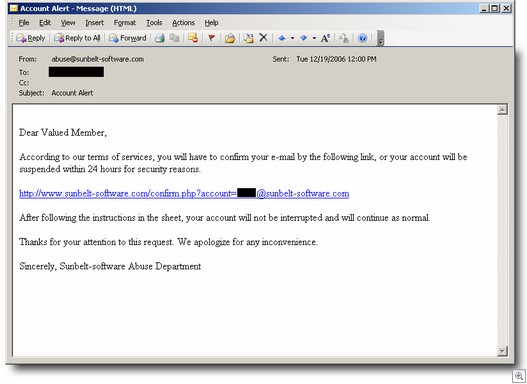
 How to use the Networking Tab in Task Manager
How to use the Networking Tab in Task Manager
You can use the Networking tab in Windows XP Task Manager to get a visual representation of the traffic occurring on your local network connection. To access it, do the following:
- Right click the taskbar and select Task Manager.
- Click the Networking tab.
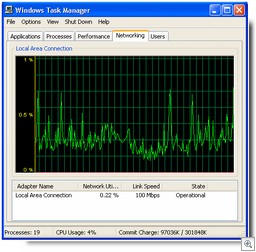
You’ll see a graph that indicates network utilization. Underneath it, columns show the network adapter name(s), percentage of network utilization in real time, the link speed for each adapter, and its state (whether it is currently operational). By default, total bytes sent and received are shown in the graph, but you can have it show bytes sent and bytes received separately, by clicking the View menu and selecting Network Adapter History.
You can also select many more columns to display. Click View and select Display Columns. For example, you can show the total bytes and/or bytes sent and bytes received so that you have the total numbers in addition to the graphic representation and percentage utilization.
The Networking tab is handy for diagnosing connectivity problems that may be related to network congestion. For more information about what each column represents, click here.
Store your Favorites online with Windows Live
There are so many Windows Live services that you may not be aware of some of them. Did you know that you can store your favorites online so they’ll be accessible anywhere, no matter what computer you’re using? If you have a Windows Live ID, just go to http://favorites.live.com and sign in. You’ll need to accept the terms of use agreement, Then you can import your existing favorites on your local computer to your Windows Live account. Just click the Import option in the Add menu at the top of the page. Adding new favorites is simple, too.
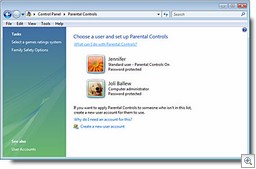 Parental controls in Vista put you in charge
Parental controls in Vista put you in charge
In homes with young children, allowing the kids to benefit from the educational value of the Internet without exposing them to its dangers is a big concern. Vista lets you set parental controls on your kids’ user accounts (this works only for local computer accounts, not domain accounts). This is done via the Set Up Parental Controls option in Control Panel. On a per-user basis, you can configure settings to specify which Web sites are allowed, as well as allowed types of content. You can set time limits for when the computer can be used, what games can be played (based on their rating, content or title) and block programs by name. You can also have activity reports recorded that you can review. For more information, click here.
Patch fixes vulnerability in wireless networking cards
A while back, there was a big uproar over the fact that some wireless networking adapters built into laptop computers had a vulnerability due to the fact that they start scanning automatically for wireless networks when you reboot the computer or when it wakes up from hibernation. Microsoft has released a patch for XP SP2 machines to fix the problem, but it wasn’t included with the Patch Tuesday updates. You have to manually download and install it, at least at this time. If you’re using a laptop with embedded wireless, it’s a good idea to do so. You can get it here.
Can I remove my user information from Windows Messenger?
You may find that after using Windows Messenger, your user name is displayed in the list of Windows Messenger users. If you want this want this information private, you can delete your user name from the list that Windows Messenger saves. How to do it depends on whether the computer is a member of a workgroup or a domain. Here’s how:
- Click Start | Control Panel.
- Click User Accounts.
- On a workgroup computer, click your user account in the list. Under Related Tasks, click Manage my Network Passwords. Select the user account in the Stored User Names and Passwords box and click Remove.
- On a domain computer, click the Advanced tab, click Manage Passwords, and in Stored Users and Passwords, select the user account and click Remove.
- Click OK.
- Click Close.
Now your user name shouldn’t appear in the list in Windows Messenger.
Can’t synch offline files as you expect in XP
If you try to synchronize your offline files on your Windows XP computer and get an error message that says “More data is available” or “The system cannot find the file specified,” it may be that a cache has become corrupted. There is a hotfix available that addresses this problem, as long as you have SP1 or SP2 installed. To find out how to get the hotfix, see KB article 903891.
How to copy data from a corrupted profile to a new one
If your user profile becomes corrupted, you can copy the files and settings from the old profile to a new one. This doesn’t apply to Outlook Express email messages and addresses. For instructions on how to create the new profile and then copy the relevant files to it, see KB article 811151.
XP stops responding at the Welcome Screen
If your computer stops responding (hangs up) when the Welcome screen is displayed after a reboot, and the keyboard and mouse stop working, you might receive the following message after you restart again: “System restart has been paused. Continue with system restart. Delete restoration data and proceed to system boot menu.” This happens because the computer goes into hibernation and accesses a corrupted memory snapshot. For instructions on how to fix it, see KB article 294427.
Internet enabled surveillance cameras can catch burglars in the act
If you’ve installed Internet enabled surveillance cameras that can be accessed via the web at your home or business, you probably already know that they can keep you apprised of what’s going on when you’re gone. A Brazilian businessman recently saw a criminal burglarizing his house, watching on his laptop while he was traveling in Germany, and police were able to get there in time to catch the bad guy. Link here.
Gartner predicts Vista will be the end of Windows
A report released by the Gartner research firm earlier this month predicts that Vista will be Microsoft’s last big operating system release. Many in the IT industry are, to put it mildly, a bit skeptical. Gartner’s rationale is that operating systems will become more modular, with “more flexible updates.” Of course, Microsoft has been releasing incremental updates for years (hey, Gartner guys, that’s what service packs are all about). Of course, crystal balls are notorious for being a bit inaccurate.
Vista update fights product activation crack
Last week, we told you about a reported crack for the Vista anti-piracy mechanism. There are already several cracks out there that attempt to bypass product activation. This week Microsoft released an update to Vista that’s supposed to combat the “Frankenbuild” product activation workaround. Read more here.
Hackers selling Vista exploits for big bucks
Once upon a time, hackers did their dirty work just for the fun of it. Now they’ve gone commercial. It’s been reported by Trend Micro that members of the hacking underground are trying to sell exploits for Windows Vista. The price tag: up to $50,000. Bad guys can also buy stolen personal data from the same sources; that’s where much of the information stolen in phishing attacks ends up. Read more here.