Update: Fix and new data here. Also, to understand the types of systems infected (all of them were unpatched XP systems, click here).
Ok, we have the latest on this identity theft ring. And it’s pretty interesting.
Remember that all we found was the cache of data from the thieves — we didn’t have the actual keylogger that was responsible for it. We had a keylogger we had found that was similar and provided us some clues, but not this specific one that was reporting all this data back.
So we had to find the keylogger. That entailed trying to actually get a hold of a machine.
Last night, we finally got an infected machine and were able to figure out what’s going on.
Briefly:
– It’s footprint is extremely small — about 26k.
– It seems related to the CoolWebSearch gang, but that is still not certain.
– It is related to the Dumador/Nibu family of trojans. The keylogger executable is winldra.exe.
– It runs under Internet Explorer (IE), so for the average user, it will generally go undected if you’re using a software or hardware firewall. So much for my ranting about the need to run a software firewall.
– It turns off the Windows firewall.
– It steals data in the IE Protected Storage area.
– It steals data from the Windows clipboard
– As is normal with Dumador/Nibu variants, it steals logins and passwords from a number of programs: WebMoney, Far Manager and Total Commander; and modifies the host file to stop access to Trend Micro, Mcafee.com, Symantec.com, Etrust/Computer Associates, AVP, Kaspersky, F-secure, etc.
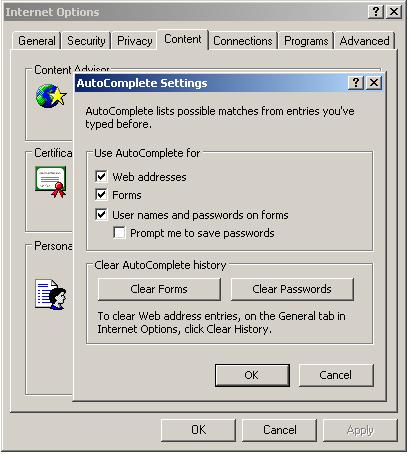
Since one thing it does is steal the IE Protected Storage Area, you can protect this data by turning off all the AutoComplete stuff in IE.
So far as we know, this keylogger is not detected by a number of the major AV companies. We are coming out with a fix in the next several hours which will be available a) to customers running CounterSpy (or the free trial) and b) through a free application we will make available.
Of course, we will be sharing data on this keylogger with AV vendors and antispyware companies, so definitions should start to propagate out from a number of other sources as well.
I will keep this blog updated as we get more data.
Alex