The holiday shopping season will kick off in earnest on Friday – named “Black Friday” because that’s the date that many businesses traditionally go into the black for the year.
Another tradition is an uptick in Internet fraud, scams and hacks.
Social engineering will probably be the biggest danger to look for. Just like any other shopping day of the year, if the deal seems too good to be true, it probably is.
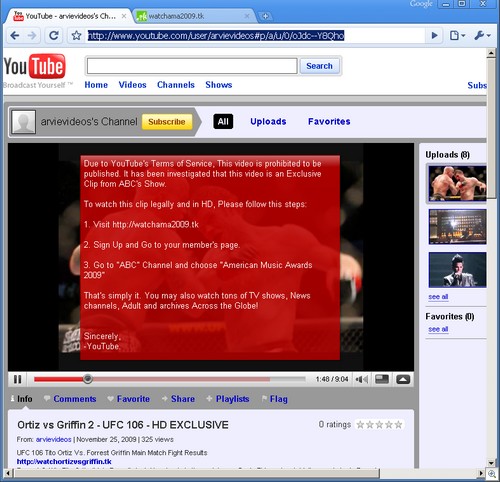
Expect rogue security products to be “on sale” in spam email, messages from social networking sites or web sites. To check if a product is a rogue, just search for its name on the Sunbelt Rogue Blog page here.
Fraudulent sites that are set up to steal your credit card and other identity information are also a serious threat.
Search Engine Optimization techniques will be big this year. Internet thieves will be pushing their sites high into the placement of search engine results. So, if you go looking for something like “black Friday sales” in a search engine, take a look at the URL before you click on it.
I just did it and found one listing with an “.fm” top-level domain. Interesting. Who in the Federated States of Micronesia is holding a major holiday sale? Malicious sites often are registered in such places because of a lack of regulation.
The .cn top level domain is another one to keep an eye out for. It’s the domain for China. A vast number of compromised machines there are used for all kinds of scams.
Another easy trick: do some research and check how long the web site you’re considering purchasing from has been in existence. Cut and paste its URL into http://www.whois.net/ and look for the line “created on…”. If a site has been created in the last few days, be very careful. Legitimate sites certainly can be registered and go on line at any time, however, malicious sites are usually new. They get taken down as soon as their ISPs discover fraud or malware, so, they don’t last long.
Basically, to protect yourself:
— Use common sense: it the deal seems to be too good to be true, it probably is.
— Don’t make on-line purchases from untrusted sites.
— Keep the anti-virus scanner on your PC up to date with the latest signatures if you don’t have the auto-update feature turned on. If you don’t have AV, Sunbelt Software is offering Black Friday and Cyber Monday specials on VIPRE. Read about them here.
— Be sure your Windows operating system has the latest updates.
— Be sure your web browser is updated. It would be best to upgrade to Internet Explorer 8 since unpatched vulnerabilities have been reported in IE 6 and 7 in the last few days.
— Be sure your Adobe Acrobat or Reader are up-to-date. There have been a number of recent vulnerabilities reported in them.
— Don’t make purchases from sites that are advertised by spam email.
Tom Kelchner
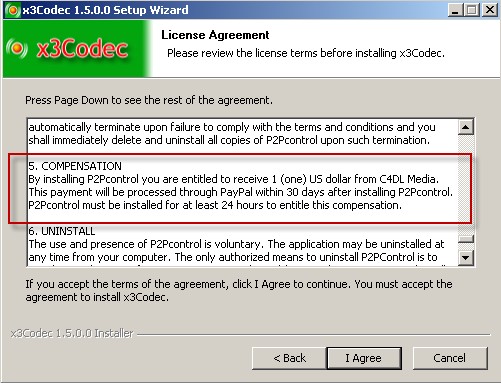
 I’m happy to say that in the
I’m happy to say that in the