A blog piece in which we discuss one Web site selling subscriptions to information about non-existent security products and a number of others that use the names of legitimate AV products as lures of which the gentle reader might beware.
There have probably been as many scams involving sales of anti-virus security products on the World Wide Web as there have been sales of “prime” real estate (that turn out to be under two feet of swamp water) in Florida.
Alert reader Bharath drew our attention to these.
The site Anti-Virus Review, “The No.1 Anti-Virus Internet Network” claims that it has reviewed anti-virus products and presents its “gold”, “silver” and “bronze” award winners: ViraFix, Antivirus Download and Antivirus-Solution respectively.
These aren’t rogue products. These are AV products that apparently DO NOT EXIST.

(click on graphic to enlarge)
So what are they charging you money for?
Anti-Virus Review explains:
“This website has no affiliation whatsoever with the owner of this software program and does not re-sell or license software. Membership is for unlimited access to our site’s resources. We provide an organized website with freeware, links, software, technical support, tutorials and step by step guides. New computer users should find our services valuable and time saving. If you are an advanced computer user, you probably don’t need our services.”
So they’re saying:: “if you don’t know anything about this stuff, this is the site for you, SUCKAH!”
The main page and pages devoted to the non-existent products are professionally laid out, complete with tables, graphs and the seals of certification agencies such as Virus Bulletin (These guys are NOT listed on the VB site: http://www.virusbtn.com/vb100/archive/results?display=vendors).
ViraFix page

(click on graphic to enlarge)
Antivirus Download claims to have VB100 and other certifications
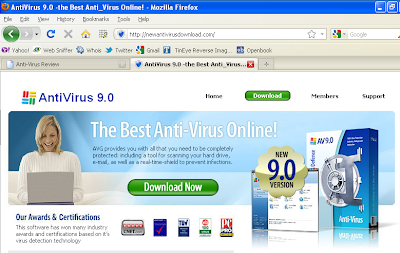
(click on graphic to enlarge)
Antivirus & Security package design has a striking resemblance to Kaspersky’s.
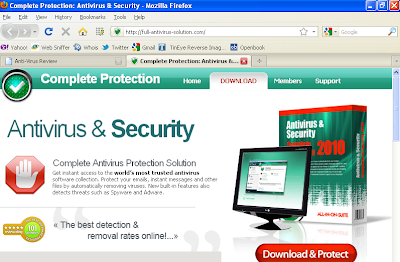
(click on graphic to enlarge)
One especially meaningless graphic shows up on the ViraFix site. We’re not even going to conjecture what this table is supposed to mean other than “we – good, they – not good.”

Another little bit of insanity/inanity lies in the FAQ. The writer uses the name “Antivirus 2010” (We blogged about a rogue by that name in October ) This leads one to conjecture that maybe this is material borrowed from another site out there.
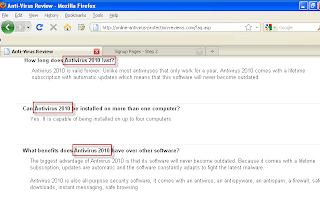
So, to make this long story a bit shorter, these sites all lead to payment pages that look quite similar: “Membership Options and Features.”
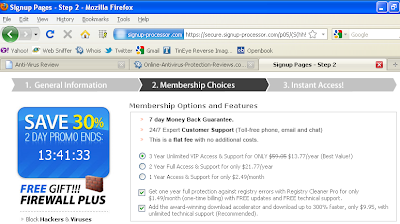
(click on graphic to enlarge)
The site hasn’t been around long either, only since the end of September.
Registrant:
Domains by Proxy, Inc.
DomainsByProxy.com
15111 N. Hayden Rd., Ste 160, PMB 353
Scottsdale, Arizona 85260
United States
Domain Name: ONLINE-ANTIVIRUS-PROTECTION-REVIEWS.COM
Created on: 29-Sep-10
Expires on: 29-Sep-11
Last Updated on: 29-Sep-10
Other sites with a twist: free legitimate AV products (and one not-so-effective one) used as lures
Our friend Bharath did more digging and found that this group, judging by similarities in page design, also have a load of sites that use the names of legitimate anti-malware products from big-name vendors as lures:
Avast
download-antivirus-now.com
antivirus-download-pro.com
antivirus-prodownload.com
Avira
antivirus-pro-suite.com
Kaspersky
full-antivirus-solution.com
Malwarebytes Anti-Malware
antimalware-protect.com
SpyBot (not considered an effective product. VIPRE detects as: Backdoor.Spybot)
search-destroy-protection.com
searchdestroy-scan.com
Ad-Aware
aware-download.com
AVG
antivirus-2010pro.com
antiviruspro-download.com
free-anti-virus-software.com
So, if you’re fixed up with an antivirus solution now, maybe you’ll be interested in some land that’s for sale in a little development we know about over by Okeechobee. This one is going to be hot! These babies are selling like hotcakes! You can flip these and double your money FAST!
Thanks Bharath
Tom Kelchner