realize they can do: Contact the site or the ISP or the compromised siteowner In my experience, by aggressively going after phishing sites, you can shut down a significant portion of these sites — perhaps 40% or more — by simply taking action. This may not seem like a large number, but it’s pretty significant if you realize how many people you can help.
I’ve been testing this over the last couple of months: From time to time, I’ll contact someone related to the site to let them know that their site is being used for a phishing scam. In a fairly significant number of cases, I’ve been the first and possibly only one who ever contacted these people. It’s usually something that only takes me a few minutes, but it is effective in a large number of instances.
You see, most phishing operations run off of an innocent compromised site. Phishers, for obvious reasons, don’t want to let the world know who they are, so they find sites with poor security (almost always Apache-based sites that have poor configurations or old Apache versions), hack in, set up shop and do as much business as they can before they are shut down.
This even occurs with keylogging operations. Recently, we came upon an elderly lady running a site about flowers who had a full keylogging operation running off her site. Sending her emails was ineffective, so I simply looked up her name using whitepages.com, called her personally and told her what was going on. We helped her through the process of shutting down the compromised portion of her site, getting things back in place, and now a few less people will be affected by this keylogger. And just this past weekend, I worked on a takedown of a real-estate site with the zero day exploit. I was the first person to contact the realtor, and she took fast action to fix it. So one person can make a difference.
And that’s why Paul and Robin Laudanski and I decided to start PIRT. And we’re recruiting volunteers. Paul has even created a tool, Fried Phish(tm), which you can use to make phishing reports. Join here. An introductory Wiki (a work in progress) is here.
You can help fight phishers as well, with just a basic knowledge of how the Internet works. If only 10% of the people who read this blog reported one phishing site a day, it would actually make a dramatic impact.
So join Paul and me and become a Phishing Terminator. Click here.
Alex Eckelberry
Digg this story.