F-Secure reports:
“Spyware vendor Mindset Interactive shuts down their business
Favoriteman and NetPal nuisances have after several years stopped. The company behind it has closed and we can report they have moved out of their company offices. All related web servers are unreachable and the already distributed Spyware no longer functions.
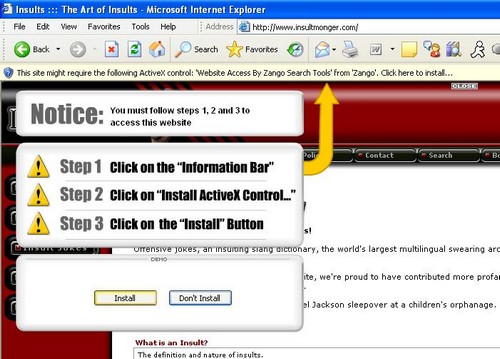
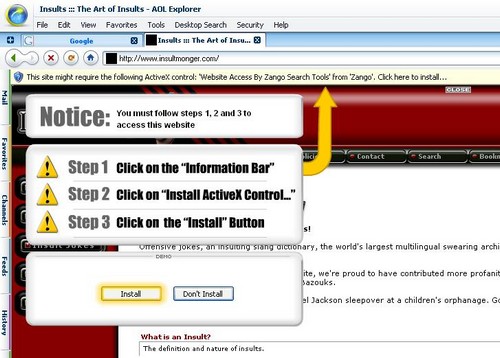
Like many Spyware vendors, Mindset Interactive has used multiple names to distribute their Spyware. That is why termination of the company behind it is such a positive turn.
Mindset Interactive was behind Favioriteman also known as F1Organizer, ATPartners, SpyAssult and Window Help 4 Smart Browsing. They also constructed NetPal, which had a massive numbers of games as distribution channels.
F-Secure will keep Favoriteman and NetPal in detection to clean out the final filth.”
Actually, our research indicates that the death knell may not have clanged loudly, at least not yet.
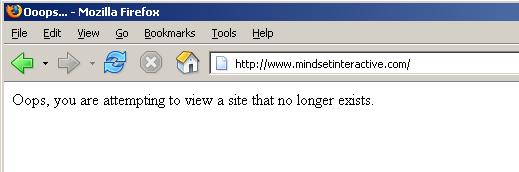
Pinging addictivetechnologies.com (207.182.237.210) and mindsetinteractive.com (207.182.237.210) shows that the site is unavailable and whois for that IP number is under the hosting company, Velocity Networks.
But let’s look at some more:
IP:207.182.237.210
vistainteractivemedia.com
10 Corporate Park, Suite 315
Irvine, CA 92612
IP: 207.182.237.210
Mindset Interactive
5 Corporate Park Suite 160
Irvine, CA 92606
Here are the websites we can find associated with Mindset or Mindset executive Scott Walker
Dead sites:
Addictivetechnologies.net
F1organizer.com
F1organizer.net
Favorites1.com
Favorites1.net
Addictivetechnologies.com
Mindseti.com
Mindsetinteractive.com
Freebiesrus.com
But…
Live sites!
Idealbrowser.com
Broadnetsoftware.com
Broadspring.com
Idealproductgroup.com
Vistainteractivemedia.com
Vistainteractivemedia.net
Flashgamejunkie.com
Flashgamesjunkie.com
Idealringtones.com
searchenginebar.com
Reflexivesearch.com
From what we can tell, they still own the sites and they still are assigned IP addresses. Last year MindSetInteractive put up a sign that they were changing to Vistinteractivemedia. They also have Broadspring.com along with Vistainteractivemedia that is running the RX toolbar bundled in Kazaa alongside Best Offers.
Finally,according to this site, Aadcom was listed as part of the MindSet Interactive Group during their days with Direct-Revenue. Today a whois shows an email address for vistainteractivemedia and they share the same DNS servers and IP range.
In short, not so fast…
Spyware researchers — contact me offline for more detailed information if you need it.
Alex Eckelberry
(Thanks to our Patrick Jordan for his extensive work on this project!)