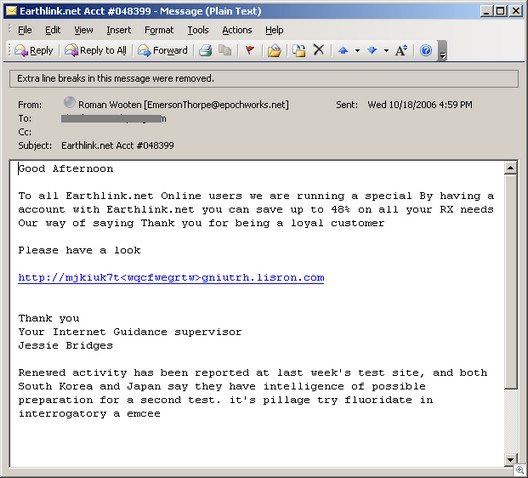
A reader recently suggested that I write an editorial about the psychology of returning emails. In other words, why is it that some people always seem to respond quickly to your email messages, while others wait a week or more to answer?
Most of us who send and receive a lot of email know plenty of people in both camps. For instance, one of the guys at Sunbelt I work with on the newsletter consistently answers my messages so instantaneously that I’ve accused him of being an “always on” artificial intelligence instead of a real person (Hi, Dan). No matter what time of the day or night I send a message, his response seems to pop up within a minute. On the other hand, there’s a guy I work with at another company who invariably takes days or weeks to write back. If I need info for an important matter, I often have to resend my message two or three times. While the “next moment” responders may be a little scary, the email procrastinators are downright frustrating, especially when you need their input to get your work done.
Of course, some folks have good reasons for their less-than-timely replies. They might have suddenly been taken ill or be on vacation, traveling on business, or having an Internet service outage. In today’s netcentric world, many of us have people we “know” only through the ‘net. We may work with them online on a frequent basis and even feel close to them, but we don’t even have phone numbers or physical addresses for them, may not know what state (or even what country) they live in, their race/ethnicity, how old or young they are, or in some cases even what gender they are if they have names that can be either male or female. I worked with an editor for one online publication for several years, all that time thinking I was dealing with a man, only to find out accidentally that “he” was actually a “she.” Oops. Because our online relationships are so compartmentalized, we don’t necessarily know what’s going on in a person’s “real life” that prevents him/her from answering the mail.
Another reason people sometimes don’t respond is because they never got our message in the first place. With unwanted commercial email posing such a big problem, almost every ISP or corporate mail server implements some type of spam filtering, and many computer users have their own client-side anti-spam software running, as well. Unfortunately, none of these spam filters are perfect, and there are always some “false positives” – email messages that get blocked by the spam filters even though they aren’t spam. If you don’t get an answer from someone you’ve emailed, you always have to consider the possibility that your message didn’t get through.
On the other hand, the spam filtering problem also presents a handy excuse for those who forgot or were too lazy or avoidant to answer messages. They can just claim to have never received the mail, and who can tell the difference? One solution to that problem is to request a receipt when the person receives or opens your message. Most mail clients make this easy to do.
Unfortunately, it’s not the greatest solution. In most cases, the recipient can choose not to send the receipt even though you’ve requested it, and many people find read receipts highly annoying. Even if you intend to answer, you may not have time to answer immediately, and you don’t necessarily want the sender to know that you read the message today at 8:00 a.m. if you may not get around to answering it until tomorrow afternoon.
And delaying a response isn’t the only way our email contacts can annoy us. Thinking about all this led me to the broader question of email etiquette in general. Sometimes the measures we take to try to avoid annoying others end up being annoyances themselves. For instance, if you’re going to be cut off from your email for a few days, should you set up an autoresponder to send a canned message telling those who write to you that you’re not in? Many people hate those “out of office” messages – especially when the recipient is on an email list and the autoresponder sends an OoO message to the list in response to every post. But is it more or less rude than just letting people think you’re ignoring their messages?
And just how long should you wait after getting no response until you try contacting the person again? A day? A week? Should you just resend the message as if it were the first time, or should you mention that this is the second (or third, or whatever) time you’ve sent it? Obviously, the correct answer may depend on your relationship with the recipient and the urgency (or lack thereof) of the message content.
Then there are those people who respond to your email message by calling you on the phone – without emailing back to say they’re going to call. That’s one of my pet peeves, but no doubt they believe they’re being especially responsive. And they probably think I’m rude for not answering the phone if I don’t recognize the number on Caller ID.
Which brings me to another issue. Many of us were conditioned, as we were growing up, to believe that if the phone rang, we had an obligation to answer it – even though we were the ones paying the phone bill, presumably to have a communications tool for our own use and convenience, not as a means for others to invade our homes when we didn’t want to be invaded. Answering machines came along and changed our attitudes somewhat; now we could “screen” our calls (although few would admit to doing so) and pick up only the ones we wanted to take. Caller ID took that even further – even if the caller chooses not to leave a message, we can see who’s calling (or at least, the number from which he/she is calling) before the call even goes to voicemail. With new technology, we can even program certain numbers to go directly to voicemail, or be blocked altogether, or to have a distinctive ringtone so we know instantly that it’s someone whose call we want to take.
I suspect it’s this relatively new “pick and choose” attitude that’s spilled over to email, and may explain why so many people respond slowly, or not at all. Just as they no longer feel an obligation to answer the phone just because it rings, they feel no obligation to send a reply just because they get an email message. And the sheer volume of email reinforces those feelings.
What do you think? Are you an email procrastinator or an instantaneous responder, or somewhere in between? Do you use OoO messages when you’re going to be out or just keep ’em guessing? Do you get annoyed when you get back an Out of Office notice, or do you like knowing why your message is going unanswered? Do you ever pretend a message was “eaten” by your spam filters when you just didn’t answer? Do you request read receipts? Do you click “Yes” or “No” when asked if you want to send a receipt? What are your pet email etiquette peeves?
Deb Shinder, MVP