Comcast has begun an experimental program in the Denver area to warn customers whose PCs have been turned into spam-spewing bots. The infected ones will see a browser pop-up warning them that their machine contains malware.
I don’t want to sound like a whiner, but why didn’t ISPs start doing this, oh, say, four years ago when the number of bots in the wild exploded?
This is really terrific, Comcast should be commended and I hope other ISP (ALL ISPs) do something similar, but why did it take this long? Spam email, and a whole load of it is from botnets, is now estimated to be near 90 percent of email traffic.
The story on the CNET news site says: “For years, security experts have complained that ISPs are uniquely positioned, and should do more, to help customers combat security problems. But ISPs have been reluctant to assume additional responsibilities that are not central to their core service offering and for which they would then have to maintain a standard, going forward.”
See story here.
Tom Kelchner
Oct. 9 Update:
Brian Krebs, in his Washington Post column “Security Fix” today dug into more details of the Comcast plan, including the possibility of fake warnings. He reported:
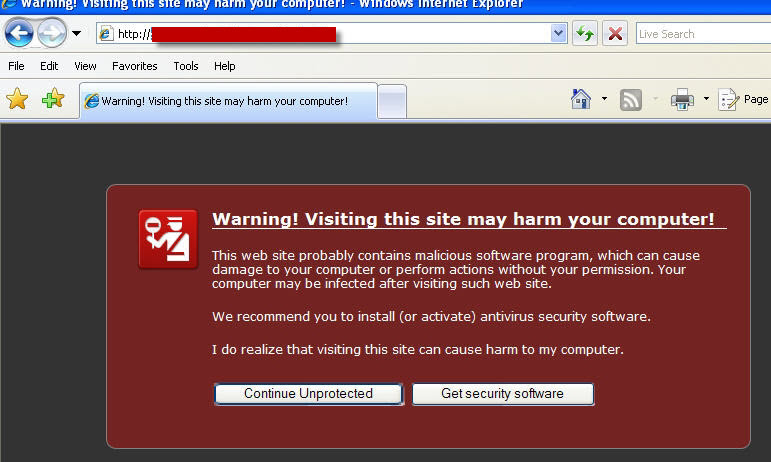
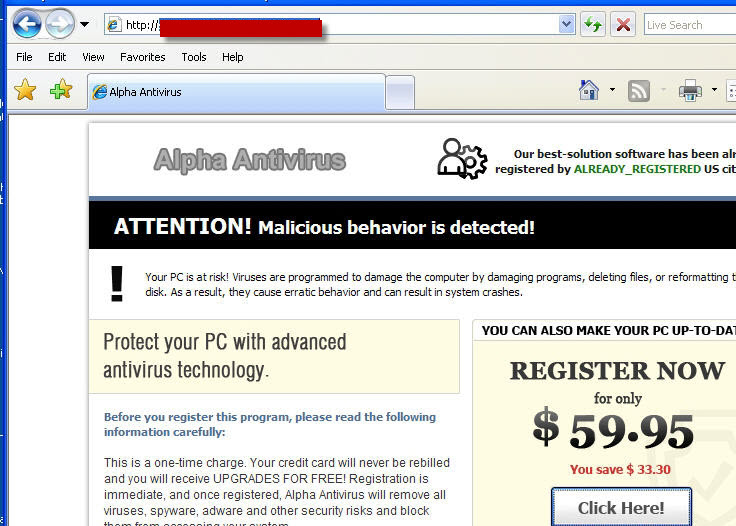
“The primary challenge to this program, aside from actually helping customers rid their PCs of bot infections and keep them clean, may come from the criminals themselves. One of the most persistent threats to Internet users today are rogue anti-virus programs that use fake security alerts to trick consumers into downloading malicious programs or at the very least paying for worthless software.
“(Jay) Opperman (Comcast senior director of security and privacy) said Comcast is attempting to combat this potential scam by including a link in the banner alert that explains “How do I know this notice is from Comcast?” Among the answers they will list is that Comcast will be sending affected users an e-mail alert at their primary account at the same time as the browser alert is displayed.”
See story here.