(A guest blog by Sunbelt’s Wxpnews editor Deb Shinder)
Computer software is a unique type of product because it’s not really a physical product at all; instead, it’s classified as “intellectual property” – an intangible item that you can’t hold in your hand. You don’t spend your money for the code itself – that remains the property of the developer who created it or (more frequently) the company that paid the programmer(s) who developed it. You simply pay for a license to use the software, subject to conditions specified in the End User License Agreement (EULA).
This has caused no end of consternation among computer users. We aren’t used to buying things this way. A book is a form of intellectual property, too – but we don’t generally “license” the right to read the words; rather, we purchase a physical copy of the book and then we own it and can do pretty much whatever we want with it: sell it to someone else, give it to a friend, leave it lying on a park bench for strangers to find and claim (legally, we are prohibited from doing some things, such as making photocopies of it and selling them to others, but that’s expensive and a hassle so it almost never becomes an issue).
The problem is that the intangibility of software (and some other products such as digital music and movies) makes it very easy and cheap to copy and distribute in bulk. Licensing is one of the only ways the creators can retain control over the fruit of their labors. And licensing in itself is not a bad thing. Most reputable software vendors try to make their EULAs emulate the situation you have when you buy a book; i.e., the terms usually stipulate that you can give the program away, or transfer it to another computer – as long as you remove it from the one it’s on. But you can’t make copies and use it on multiple computers (except in some cases where the EULA allows for you to install a program on two or more computers within your household; this so-called “family licensing plan” is becoming more and more popular).
In theory, this prohibition on making copies is no different from the copyright laws that prohibit photocopying a book. In practice, it feels more restrictive because of the ease and convenience with which you could, technically, make such copies. Folks argue that “I can loan my book to someone else if I want.” And indeed, there’s nothing in most software licenses that keep you from loaning your computer to someone else so they can use the software. What you can’t do is “loan” them just the software without the computer – as you can’t loan someone the words without the physical book you bought (by photocopying those words).
It gets tricky, though, when some companies start to sneak more and more restrictive terms into the EULA. And “sneak” is applicable here because, when you buy boxed software in the store, you’re actually unable to read the agreement until after you’ve paid for the product, taken it home and opened the box (not that most people read it, even then). For an interesting discussion of some issues pertaining to EULAs, click here.
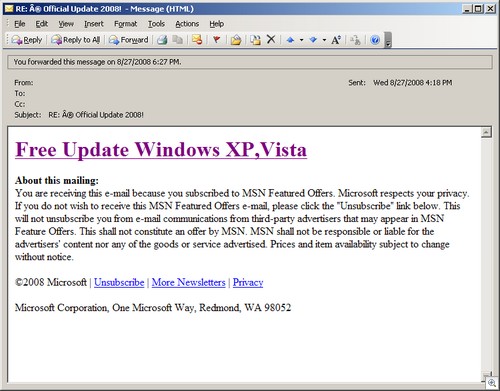
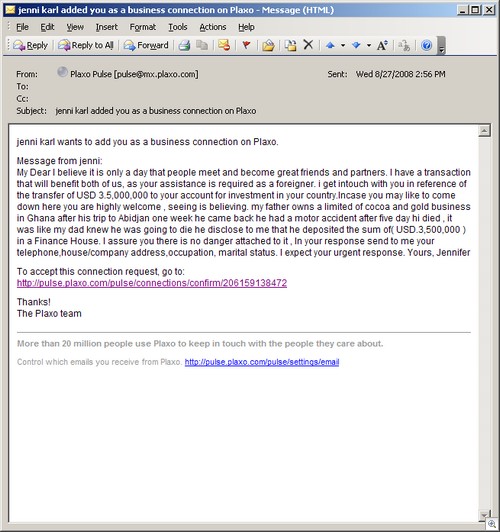
We’ve talked about EULA terms here before, so we won’t go into that in detail. Instead, I want to discuss some other questionable business practices that we sometimes run into when dealing with software companies. Many of these are made possible (or at least made easier) due to the way much software is sold today – paid for and delivered over the Internet rather than bought in a box at a store. And some of these practices are by no means unique to software companies; they’re the same unethical practices engaged in by businesses of all kinds that participate in “remote” transactions, whether over the ‘Net, over the phone or through the mail.
Whenever you give a company your credit card number, there is a risk that they will use it in ways you didn’t intend. One problem encountered with the new subscription based software services (and one reason many are wary of them) is the difficulty of terminating a subscription. You sign up for a year and pay by credit card. At the end of the year, the company automatically renews your subscription and charges you for another year, whether you wanted it or not. Here’s an example of such a complaint against one software company.
(In fact, this is common practice for many businesses. I ranted have ranted long and often about security alarm monitoring services that contain a contract clause stating that unless you cancel the contract within a short window of time prior to the end of your three year contract, it will automatically renew (and obligate you to pay) for another three years. Some states (New York is one) have passed legislation to ban these automatic renewal clauses and I am currently trying to convince my own state representatives to do the same).
Companies that embrace the automatic renewal practice argue that they do it for customers’ convenience. They say if they didn’t, you might forget to renew and then you would be without the service. This might be okay if, when you initially sign up, you select an option to automatically renew (but in my opinion, locking you in to another three years of service as the alarm companies do is never okay). We’ve set up a poll to ask readers what they think about this practice as it pertains to subscription software. Please let us know your opinion on this by voting in the SunPoll.
Then there are marketing practices that may not be blatantly unethical, but are extremely annoying to customers. For instance, with many companies that sell business-oriented software, finding out what their software costs is like pulling teeth. I guess it’s a case of “if you have to ask, you can’t afford it,” but it really makes it difficult to compare different products. If I know a particular software package costs $15,000, I’m not going to waste my time evaluating a trial version of it for my small business. If it costs $1500, that’s a whole different story. But some vendors seem to hold their prices as closely guarded secrets.
Some won’t even let you download a trial version without making a sales pitch to you over the phone. Tom recently clicked a “Try it now” link for an enterprise level virtual appliance software package, which took him to a form to fill out. He expected to receive a link to download the trial; instead he got email telling him that they would have to contact him by phone in order to get the evaluation version. Needless to say, he didn’t evaluate that package (and it won’t get his recommendation or even consideration). What if you have total hearing loss or can’t speak due to a larynectomy? Does the company discriminate against disabled persons by not allowing them to evaluate the software? An extreme question, perhaps, but is it ethical for a company to advertise a free trial and then hijack you into listening to a high pressure sales pitch?
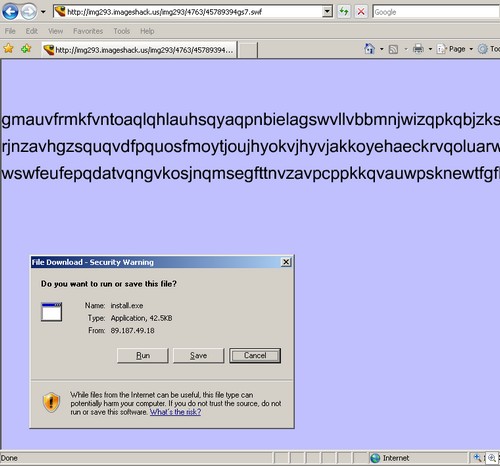
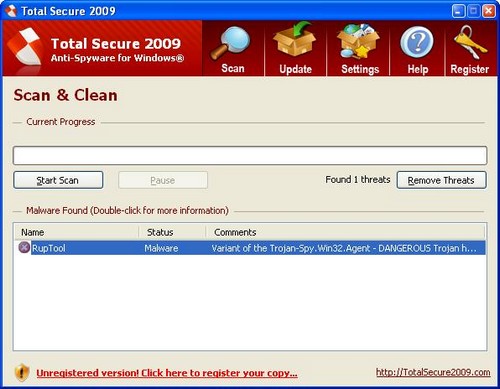
When you think about it, software makers have a tremendous responsibility and hold a position of trust with their users. Most customers are not very technically savvy and must trust the software company that its software not only does what it claims to do, but doesn’t do other things that the customer doesn’t want. A program that you install on your computer can be coded so as to create a “back door” that will allow the programmer to get into your system and take control of it. This is often the basis of Trojans and other malware, but the capability can be written into almost any software. Every time we install a program, we’re trusting that software vendor to be ethical.
What unethical practices have you encountered in buying software? Share your experiences and opinions.
Deb Shinder