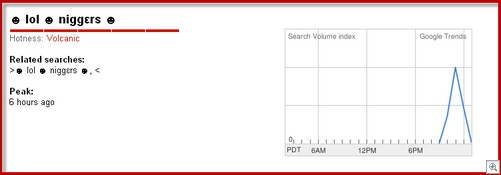
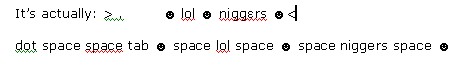Search engine optimization (SEO) poisoning is nothing new, but here’s a nasty new twist. Early this morning someone apparently found a way to game Google Trends, sending an ugly racist string to the number one position on the “Hot Searches” list.
A post on the 4chan.org boards seemed to hint that someone, somewhere discovered something: “omg it works guyz every time”
4chan apparently took down a number of posts that contained the string.
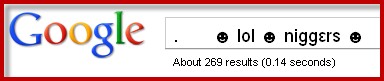
By about 9 a.m. (EDT) Google was showing 269 hits for the string, many of them seemed to be sites that scrape Google Trend Hot Topics.
Searching the Google hits for the string didn’t really turn up much about its origin, but it did show some interesting SEO techniques in which web site owners scraped Google’s Hot Searches to attract visitors to their sites. This has the potential of amplifying any nastiness that anybody can get into the trends.
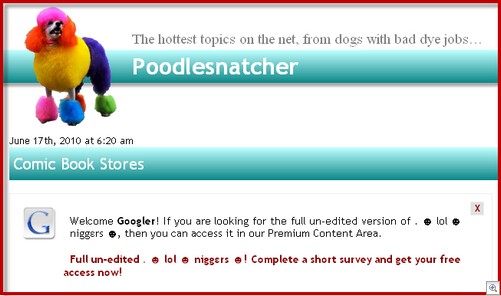
This site apparently scraped Hot Searches then told visitors they could see the “full un-edited version” by clicking on a link which took them to an anchor on the same page – thus getting (at least) two clicks for the price of one.
http://www.poodlesnatcher.com/comic-book-stores-4841/
This appears to be just nasty old fashioned hacking for (racist) kicks, however, the same mechanism could be used to pass along a link to sites with malicious drive-by downloads.
Bottom line: think twice when you click on Google’s Hot Topics.
Tom Kelchner