I’ve been tracking a steadily increasing amount of redirects, often from legitimate .gov, .edu or major corporations.
The cause of these redirects are, in many cases, a result of configurations of Ultraseek/Autonomy/Verity search software (Ultraseek, Verity and Autonomy are all the same company). Most, if not all, enterprise search redirects I’ve seeing now are related to Ultraseek.
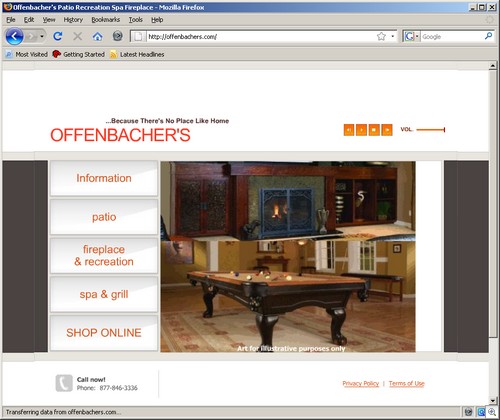
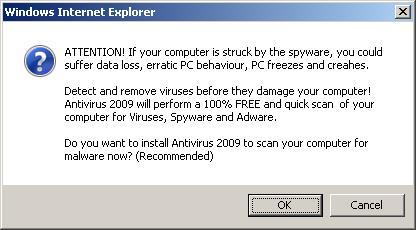
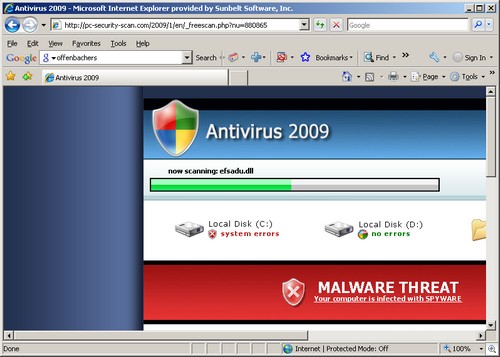
For example, we see that the Coca Cola Credit Union is currently redirecting to malware.
An example string is as follows:
http://search.creditunion.coca-cola.com/creditunion/cs.html?url=//marker2009 com%2Fin.php%3F%26n%3D1131%26t
(The link is slightly munged for safety).
Here’s that same redirect that’s safe.
Going up a notch, we see the tell-tale Ultraseek search engine.
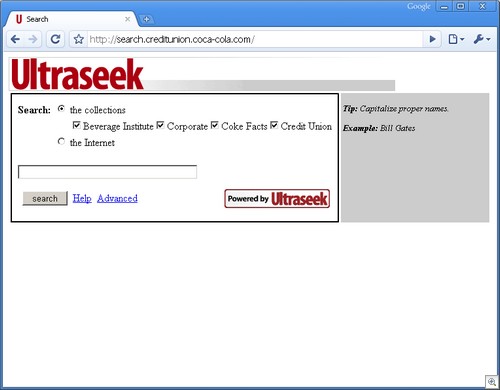
This is a simple configuration issue and leaves a wide-open redirect. Webmasters using these tools must close them from redirects.
These search hacks have involved a number of very high profile institutions. I often report them but don’t bother to blog them. But I’ve gotten a bit tired of seeing them occur so easily and regularly.
For example, here are some redirects currently using Ultraseek search redirects — these are live, right now:
search.networkworld.com/cs.html?url=//marker2009 com
search.neb.com/cs.html?url=//marker2009 com
www.javaworld.com/ifind/java/cs.html?url=//marker2009 com
search.creditunion.coca-cola.com/creditunion/cs.html?url=//marker2009 com
search.icbcasia.com/cs.html?url=//marker2009 com
search.bucknell.edu/cs.html?url=//marker2009 com
search.ncrel.org/cs.html?url=//marker2009 com
search.dot.state.co.us:8765/cs.html?url=//marker2009 com
search.cignagovernmentservices.com/cs.html?url=//marker2009 com
searchawwarf.org/cs.html?url=//marker2009 com
search.wexford.ie/search/cs.html?url=//marker2009 com
search.paychex.com/cs.html?url=//happy2009texmas com
cpastar2.cpa.state.tx.us/cs.html?url=//halfstyles-1 com (likely uses Ultraseek)
search.ssga.com/cs.html?url=//happy2009texmas com
datafind.gov.bc.ca/cs.html?url=//halfstyles-1 com
mail2.sasked.gov.sk.ca:8765/cs.html?url=//halfstyles-1 com
All of these sites lead to sites pushing malware.
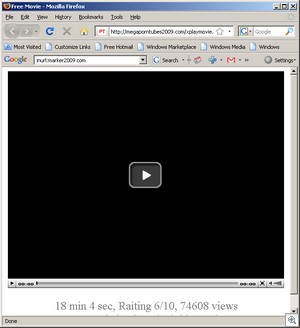
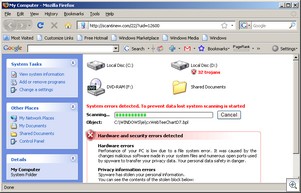
What needs to happen is that the folks at Autonomy/Verity/Ultraseek have to get a message out to administrators and webmasters warning them of the problem, and the configuration steps needed to resolve them.
Now, Ultraseek isn’t the only issue occurring right now in redirects… Perhaps more later.
Alex Eckelberry




 The
The