Sunbelt Software is supporting tomorrow’s Safer Internet Day, an awareness-raising initiative co-funded by the European Commission. Organizations in more than 60 countries are behind the campaign, this year focusing on the theme “Think B4 U post!”

New technologies have turned all of us, and mostly young people, into publishers of information, pictures, and videos. While bringing about new opportunities for personal expression and creativity, the same technologies can also conjure up embarrassing or even traumatic situations. For example, photos, once posted online, remain online and can be seen by anybody, even years after they have been posted. Therefore, children and teenagers need guidance to manage their online identity in a responsible way, to be in control of their own online identity.
“We are proud to be supporting Safer Internet Day. Whilst it is generally assumed that the latest generation will be the most technologically savvy, we see that children are taking increasingly liberties with their online identity and opening themselves up to a wealth of very real dangers,” explained Sunbelt Software CEO Alex Eckelberry. “By following this simple five point checklist they can enjoy the many social and academic benefits of the Internet safely.”
Sunbelt Software offers the following five-point checklist to both children and parents to enable a safer online experience:
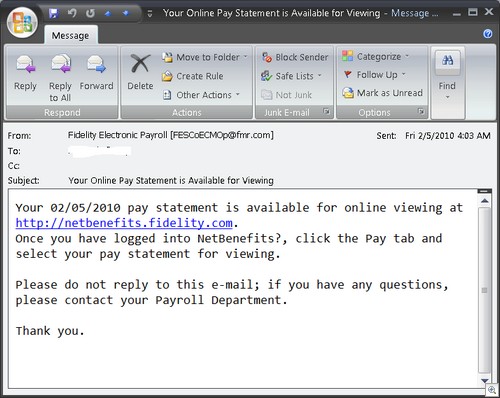
1. Do not to open any emails that come from senders you don’t know. Many of those emails have luring titles like “You have won a lottery” or “Happy birthday, I have a present for you” and so on. Never open any attachments coming with such emails, as it is likely that in such cases you will install a virus or a worm in your PC.
2. Try to avoid suspicious websites, and if you accidentally enter one that seems strange, leave it immediately.
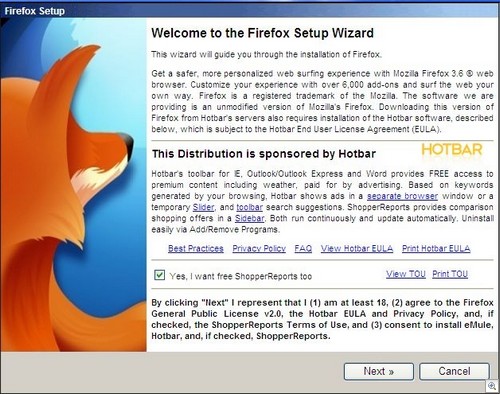
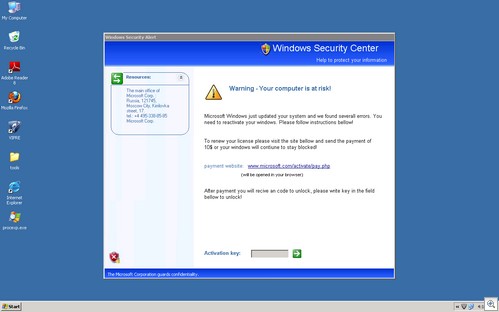
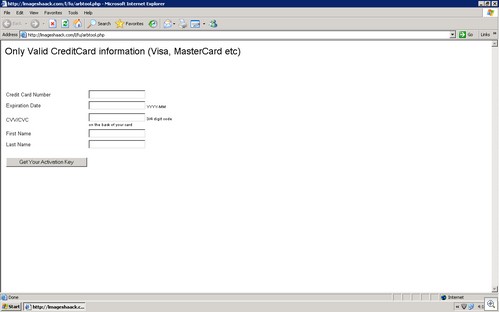
3. If pop-up windows alert you or ask you to agree to anything, immediately close them and never click on any button inside them.
4. Install antivirus software such as Sunbelt Software’s award winning VIPRE on your PC. This will protect your computer against viruses and other malware threats. Antivirus software needs to be regularly updated, and can provide added security such as content or website filtering.
5. Install a firewall, which will keep watch on all files that go in and out of your computer.
About Insafe
Insafe is the European Safer Internet awareness-raising network co-funded by the European Commission. It’s made up of national contact centers across the European Union and in Iceland and Norway, with partner organizations in Argentina, Australia and the US. Insafe aims at empowering users to benefit from the positive aspects of internet whilst avoiding the potential risks.
Further information is available at www.saferinternet.org or contact info-insafe@eun.org
Tom Kelchner