Good writeup by Gary Warner:
We are well past time for someone to declare a “Spam Crisis in China”.
There are three components to the Spam Crisis:
1) Certain Registrars in China who refuse to cooperate with abuse complaints and who let domains “live forever”, even when they are involved in criminal activity. We do not believe these companies are criminals. We believe that these companies have provided “reseller services” to criminals, and do not engage themselves proactively in stopping the criminal activities of their resellers. We look forward to helping in any way possible to identifying and stopping the criminals who are tarnishing the names of the companies listed below. I specifically name:
Sponsoring Registrar: 易名中国 ENAME Corporation, http://www.ename.cn/
Sponsoring Registrar: XIN NET TECHNOLOGY CORPORATION
2) Certain Network operators in China refuse to cooperate with abuse complaints and who let bad computers “live forever”, even when they are clearly involved in criminal activity. We invite the companies who are allowing criminals to continuously use their networks to take action so that they can be an International Success Story similar to our friends at HKDNR. We do not believe that these network companies are criminals. We believe that criminals use their network, and these companies have not yet found a way to effectively receive our complaints and remove these criminals from their networks. There are many companies, but I specifically name:
ASN 4837 CHINA169-BACKBONE CNCGROUP China 169 Backbone
ASN 4134 CHINANET-BACKBONE No.31, Jin-rong Street
ASN 9929 CNCNET-CN China Netcom Corp.
3) Law Enforcement activity. It is unacceptable in the International Community to allow one’s country to continue to serve as a haven for spammers of illegally counterfeited pills, illegally counterfeited software, and illegally counterfeited watches and handbags. It is also unacceptable to provide hosting services for numerous international criminals to place their servers on networks in your country. We invite Chinese Law Enforcement to become engaged in being part of the solution to this problem, and through dialogue with the International Community learn more about interacting with other countries about these issues.
More here.
Alex Eckelberry


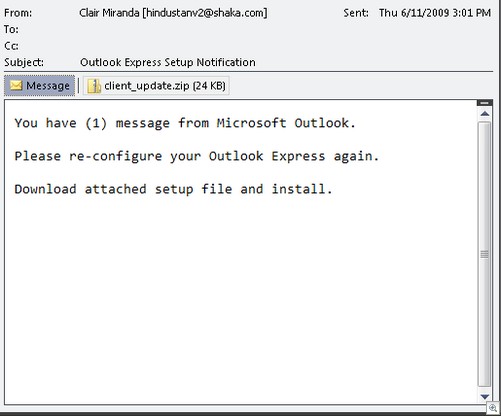
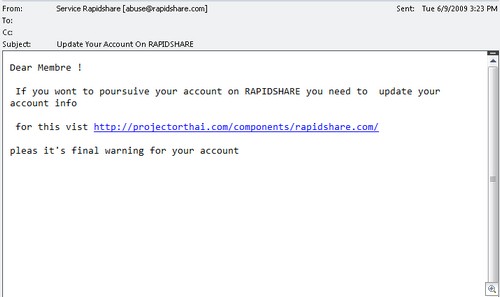
 FTC
FTC 

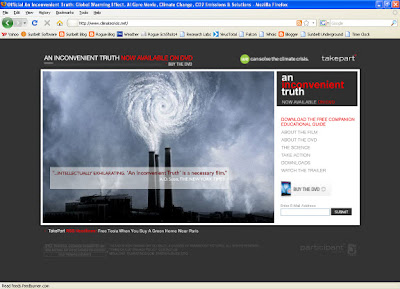
 The infected site, hxxp://an-inconvenient-truth.com, (DO NOT GO THERE!) has been registered since 2006, so, it’s probably a legitimate site that’s been taken over.
The infected site, hxxp://an-inconvenient-truth.com, (DO NOT GO THERE!) has been registered since 2006, so, it’s probably a legitimate site that’s been taken over.