AnchorFree’s response to our blog post:
Hey Tom,
This is Art from Hotspot Shield. I work for the marketing department.
I wanted to bring to your notice that users don’t start seeing ads just by downloading/installing Hotspot Shield. They only see ad if they connect to Hotspot Shield. So, they are basically opting in to see the ads in exchange for using our services. We are very upfront about this to our users.
Once they disconnect, they go back to the normal browsing without any ad
insertion. User is informed that HotspotShield is supported by advertisements
before the download and at the start of each private browsing session.
Also, we never store real user IP address and never provide real user IP
to any advertiser. Therefore, neither we nor our advertisers can disclose real
IP of our user even if compelled. Although I agree that it is not very clear in
our privacy policy. But we never store/share any users’ personal data. We limit
list of our advertisers to only ones who agree NOT to receive real user IP.
Feel free to email me or call me if you have any questions.
Cheers,
art
Our response from Eric Howes, Sunbelt Spyware Research Manager
Art:
I’m sorry, but nothing in your response changes our conclusion that Hotspot Shield is adware and that it is being presented to users in a deceptive manner. Let’s look at your claims one by one.
They only see ad if they connect to Hotspot Shield. So, they are basically opting in to see the ads in exchange for using our services.
Most adware vendors can and have made similar claims. The term “adware” was, in fact, coined to describe products that are ad-supported.
We are very upfront about this to our users. Once they disconnect,
they go back to the normal browsing without any ad insertion.
There is nothing straightforward, clear, or conspicuous in the disclosures you offer users concerning the ad-supported nature of the product or the fact that ad networks can (and undoubtedly are) using tracking technologies to monitor users’ response to ads and personalize those ads.
User is informed that HotspotShield is supported by advertisements before
the download and at the start of each private browsing session.
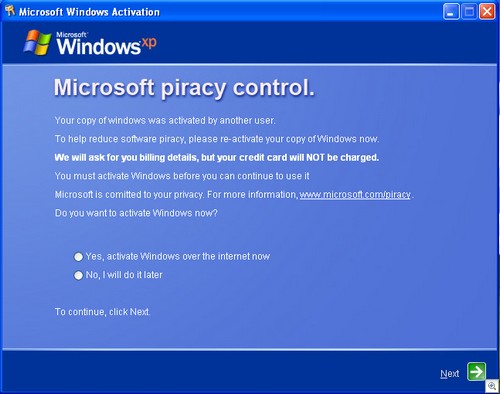
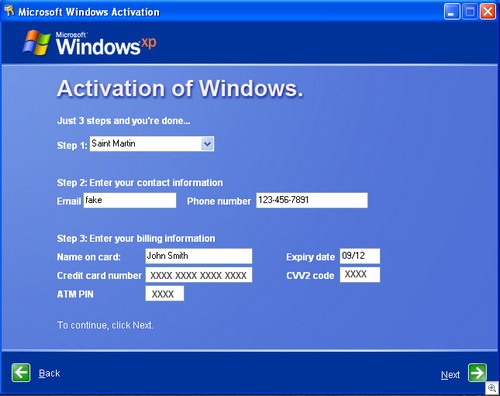
Neither of these claims is true. There is no notice on the Hotspot Shield home page or download page that the product is ad-supported. To the contrary, the home page sports that flashy green “no adware/spyware” logo, leading users to believe that quite the opposite is true. Although there is a link to the “terms of service,” that link is at the bottom of the page (the download link is at the top right), and even then users must scroll down to section 9 to find any mention of advertisements.
The installation/setup process similarly lacks any notice of these material terms outside of the EULA. Curiously, there is a separate screen for the optional toolbar (presented to users as a means of helping AnchorFree keep the product free for use), but nothing equivalent for the advertising functionality of the core program itself.
Finally, what the user sees at the start of each private browsing session is a connection status message that, again, makes no mention of the ad-supported nature of the product.
It should also be noted that even though I carefully unchecked all the options to have AnchorFree take over my home page, search, and error page settings, my browser’s home page was still hijacked to the AnchorFree “privacy search” page at the start of each “private browsing session.”
Also, we never store real user IP address and never provide real user IP to any advertiser. Therefore, neither we nor our advertisers can disclose real IP of our user even if compelled. Although I agree that it is not very clear in our privacy policy. But we never store share any users’ personal data. We limit list of our advertisers to only ones who agree NOT to receive real user IP.
The real problem is that AnchorFree goes out of its way to create user expectations that are entirely opposite of the true ad-supported functionality of the product. Moreover, it’s fairly well established at this point that users’ true identities (or something very close to them) can, given enough data, be derived from the browsing profiles created via the tracking technologies used by major ad networks.
The key test or question in this case is a simple one. AnchorFree promotes Hotspot Shield as means for “protecting your privacy, security, and anonymity on the web.” What would users think if they knew that the very first thing AnchorFree does after users start a “private browsing session” is hand them over to invasive advertising networks? I think they would be appalled.
Eric Howes
Sunbelt Software