On the heels of the release of the new consumer version of CounterSpy yesterday, the Enterprise version was officially released today.
Alex Eckelberry
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
On the heels of the release of the new consumer version of CounterSpy yesterday, the Enterprise version was officially released today.
Alex Eckelberry
The indefatigable Rick Green of the Hartford Courant blogs about Julie Amero’s ongoing plight.
Alex Eckelberry
I hope it was not felt that my post yesterday on Fuse Kit (being used by malware authors) would in any way impugn this very cool, very useful program. This has gotten some attention since SC Mag wrote a story on the general subject of malvertisements.
The author of Fuse Kit, Moses Gunesch, sent me an email today, understandably not to happy:
Fuse Kit is an animation system for Flash. It cannot be used for malicious purposes, in fact it has no networking code in it at all. The fact that this horrible malware person used it in a banner ad is entirely incidental (Fuse is used in banner ads for animation purposes).
Sandi Hardmeier’s mirrors these sentiments on her blog here.
Fuse Kit is a very cool, useful tool that happens to be used by malware authors to create animations in malicious advertisements. It’s about the same as saying that MS Paint is being used by the malware authors — it may be being used to create the animations, but it’s not the source of the scripts, the network activity, or anything that would directly contribute to the spawning of these ads.
Alex Eckelberry
Today, we officially released the consumer version of our all-new CounterSpy 3.1 product. (It’s actually version 3, but due to having to align our version numbering scheme with our Enterprise version, it was released as 3.1).
This is a major upgrade to CounterSpy. All-new threat engine, all new technology — completely re-written from the ground-up for fast performance. As always, none of our products bundle toolbars, our trial versions are full versions, and we provide free support.
Give it a whirl and let me know what you think. You can always email me your opinions directly.
Users of VIPRE will find the interface familiar — CounterSpy is simply a sub-set of VIPRE, excluding features specific to viruses. CounterSpy customers can upgrade at anytime to the VIPRE product for a small cost.
One small note: Unlike a “silent” preview edition posted last week on our website, this version comes with the On Access feature of Active Protection disabled by default (it can always be re-enabled). This feature will invariably conflict with some antivirus programs’ real-time protection, and since almost everyone runs this product alongside their existing antivirus product, it’s not necessary. A further explanation is in our video tutorial here.
Full company propaganda here.
Alex Eckelberry
Fuse Kit is a cool utility to create animations in Flash. Unfortunately, it’s popular with malware distributors, who are using it to create malicious advertisements.
These malicious advertisements get served on sites — even mainstream sites. They push malware. (Just to make sure there’s no confusion, this is not a drive-by exploit. Typically the user will see a fake “system scan” message that “Your system is infected!”. If the user actually believes it and clicks “OK”, and then downloads and installs the “security software”, the infection will occur. However, it’s not to lighten the effect — it’s very devious social engineering.)
More from Sandi Hardmieir, who has been doing just about the best job of tracking these:
I am seeing reports of the malicious redirects remaining dormant for a week before visitors to victim web sites are hijacked and redirected to fraudware sites. Web sites simply *must* increase their due diligence checks with any new advertiser. It is going to take time, and it is going to cost money, but what alternative do web sites have if they want to protect and keep their readership, and if they want to avoid the inevitable end result of malvertizing, which is that more and more of visitors to their sites are going to block all advertising.
That being said, it is not all doom and gloom – not yet. There is something that you can watch out for, even if a particular advertisement passes the adopstools test, and passes other security tests. You see, even if the hijacking behavior of a malvertizement is “dormant” there are still subtle hints of trouble ahead that you can see if you know where to look.
For example, in the case of the newsweek malvertizement, by leaving network traffic capture software (or Fiddler) running when the advertisement displays on a web page, we see that the following URL is touched – adoptserver.info/state_.gif?url=[removed] and that the malvertizement is the referrer. adoptserver.info is a known “bad actor”. Its name servers are supplied by the now infamous “estboxes”. Any advertisement that leads to such a domain being touched should be suspended, no questions asked. Don’t wait for the complaints to start.
More here.
In an email this morning, Sandi told me that she’s “very worried” about these latest malvertisements.
Alex Eckelberry
Pretends to be Windows Media Player.
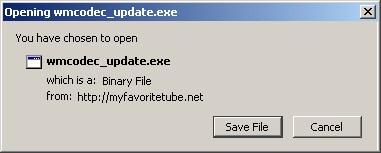
Installs a zlob fake codec with fairly poor antivirus detection, then installs the current plague, Antivirus XP 2008.
(I admit, commenting on one of these fake codecs/rogue security products is kind of like discussing a single bullet in the middle of a full-blown war.)
Alex Eckelberry
Our good friend Chris Boyd continues to report on some baffling things.
First, another site with pirated movies pushing Zango. He’s starting to suspect that there’s a ton of these types of sites pushing Zango.
But then, the mother of all confusing popups when you try to cancel Zango. It’s the first he’s seen of this.

It’s worth noting that the indefatigable Ben Edelman complained earlier about confusing Zango button placement. But this latest popup tops his earlier complaint.
Alex Eckelberry
PaperGhost goes to movietvonline(dot)com, gets pushed to install Zango, and gets to watch a horrible pirate of The Dark Knight.
The story here.
Alex Eckelberry
Antivirus XP 2008 delivers a malware certed from GlobalSign. I’ve sent them an email.
Alex Eckelberry
Off topic, but the predictions of this blog — that the oil prices were a speculative bubble soon to burst, and that the dollar would rally — have come to pass.
(Ok, ok! I’ll get back to writing about security issues.)
Alex Eckelberry
Jeff Lawson blogged last week about problems with a TRUSTe certified site, iGive.
Briefly, Jeff found a number of problems with iGive’s security model:
While TRUSTe did ultimately take action on Jeff’s security issues (and according to Jeff, they did understand the issues and did communicate to iGive), Jeff adds some additional color in an email exchange:
At least in my case, TRUSTe was effective in getting some action from iGive, after months of inaction after attempting to work with them directly. TRUSTe’s staff were able to understand the seriousness of the issues and made efforts to reproduce my claims before passing them on.
My main complaint with TRUSTe is with the fact that they intentionally avoid taking any role in auditing their member companies, even at the most superficial levels. I don’t believe TRUSTe would have even recommended that iGive conduct their own general security audit if I hadn’t suggested it. If TRUSTe doesn’t want to take the responsibility of performing security audits, perhaps they should place a membership requirement for periodic external reviews by a designated security firm. Watchdog complaints seem to unreasonably require the reporter to satisfy the burden of proof upon the reporter before any action is taken.
The lack of full transparency around the corrective actions done is a little disappointing, though probably not unreasonable since it usually involves the PR image of their member companies.
You can view Jeff’s blog post here.
TRUSTe recently went for-profit, which only opens the door more potential weakness in the face of a paying client. On the other hand, they did hire the highly-respected researcher Sandi Hardmeier as one of their online watchdogs/security researchers — something which shows an increased vigilance in policing their certified companies.
(Now, in fairness, I understand that security audits may not be economically feasible at their current rates, but perhaps there are other methods — like having a TRUSTe “Audited” seal, denoting a higher level of security in a site.)
Alex Eckelberry
The GUI is similar to XPAntivirus, however it’s a different program.
Typical fake scan page (and notice the fake system tray message, actually in the browser).
Almost non-existent detection by existing antivirus engines on this one…
Supporting sites:
ia-scanner com
ia-license com
ia-payment com
ia-support com
Alex Eckelberry
(Thanks Bharath and Patrick Jordan)
A new round of spam pushing fake codecs. Last week we had fake Reuters. Now, we have fake CNN.
That “flash player” is a Trojan and will only make your day decidedly less pleasant.
Alex Eckelberry
We’ll be there exhibiting this Wednesday and Thursday. Feel free to drop by and say hello.
Alex Eckelberry
Power Antivirus 2009, recent entrant to the sleazy fake antispyware world (at power-antivirus-2009 com) started making the rounds late last week.
Incidentally, the installer is signed by Verisign’s Thawte division…
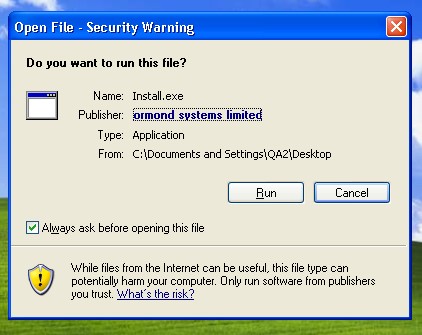
Alex Eckelberry
(thanks, Patrick Jordan)
Chandra will be discussing the Rustock rootkit at AVAR 2008. The subject will be interesting:
Paper title
—————–
What makes the Rustocks tick!Abstract
————-
The Rustock family of rootkits is undoubtedly the most notorious collection spambot rootkits. Rustock A, B and now Rustock.C have invaded the Web chronologically in that order. Each newer variant has evolved with increasing degree of sophistication and complexity. This paper first presents a comparative analysis of the evolution of sly techniques used by these Rustock variants. The comparison includes their mode of infection, explanation of kernel code disassembly for their stealth mechanism, underlying operation and techniques for detection and remediation. Then it delves into a very detailed reverse engineered analysis of the latest Rustock.C variant. The analysis encompasses different phases of its kernel and user mode activity. Specifically, this paper includes explanation of Rustock.C DriverEntry startup code for its multi-layered unpacking routine, well tuned loader, techniques for obfuscation of loaded image, hook initialization routines and several more aspects. In regard to the steady state operation the paper describes its driver dispatch routines and activities of its worker thread that manifest its underlying operation. In addition, the paper also presents some of its new techniques for registry hiding, file system hiding, anti-debugging tricks and revival strategy that all work collaboratively to make it a highly effective spambot rootkit.
Chandra’s become an AVAR regular, having presented at AVAR 2006 (“B-tree with fixed node size and no minimum degree”) and 2007 (“Design of X86 Emulator for Generic Unpacking”). Nice work Chandra.
Alex Eckelberry
Following on the heels of our VIPRE consumer release last week, our enterprise version has now shipped. Hype here, page link here.
It’s been busy around here and I do hope to get back to some more blogging soon. But man… has it been busy.
Alex

Grumpy curmudgeon/extreme luddite Ted Stephens finally indicted on corruption charges.
Alex Eckelberry
(Photo credit)
Not much news to those who track phish kits, but a bit of poetic justice here in this academic paper:
The most recent step in the commoditization of phishing was the distribution of free phishing kits. These kits are actively advertised and distributed at no charge. However, as the economist Milton Friedman would have pointed out [6], there is no free lunch in the underground economy. Often, free phishing kits hide backdoors through which the phished information is sent to recipients (probably the original kits’ authors) other than the intended ones. In other words, far from being a display of generosity on behalf of the authors, free phishing kits respond to rational economical motivations. That is, kits’ authors minimize the effort and risks associated with deploying the phishing site and attracting victims, and maximize their return on investment by harvesting the work of unwitting users.
Link: html, pdf (via John LaCour at Mark Monitor)
Alex Eckelberry