“Anyone else getting this crap today?”
Alert reader David McSpadden notified Sunbelt of the following spear-phishing attempt that was sent to users, appearing to come from their system administrator. [The PDF contains a link to the executable for the user to download.]
“If you already received this information before and action has been taken, then please ignore.
“This important information about a security vulnerability requires your immediate attention!
“All systems detected using Adobe products have been sent out this e-mail and are all requested to update their systems urgently.
“Kindly follow the instructions in the e-mail as forwarded below.
“Failure to comply will result in all financial and non financial loss to be a liability of the receiver.
“Please treat this e-mail as a matter of urgency. No further follow up warning will be sent.
“**This e-mail is a computer generated e-mail from admin@xxxx.com and does not require a reply**
“— On Fri, 5/28/10, Rxxxxxx Bxxxxxx <rbxxxxx@adobe.com> wrote: —
From: Rxxxxxx Bxxxxxx <rbxxxxx@adobe.com>
To: Administrator <admin@xxxx.com>
Subject: Adobe Security Update
Date: Friday, May 28, 2010, 11:24 AM
“Broadcast message:
“Adobe has issued a directive which states that all systems running their software should be patched for the latest security glitch.
The CVE-2010-0193 Denial of Service Vulnerability has recently been discovered on several systems running the previously released version of the software, which has been further documented on security sites such as http://www.securityfocus.com/bid/39524
It is strongly advised that all systems running the Adobe software is updated with the latest security patch to avoid further situations hampering the security and integrity of the system. Failure to follow the directive would mean that any loss which occurs due to the negligence will be a liability of the company and not Adobe. The link to update the system with the latest patch and instructions are provided below:
“Download the instructions here: hxxp://190.144.101.204/adobe/update.pdf (requires Adobe Acrobat Reader).
To update your system, download the installation file here: hxxp://190.144.101.204/adobe/adbp932b.exe (adbp932b.exe).
(Read first the instructions before updating the system)
“Your urgent attention is most appreciated,
“Rxxxxxx Bxxxxxx
Adobe Risk Management
xxx Park Avenue
San Jose, CA 95xxx-xxxx
Tel: xxx-xxx-3932
xxxxxx@adobe.com”
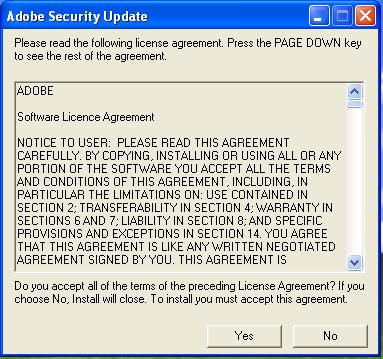
The executable tries to inject code into explorer.exe under the guise of an Adobe update (including a phony license agreement, below):
The main file is a self extracting EXE that drops code in TempIXP000.TMP as UNINST~2.EXE.
It has been associated with the iframedollars (rogue security product) primary downloader and about six other secondary’s which were first found in April. VIPRE detects it as Trojan.Win32.Generic.pak!cobra. Only seven out of 41 anti-virus products on Virus Total detect it.
Trojan.Win32.Generic.pak!cobra was the third most common detection in May according to Sunbelt’s ThreatNet statistics.
Thanks David, Patrick and Dodi
Tom Kelchner