This new Mac trojan? Well, it’s actually fairly important news.
I don’t mean to sound breathless about it. As far as we know, it’s not widespread. But this is the first targeted, real attack on Mac users by a professional malware group.
As one of our security researchers put it:
“This is pretty groundbreaking, actually. Not from the standpoint of ‘malware can exist on Mac too’ (everybody who’s not a moron knew that), but really from the fact that this actual malware created by real malware groups, not one of those useless proof-of-concept of ‘malware can exist on Mac too’.”
Yet the chorus of yawns from the security space is deafening:
While security experts agree that such a piece of malware would pose a very serious threat to users, it remains unclear just how far the reported trojan has spread.
Representatives for McAfee, Symantec, and Trend Micro all told vnunet.com that their researchers had been unable to find the trojan in the wild or obtain a sample from Intego. A spokesperson for Symantec noted that Intego “has a tendency to overhype things. “
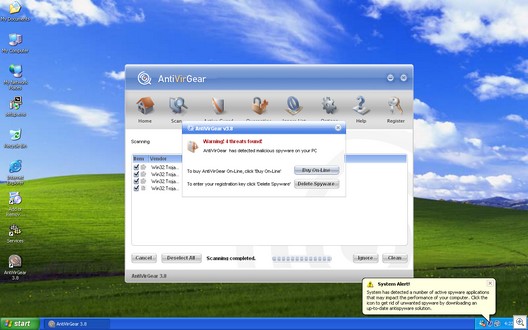
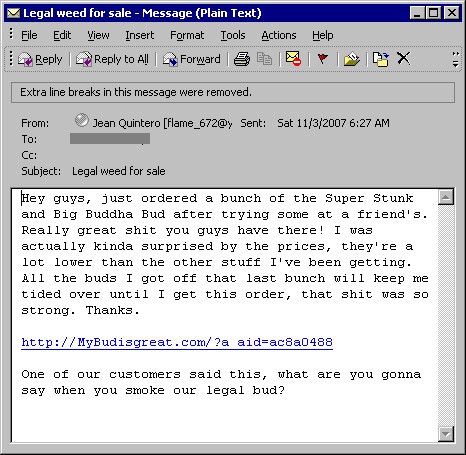
Well, putting aside the fact that it took us under 3 minutes to find the Trojan simply by doing a simple Google search, this shouldn’t be viewed as overhype (although one part of the article certainly is overhype: “the tool allows the attackers to redirect web traffic. Users attempting to visit Paypal, Ebay or certain banking sites for instance will be directed to a phishing website instead.” Nah.)
I don’t know much about Intego, a Mac antivirus company. But when I showed our resident Mac guru this Trojan, his reaction was real surprise. In his words, “I’ve been using Macs since 1989. This is the first time I’ve seen something like this.”
This is a good story.
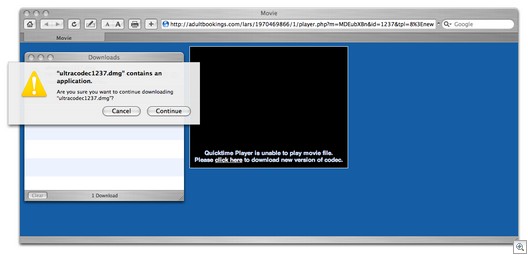
Again, I’m not trying to overhype. Mac users, hungry for pr0n, really do have to go through a few hoops to get this thing loaded. But we now have millions of new Mac devices out there, between the Touch and IPhone, running OS X.
The sole driving force behind malware these days is money. And this is simply a new market for these bad guys.
Let’s not ourselves in the security space get complacent.
Alex Eckelberry