Not the first time it’s happened.
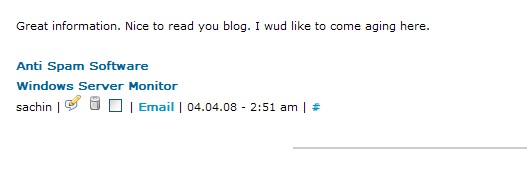
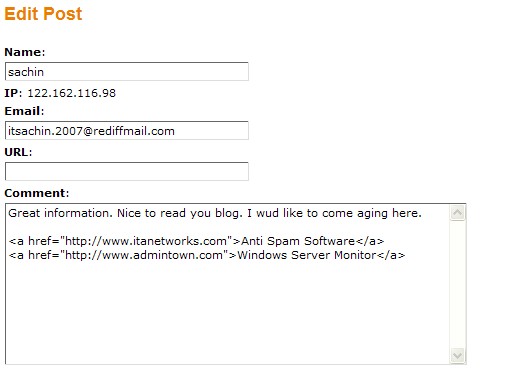
But I’m happy that someone would like to “come aging” here at this blog. We’re located in Florida, after all, and support a rich and robust retirement community.
Alex Eckelberry
The Great Years: 2004-2010
Not the first time it’s happened.


But I’m happy that someone would like to “come aging” here at this blog. We’re located in Florida, after all, and support a rich and robust retirement community.
Alex Eckelberry
This afternoon, we got a highly customized email purporting to come from the IRS, which of course, does nothing more than load malware.
The email is made out to a key financial contact here at Sunbelt (name obfuscated for this post).
As you can see, it’s quite convincing. (Incidentally, “Sunbelt Software Distribution, Inc.” is no longer our company name, it was recently changed to simply Sunbelt Software. But that’s a side note.)
Attached to the email is a zip file, which has a .scr file in it:
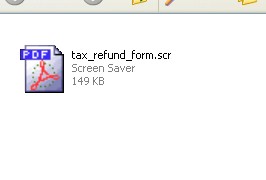
Once clicked, the.scr file downloads several other files and reaches out to several servers including the “Office of the Attorney General – California Department of Justice” – where a PDF file is downloaded from and opened using your default PDF viewer. In this case, we got a PDF from the following location:
http://ag(dot)ca(dot)gov/cms_pdfs/press/n1478_complaintat&tunauthorizedchargesfinal_tbf2.pdf?id=1594
The entire purpose of this PDF is to make things look official. Otherwise, it’s meaningless, and does not appear to be malicious.
Interestingly, the id parameters for the PDF change with each install (increase in number) and the link is not indexed and the name of the PDF corresponds to the nature of the attack. And, interestingly, the malware set’s its user agent to:
Accept-Encoding: identity
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en;) Gecko/30060309
Firefox/1.5.0.7
This raises the question: Is this California .gov website compromised in some fashion to serve the pdf? We simply don’t know at this juncture, but this does look suspicious.
Then, a number of other URLs are contacted to download malware, and the user is left with keylogger on their system. It also appears that malware is downloaded from a number of compromised sites.
Alex Eckelberry
(Additional credit to Sunbelt’s Adam Thomas for his invaluable help)
We partnered with the folks at CyberPatrol on some business in the past, nice to see they’ve been acquired now by some other friends — the Bob Bales team (Bob founded PestPatrol and Exploit Prevention Labs).
Link here (PDF, alas).
Alex Eckelberry
We announced our new Unlimited Home Site License yesterday. We had some trepidation on launching on April 1st, but due to a variety of internal timing issues, we needed to get the release out.
Of course, it turns out that some thought it was an April Fools joke.
Just to make it clear, it’s not a joke — it’s real. Here’s the link to the blog post, and the press release.
Alex Eckelberry
I suspect quite a few people in the malware research space got pretty unnerved when they first saw Offensive Computing’s site today:
In case you don’t recognize the image, that is the exact image you get right now when going to a storm worm site. In fact, the source on the site is identical to the source used in the storm sites.
But, of course, it’s a joke. The exes pushed on the site are harmless. Worse, it’s a rickroll — there’s a link in the binary to a Rick Astley video.
Alex Eckelberry
(hat tip to Nick Fitzgerald)
Today, we’re introducing something completely new: An unlimited home site license. This will be an option on all of our consumer products.
Here’s the backstory:
Sunbelt is a research-intensive organization — we are constantly doing surveys.
Back in February, we were doing a survey for our upcoming security product, VIPRE (shipping later this month), and our head of marketing noticed something interesting: On average, about 35% of the respondents had more than 3 PCs in their household. (21% responded with three computers, 28% responded with two computers and 17% responded with one computer, out of 1009 respondents, obtained from Sunbelt’s database.)
The lesson was clear: a large group of users out there are getting to a point where a typical 3–user license just doesn’t cut it. That got our marketing head thinking about a whole new idea, taken from the enterprise software space: An unlimited home site license. I really liked the idea.
So, after further discussion and some testing, we’ve formally launched our new Unlimited Home Site License program. All of our consumer products have this in place right now, but it will also be available for VIPRE.
This is an unlimited license — it works for as many computers as you have at home, whether 3, 10, 50 or 100 computers. No guilt, no BS. No limits.
Here’s how the pricing breaks out:
iHateSpam ……………………………………………….. $39.95
CounterSpy……………………………………………….. $39.95
Sunbelt Personal Firewall ………………………….. $39.95
VIPRE™ Antivirus + Antispyware …………….. $49.95
The annual subscription provides protection for unlimited PCs and includes one year of software updates and upgrades, any relevant threat definitions, and live US-based toll-free technical support.
You can read more about the new program here.
Alex Eckelberry
 The text on this site promotes a bundle of Vista Premium, OneCare for free, and a book.
The text on this site promotes a bundle of Vista Premium, OneCare for free, and a book.
I assume that in the US or the EU, bundling the OS with their antivirus product would raise the ire of the gubmint (no, I never hinted at this before).
But the bigger news? It comes in a PINK BOX (with flower petals, of course)!
I think the Symantec team needs to get their Super Sentai fighters ready!
Alex Eckelberry
(Thanks Donna)
PC Mag just gave it a rather nice writeup, here.
iHateSpam is the product with which I launched Sunbelt’s security business nearly 6 years ago, so it always has a special place in my heart.
Alex Eckelberry
Typically looks something like this (there are variations).
Jose at Arbor has a writeup on it here, saving me the work.
And poor detection on one sample I picked up (VT).
Alex Eckelberry
(Additional thanks to Lance James)
Not major news, but there’s a new Pandex campaign going around (Pandex is a trojan that turns your machine into a spam zombie).
Typical spam email looks like this:
(Image thumbnailed due to offensive content.)
The URL typically points to a compromised site hosting the trojan. The trojan has also been observed as an attachment to the same email.
Virus detection is fairly weak on at least one of the samples we checked. (one sample: VT and Sandbox report).
Alex Eckelberry
As chaos broke out at Heathrow Terminal Five, BA bosses were throwing a party to congratulate themselves on a job well done.
A free buffet, doughnuts and soft drinks were laid on at the T5 Celebration Party as BA managers enjoyed music from a string quartet. Staff were also given boxes of chocolates and commemorative T5 pens.
Meanwhile the new terminal was in meltdown with flights cancelled, bags lost and staff unable to find parking spaces.
And as thousands of passengers faced misery, BA Chief Executive Officer Willie Walsh gave a speech at the party thanking his team for their good work.
Link here.
Alex Eckelberry
(hat tip)
Wow.
…the campaign is still up and running, poisoning what looks like over a million search queries with loadable IFRAMES, whose loading state entirely relies on the site’s web application security practices – or the lack of…
And…
USAToday.com, ABCNews.com, News.com, Target.com, Packard Bell.com, Walmart.com, Rediff.com, MiamiHerald.com, Bloomingdales.com, PatentStorm.us, WebShots.com, Sears.com, Forbes.com, Ugo.com, Bartleby.com, Linkedwords.com, Circuitcity.com, Allwords.com, Blogdigger.com, Epinions.com, Buyersindex.com, Jcpenney.com, Nakido.com, Uvm.edu, hobbes.nmsu.edu, jurist.law.pitt.edu, boisestate.edu.
Link here.
Alex Eckelberry
(Thanks Francesco)
Interesting article about what apps crash in Vista.
Microsoft (NSDQ: MSFT) wields incredible power in the computer industry. Still, when it comes to the image of its flagship operating systems, it is greatly at the mercy of third-party software developers. When users sit down to use Windows, the code written by Microsoft sometimes doesn’t matter as much as the bugs left behind in poorly written applications and drivers. If a crash does happen, the average user is more likely to blame “that crummy Windows” than to figure out it’s a bug with a device driver.
We rarely get to hear Microsoft’s side of the story on this; it doesn’t want to publicly berate partners about software quality. Occasionally, though, some unvarnished truth gets through. For example, the folks at Ars Technica have been digging around in the Microsoft e-mails released as part of the “Vista Capable” lawsuit. Those e-mails had some revealing information about the causes of Vista woes.
According to the Microsoft e-mails, Nvidia’s drivers alone caused 28.8% of the crashes seen in Vista during the report period. (The report says only that it covers 2007, but it likely does not cover the entire year.) Microsoft drivers come in second at 17.9%, ATI is third with 9.3%, and Intel takes fourth place with 8.8%. Webroot Software, makers of an anti-spyware application, was next with 2.9%. All the other drivers, from hundreds of companies listed on the report, plus “Unknown”, make up the other 32.3% of the crashes.
Link here.
Alex Eckelberry
Here’s a new one: Google Adwords phishing.
According to the folks over at CSIS, the email reads like this:
Dear Google AdWords Customer!
In order to update your billing information, please sign in to your AdWords account at https://adwords.google.com, and submit your billing information. Your account will be reactivated as soon as you have entered your payment details. Your ads will show immediately if you decide to pay for clicks via credit or debit card. If you decide to pay by direct debit, we may need to receive your signed debit authorization before your ads start running, depending on your location. If youchoose bank transfer, your ads will show as soon as we receive your first payment. (Payment options vary by location.)
Thank you for choosing AdWords. We look forward to providing you with
the most effective advertising available.Sincerely,
The Google AdWords Team
More here (no, it’s not transliterated Klingon, it’s Danish). CSIS says these are all fast-flux on Chinese domains.
Alex Eckelberry
(Additional thanks to Mike at Shadowserver)
Just for grins and giggles, here’s some new rogue security products designed to extort money from you.
March:
unigray(dot)com
spymaxx(dot)com
spywatche(dot)com
pcprivacytool.com
thelastdefender(dot)com
thespybot(dot)com
spywareisolator(dot)com
pc-cleaner(dot)com
pc-antispyware(dot)com
MalwareWar(dot)com
DataHealer(dot)com
These can all be removed with the free trial version of CounterSpy.
Alex Eckelberry
(Credits: Patrick Jordan, Bharath)
Still trying to get my mind around this one:
…one of my close contacts has confirmed there is someone going around either hijacking, hacking or phishing user accounts on Facebook, then randomly uploading pictures of child torture to their funwall…
So far, I have one definite confirm on at least two accounts that were taken over (most likely by the same individual), one of which had the child torture pictures uploaded to it and the other – well, it wasn’t child torture but it nearly cost someone their marriage, according to my friend.
Link here.
Paperghost (the author) just updated me with this:
apparently the pics were placed on the hacked accounts funwall, which of course means anyone would see the pics simply by visiting the profile, instead of having to navigate to the albums
So far, no confirmation or screen shots.
If true, this is very messed up.
Alex Eckelberry
Follow-up to my previous blog entry:
In what must be the fastest turnaround in corporate history, Abary told me that the $49.99 charge is dead. “We didn’t intend that to happen,” he said, blaming the snafu on an internal miscommunication. “We’re removing the $49 charge,” he told me. Beginning this spring and rolling out to all products through the end of the year, there will be no charge to order a custom-configured Sony VAIO computer, and you will be able to opt out of every trialware application, without exceptions.
Link here.
Good for them.
(Now, see if you can say this post’s headline 10 times perfectly.)
Alex Eckelberry
(Thanks Angus)
No news in having another trojan doing typical host redirects, but in this case, we found the use of Google’s name to be mildly interesting: A new variant of Trojan.Delf from the Loadscc gang changes your host file to redirect to a fake Google page. The fake Google page pushes a SpywareIsolator, a rogue antispyware program.
O1 – Hosts: 124(dot)217(dot)251(dot)147 google.dk
O1 – Hosts: 124(dot)217(dot)251(dot)147 google.se
O1 – Hosts: 124(dot)217(dot)251(dot)147 google.co.nzand so on…
Resulting infection if one follows the suggestion above:
Alex Eckelberry
(Thanks Patrick Jordan)
Sony launches a new option, which will give you a $50 discount on your purchase if you choose to crapify it. On Engaget, here.
In other words, they’re charging $50 to not crapify your computer.
I have a Vaio and actually really like Sony product. However, someone has their head screwed on backward to think this idea is going to fly. It shows such a complete disconnect from the market.
Sony got a good start appealing to enthusiasts, with beautiful hardware design. But I can only imagine some freshly-minted MBA product manager coming up with this brilliant idea to “monetize” crapware. I hope that same bozo who thought up this absurd idea will be so fired.
Of course, there’s always the free PC Decrapifier. But that doesn’t beat a clean machine to start.
Alex Eckelberry
(Thanks Robert)