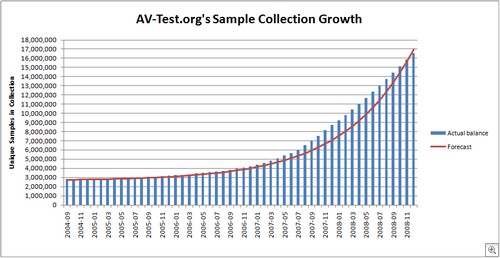
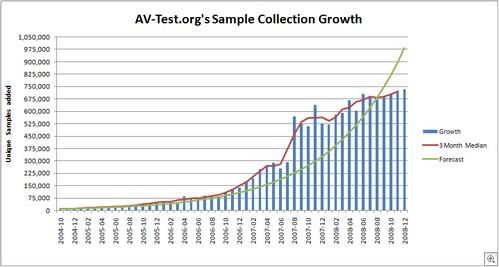
I have a lot of respect for Anne Mulcahy, Xerox’s CEO who has announced her retirement.
One thing that I like about her is that she gets innovation:
To be sure, a company’s R&D investment pool looks tempting in tough times. And draining it might save a few jobs or help make the quarterly results less painful. However, if you fail to fund the future, all you’ll be left with is a really lean company trying to churn old ideas into new business…When Xerox went through a downturn of its own making earlier this decade, everywhere I went, lenders and investors were demanding I cut our R&D spending. But to me, Xerox innovation was sacred. Why avoid financial bankruptcy only to face technological bankruptcy down the road?
Some of the tech CEOs I know right now who are in trouble are, in many cases, the ones who have not spent enough on R&D — the core of innovation in a technology company.
There is an attitude often in financial circles (and among non-technical managers), that research and development is not the vital lifeblood of an organization. It can be off-shored, or outsourced, or heavily cost-managed. I know several companies where the financial backers are soaking the company for cash flow, but not investing heavily in new technology.
An organization starts with a product. It doesn’t start with a sales, finance or marketing department. It starts with something that’s produced. And in technology, the people who make your products are your R&D department. Without a product, you have nothing.
The sometimes painful truth is that the business of technology is very R&D intensive. There are cycles, where you make a new product, make money off of it, and then go into another major new R&D phase. This is an ongoing process.
However, what is commonly observed is a company spends on innovation, gets successful, and then doesn’t realize that it actually needs to keep spending on innovation. The companies that would qualify for this list are legion.
Simply straight-lining your R&D expenses at some magical percentage of total revenue is not the right approach. A company must invest in R&D with relevancy to its current situation. Right now, almost 40% of our staff is dedicated to R&D, a staggering figure for some people. But we’re at an absolutely essential time where innovating is the most important thing we can do, to remain competitive. It pays off — our growth is 70% year-over-year. So we keep investing, and investing. We’re making money, but we’re also spending money on making sure that two years from now, we continue to have the most innovative products. (Our percentage of R&D won’t always be this high, because as revenue goes up, the percentage dedicated to R&D goes down, but the current ratios are relevant to where we need to invest now.)
So to those developers out there facing budget cuts, fight back. Teach your managers that you need the money to make the products that the company will need in the future — so they will have jobs themselves.
In short: Innovate or perish.
Alex Eckelberry
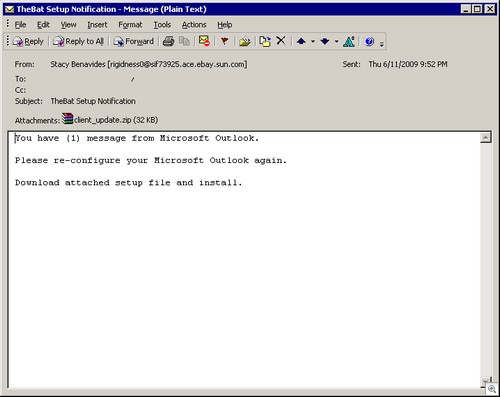
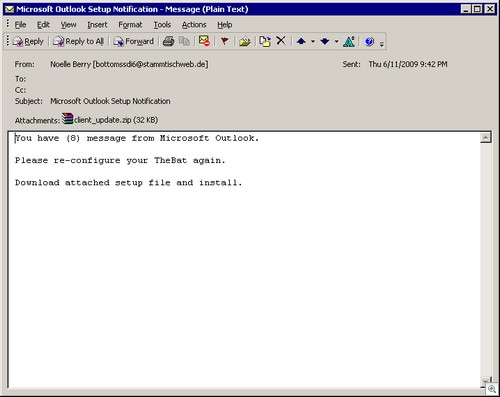

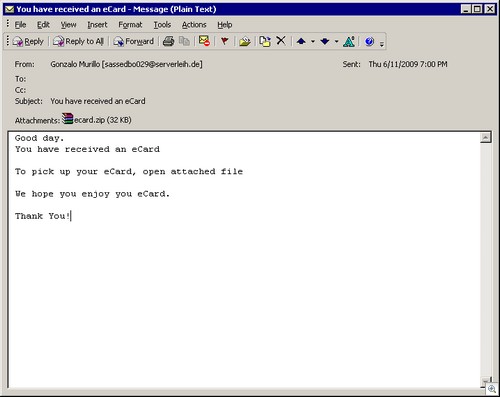
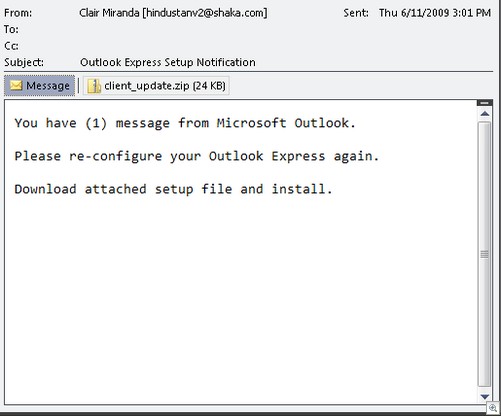
 FTC
FTC 
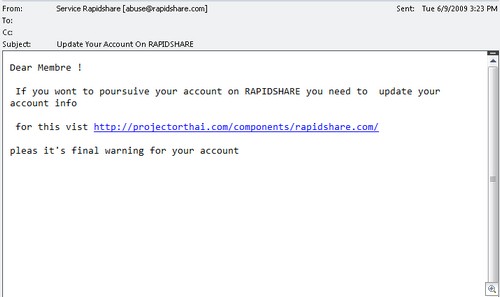

 The infected site, hxxp://an-inconvenient-truth.com, (DO NOT GO THERE!) has been registered since 2006, so, it’s probably a legitimate site that’s been taken over.
The infected site, hxxp://an-inconvenient-truth.com, (DO NOT GO THERE!) has been registered since 2006, so, it’s probably a legitimate site that’s been taken over.