Press release here, brief here.
Alex Eckelberry
The Great Years: 2004-2010
We’ve seen hacks on iPowerWeb servers before. Now there seems to be a fresh rash of them. All of these sites are hosted on iPowerWeb-related servers (which include Endurance International Group and Bizland). And all of them have a similar pattern.
Examples:
Generally, these links redirect to porn:
More hacked sites:
nvvam.org
orda.org
chnetwork.org
ifess.org
vraweb.org
spt.org
chnetwork.org
limarc.org
atcsd.com
123child.com
planetarium.net
kci.org
icat.org (not porn, but search redirects)
It’s a DNS hack (very much like what occurred in the past):
| 111.pornsites2703.planetarium.net | |
| Answer records | ||||||||||||||||||||||||||
| name | class | type | data | |||||||||||||||||||||||
|
111.pornsites2703.planetarium.net planetarium.net
|
IN | A | 216.130.168.69 | |||||||||||||||||||||||
iPowerWeb isn’t the only web hosting provider to have this problem. At least one site on Cernio (indybay.org), The Planet (ruby-doc.org) and Media Temple (hml.org) is similarly hacked.
However, they pale in comparison to the iPowerWeb problem.
Alex Eckelberry
We’ve just added a Sunbelt Software section on GetSatisfaction. The link is getsatisfaction.com/sunbeltsoftware. This new forum is still in the “experimental” stage for us, but our support staff will be monitoring it on an ongoing basis. It’s brand new, so feel free to get a topic going.
Support personnel here at Sunbelt monitor questions on a variety of public forums, including Wilders (firewall,antimalware, privacy software), CastleCops (CounterSpy, firewall) and Broadband Reports (firewall, software vendors,security). We also maintain our own Lyris list serv for enterprise customers here. Finally, beta version of Sunbelt products are managed at our beta forum.
Alex Eckelberry
On PC Mag’s site:
I really don’t know what to say. It’s astonishing how people’s perceptions of Zango continue to be informed by this sort of post. How exactly does this constitute evidence that Zango is untrustworthy?
Ken Smith
CTO, Zango
Feel free to drop a comment over there if you feel otherwise.
Alex Eckelberry
A new rogue of the Spywareno family: AntiVirProtect from antivirprotect(dot)com.
Patrick Jordan
Sunbelt Malware Research
In case you didn’t catch these earlier at another site, here are some new domains floating around out there doing bad things.
In some cases, binaries can be captured by using the following example format:
roguesite.com/files/get.php?id=538090733
| Created | IP | Site | ||
| 4/29/2008 | 85.255.120.110 | flwplayer. com | ||
| 4/29/2008 | 85.255.118.214 | protectalerts. com | ||
| 4/29/2008 | 85.255.118.34 | toolbarusage. com | ||
| 4/29/2008 | 85.255.116.211 | safehomesite. com | ||
| 4/29/2008 | 216.255.179.243 | getnewfiles. com | ||
| 4/29/2008 | 216.255.179.243 | asearchflame. com | ||
| 4/29/2008 | 216.255.179.243 | asearchpool. com | ||
| 4/29/2008 | 216.255.179.243 | asearchreview. com | ||
| 4/29/2008 | 216.255.179.243 | explorertool. net | ||
| 4/29/2008 | 216.255.179.243 | gateietool. com | ||
| 4/29/2008 | 216.255.179.243 | gatetofind. com | ||
| 4/29/2008 | 216.255.179.243 | homepagerestart. com | ||
| 4/29/2008 | 216.255.179.243 | ieservicegate. com | ||
| 4/29/2008 | 216.255.179.243 | iqsearches. com | ||
| 4/29/2008 | 216.255.179.243 | linkietool. com | ||
| 4/29/2008 | 216.255.179.243 | newuploads. net | ||
| 4/29/2008 | 216.255.179.243 | renewfiles. com | ||
| 4/29/2008 | 216.255.179.243 | searchinggate. com | ||
| 4/29/2008 | 216.255.179.243 | searchthruweb. com | ||
| 4/29/2008 | 216.255.179.243 | shareownfiles. com | ||
| 4/29/2008 | 216.255.179.243 | trysearchhere. com | ||
| 4/29/2008 | 85.255.118.245 | dns404rule. com | ||
| 4/29/2008 | 85.255.118.212 | secureprior. com | ||
Patrick Jordan
Sunbelt Malware Research
Interesting things…
Anime site onepiecehq.com redirects to Zango:
However, if you cancel and then go back to the site, the Zango install magically disappears. This means that claim that you get site access for free by installing Zango is a crock (video).
Another site, userbars.org, also redirects to Zango. However, unlike onepiecehq, you apparently must install Zango to use the site.
Incidentally, there are these two Zango sites floating around, but they appear dead:
findlyrics.powered-by.zango.com
livenba.powered-by.zango.com
Alex Eckelberry
(Thanks, Shane E!)
Some fresh stuff in here, apparently mostly pushing crapware registry cleaners.
70.84.192.228 freeadobes.com
70.84.192.228 updates-microsofts.com
70.84.192.228 updates-microsofts.com
70.84.192.236 free-microsofts.com
70.84.192.236 registry-great.com
70.84.192.236 registrygreat.com
70.84.192.236 registrygreat.net
70.84.192.229 updates-xp.com
70.84.192.229 updatemicrosofts.com
70.84.192.230 microsofts-updates.com
70.84.192.230 updates-all.com
70.84.192.230 updates-microsofts.net
70.84.192.230 update-microsoftes.com
70.84.192.230 update-microsoftes.com
70.84.192.231 www-microsofts.com
70.84.192.232 perfect-uninstall.com
70.84.192.232 uninstall-free.com
70.84.192.233 dellupdates.net
70.84.192.233 updates-os.com
70.84.192.233 updatesmicrosoft.net
Alex Eckelberry
(Thanks, Patrick Jordan)
Sunbelt Personal Firewall 4.6.1751 (known previously as the Kerio Personal Firewall) is now available for download. This version supports Vista and also has a number of under-the-hood improvements.
The download and more information is available from our beta forum here.
Alex Eckelberry
I realized that I inadvertently titled a blog post earlier this month about Google Groups malware links as “Google Pages Porn Malware Invasion Continues Unabated”. In fact, if you read the blog post, you could see I was referencing Google Groups, but simply mistyped the headline. It’s corrected.
Incidentally, this malware infestation is still a problem…
Alex Eckelberry

No, not the Clash song, but I spent the last week with other Sunbelters at InfoSec Europe in London. This trip followed on a trip to DC the week before, and a week in San Francisco for the RSA show at the beginning of the month. I’ve barely been in the office as a result.
Unlike the InfoSec shows here in the US, InfoSec Europe is pretty much ground zero for the security business in Europe (akin to our RSA show in San Francisco, but different than RSA’s historical industry-centric, incestuous flair, where you’re more likely to do a deal with a rival than with an actual customer).
The show is very active and there’s a lot going on there. But in the story-telling tradition of this blog, I’ll expand on the particulars.
I flew in Tuesday morning on the red-eye from Atlanta. My first meeting found me crashed on a couch by my visitor being, in typical British fashion, quite polite at my unshaven, shabby, smelly form.
After that, Charles Arthur at the Guardian was nice enough to meet with me, where he was also, in typical British fashion, quite polite at my unshaven, shabby and smelly form. Arthur is exactly what you’d expect from a Guardian journalist — polite, gracious, and intellectual. Better, he is good listener, and endured my sleep-deprived, caffeine-induced ramblings. In the end, he followed-up with a blog post about porn.
After that, off to the show for another meeting, then walking the show, and then another painful experience attempting to get through a dinner which needs to be purged from memory. The next day I spoke on a security panel at, of all places, the Sophos booth.
The panel was the brainchild of Sophos PR mavens Carole Theriault and Graham Cluley. Fellow panelists were Paul Ducklin of Sophos, Tony Neate of Get Safe Online, Bob Burls, Detective Constable at Metropolitan Police Computer Crime Unit and Ed Gibson, Chief Security Advisor, of Microsoft UK. (Apple was invited but, err, declined.) All the panelists brought their own perspectives to the various security issues. If you were there, drop your comments.
The show itself was a solid mix of security companies, with European stalwarts such as Kaspersky, Sophos and BitDefender intermingled with US counterparts like McAfee.
Is it Florida or London? At Holland Park, with Sunbelters Chad Loeven and Juan Vasquez.
At the end of the day, the folks at Sophos were kind enough to invite the panelists to dinner at Babylon at The Roof Gardens. Wow. The food was spectacular, the company great and the setting beautiful. And, as one would expect from a company based near Oxford, the Sophos folks are polite, gracious, and intellectual. Is there a pattern here?
And, yet invariably, the conversation leaned to the naughty. You see, the restaurant has a peculiar bathroom setup. Everything is normal until you go to wash your hands. Instead of a normal sink, there’s a waterfall. Yes, a waterfall. It’s kind of an odd contraption, where water drips down from a long bar. You put your hands underneath it and attempt to get the soap off (there’s not exactly a high flow of water). However, where things get interesting is that this is a co-ed waterfall — the women’s bathroom shares the same sink, so your fingers sometimes find themselves intermingling with restaurant patrons of the opposite sex (the waterfall isn’t at eye level, so you can’t see the other bathroom unless you really tried). Of course, when I went, Carole discovered I was on the other side and proceeded to splash copious amounts of water on me.
At any rate, the following day was taken up with meetings until finally, we were done and decided to go out to dinner after a typically crowded ride back on London’s Series of Tubes. A pleasant excursion to beautiful Holland Park found us at the Belvedere, an outstanding and reasonably priced French restaurant right in the park. Highly recommended.
The next day I had something close to a Chris Boyd experience (but not nearly as bad). My flight was cancelled, and I had to spend a night in a local hotel at Heathrow. No biggie, I made some great friends (the old “solidarity of shared discomfort” thing) and Delta handled the situation quite well.
Some closing thoughts on London in general: Yes, as I’ve reported extensively on this blog, there really are cameras everywhere. Everywhere. Yet I’m not sure everyone really even notices it. Perhaps it’s the “light-dimmer”/”how to boil a frog” effect I’ve written about before. For Americans, the cost of London these days is simply staggering. No news there, but it really hits you when you pay for a cup of coffee with practically a week’s wages. London streets are immaculate due to copious street cleaning, a nice change from other big cities. And, the London cabs continue to make me envious. Cramped into a beaten-up police auction cab in New York compared to a spacious London cab… I’ll take a London cab any day.
A great city and a great time. And now, I hope to rest my weary frequent-flier legs for a bit.
Alex Eckelberry
We’ve collaborated quite a bit with Bharath in the past and it’s nice to see he’s been blogging about new rogue (fake) security products. If you’re interested in following this area, add his blog to your feed list. Link here.
Alex Eckelberry
(Not to be confused with the legitimate PrivacyWatcher.)
This PrivacyWatcher is a typical highly deceptive rogue security product.
Fake scans scare the user into believing that all kinds of nasties are on their computer, with one scan observed even providing fake pornographic images supposedly “discovered” on the computer.
Alex Eckelberry
(Thanks Bharath)
Back in the fall of 2006, I held a meeting with the senior technical managers of the company to kick off a total quality management effort. While Sunbelt had historically shipped some great products, we all felt we could do better, in terms of how we develop products. 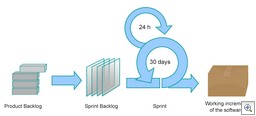
One of the effects of this effort was to move the development organization to the Agile method. (If you’re not familiar with Agile, you can read an overview of it here, but we started by having the teams watch Ken Schwaber’s outstanding talk at Google. I would highly recommend the video if you want to learn about the subject of Agile, Scrum, etc.)
I was originally trained in in the classic “waterfall” model (basically, the standard linear method of specification, development and testing), and I knew there were real problems with it. I was thrilled to see us move to this model.
One of the key tenets of the Agile method is to break projects down into small, manageable parts, referred to as iterations. Agile’s Scrum method is a way of managing these iterations, where they are referred to as Sprints. Simply stated, you break a project down into multiple Sprints, each lasting two to four weeks. Each Sprint has its own burn-down chart, showing the Sprint’s status. (The image to the left, courtesy of Wikipedia, is a diagram of the Scrum process.)
Next to my office is a small conference room. One of the first things I noticed was little meetings occurring in the mornings. These were a Scrum meetings. Each team would work through their sprints, with a burn down chart displayed on a large screen projector. During each Sprint, the burn-down chart shows how well the team is “burning down” through features or bugs. Once the chart goes to zero, that part of the project is done. Meetings are held daily each morning.
I rapidly noticed a difference. Happier, more productive developers, better products, more teamwork, and so on.
We’ve released a number of new versions of our products using this method. However, our upcoming VIPRE is our first major new release that has been developed using Agile.
VIPRE may look simple, but underneath, it’s actually an enormously complex product, with almost 50 subsystems all working in concert. Architectural design was key, as was managing the entire development process.
All of the key components were developed separately, and then were assembled together over a couple of days, much as an aircraft is assembled from its various components. What was quite amazing was the speed of assembly — it’s not normal to have a product of this complexity come together into one whole as quickly as it did. After assembly, it was in a brief alpha phase, and was deemed solid enough to go into beta.
Here’s what’s interesting: In the classic model of software development, you basically have this fight toward the end of every release, where product management, sales and marketing try to negotiate a release date, while QA and dev fight tooth and nail not to release. (Actually, you have fights all the time about all types of things — watch Ken’s video above for an idea as to what goes on. It’s highly educational about what happens behind-the-scenes in a typical software company. Just thank God that software companies don’t make airplanes.)
With Agile, however, we have burn down charts which is the religion. Here’s one of the burn down charts for VIPRE, showing the product’s final Sprint, its beta period. It’s from the 15th of April, and is un-edited:
The green line is open bugs. The blue line is bugs that are fixed, but need to be verified as such (by QA). And the red is the combination of the green and blue.
The red line is our religion. We look at that line and can rapidly predict how the development process is going, and when we’re going to be able to ship. When the red line gets to zero, that’s a point referred to as “zero bug bounce” (“ZBB”) The next version is then release candidate. Then, ideally, release.
This chart, along with a number of others, gets delivered to the team and senior management every single day. We all can get an immediate read as to how the process is going.
Moving to Agile is one of a number of changes we made here at Sunbelt to continue to improve both our organization, and our products. I’d rank it as one of the best things we’ve ever done as a company.
Alex Eckelberry
Maarten Van Horenbeeck did a writeup last year on targeted attacks. Most of it is based on a presentation he gave at 24C3 last December, so it’s somewhat dated right now. He is planning to update it.
However, as a technical read, it’s interesting if you’re following this subject. Link here.
Alex Eckelebrry
We just got this in from a credible source:
I have just been advised by my Dell representative that Dell will be offering XP on Optiplex and Latitude computers through 2011 at no extra cost. Vista media will be available for those who think they might want to install it later on. Vostro computer orders will have the same option at a $50.00 premium.
Note: this means that there will be an extended period of review available for Windows 7 before we have to commit to it.
She told me that the reps are thrilled to be able to respond to the increasing expressions of concern from customers regarding the June 30 cut-off XP date publicized by Microsoft. She also told me that, of the more than 100 customers she has, only one is ordering Vista computers…
Anyone have any confirmation on this rumor? If it’s true, it’s really good news…
Alex Eckelberry
A bit of a self-serving backstory, but it serves as a proxy for what’s happening out there: About a year and a half ago, we released a malware research tool, the Sunbelt CWSandbox. This is a tool which can automatically analyze any file in a safe environment, and give you a comprehensive report as to what the file does. We started by using the tool for our own research, and also licensed it to other companies. In the beginning, practically all of our customers were security researchers.
Then about six months ago, something curious happened: We started getting interest from enterprise and government institutions, and product sales started to climb. I was a bit baffled by what was happening — after all, this is a tool that has primarily been in the field of security research.
It turns out that the reason is simple: Targeted attacks are on the rise.
What’s happening is that organizations get some type of program, or attachment through social engineering. The file is run through a virus scanner, and many times, there’s no or little detection (because it might be a custom-crafted trojan). However, if they have a tool like the Sandbox, they can do a quick, automated analysis and find out if it’s bad or good.
No one has (yet) stats as to how big the problem is. However, there’s an overview of part of the problem in this week’s BusinessWeek, and some other commentary from our friends at F-Secure.
I’ll keep updating this blog as I get more interesting information on this subject.
Alex Eckelberry