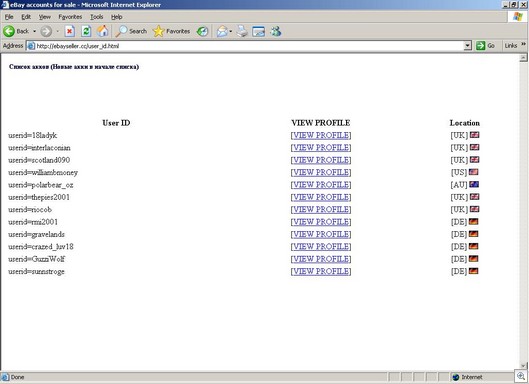
19 confirmed sites now using the IE vulnerability, as reported on security lists by Dan Hubbard (alert) at WebSense and Joe Stewart at Lurhq.
These can be very nasty. Our analysis of one site, www(dot)textrum(dot)se (since shutdown):
The exploit calls a file, updater.exe
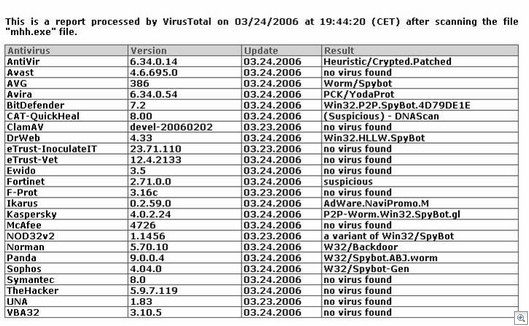
Norman sandbox report:
Found Sandbox: W32/Backdoor; [ General information ]
* Anti debug/emulation code present.
* Creating several executable files on hard-drive.
* File length: 46644 bytes.
[ Changes to filesystem ]
* Creates file C:WINDOWSSYSTEM32Updater.exe.
* Creates directory C:WINDOWSSYSTEM32kazaabackupfiles.
* Creates file C:WINDOWSSYSTEM32kazaabackupfilesdownload_me.exe.
[ Changes to registry ]
* Creates value “Windsupdate”=”Updater.exe” in key “HKCUSoftwareMicrosoftWindowsCurrentVersionRunOnce”.
* Creates value “Windsupdate”=”Updater.exe” in key “HKLMSoftwareMicrosoftWindowsCurrentVersionRun”.
* Modifies value “Dir0″=”012345:C:WINDOWSSYSTEM32kazaabackupfiles” in key “HKCUSoftwareKazaaLocalContent”.
[ Network services ]
* Connects to “[redacted].com” on port 6667 (IP).
* Connects to IRC server.
* IRC: Uses nickname [redacted]
* IRC: Uses username [redacted].
[ Security issues ]
* Possible backdoor functionality [Authenticate] port 113.
[ Process/window information ]
* Enumerates running processes.
* Will automatically restart after boot (I’ll be back…).
* Attemps to open C:WINDOWSSYSTEM32Updater.exe NULL.
* Enumerates running processes several parses….
* Creates a mutex coolbot1.c4.
Logs information to: C:WINDOWSsystem32sys.ini
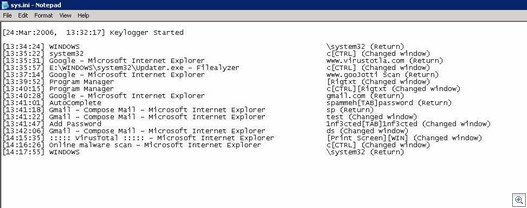
More work going on… may post more later.
Based on what we’re seeing in the wild right now, we hope that Microsoft will patch this new IE exploit prior to April 11 (the next scheduled update).
Keep your AV and antispyware updated and run your software firewall (free suggestions here). The only valid workaround for this patch is to turn off Active Scripting in IE, or use another browser. Your AV may very well catch these nasties, but don’t count on it in the immediate future.
Alex Eckelberry