A while back, AskJeeves approached us to have their products delisted from the CounterSpy database.
There are a number of antispyware programs that list AskJeeves toolbars and a number that don’t. You can see the current status of AskJeeves detections here. It’s a mixed bag: Companies that don’t detect any AskJeeves programs are Lavasoft, Microsoft, WebRoot, PC Tools and FBM Software. Companies that do are Sunbelt, McAfee, Computer Associates, Spybot, Tenebril, Trend and Facetime
The AskJeeves question is not new. See this article in Newsweek in June and Ben Edelman’s discussion in May. Clearly, there’s room for a definitive answer, especially with business customers who buy antispyware programs.
So we proceeded to perform a comprehensive study of the AskJeeves programs in question. That study can be found here.
The AskJeeves programs referred to are all search tools that are added to your browser: MySearch Bar, MyWay Speedbar and MyWeb Search and their variants (AskJeeves re-brands or makes changes to these toolbars, to come up with types of toolbars that offer free cursors, screen savers, etc.).
What we found in some cases was troubling. Now, don’t get us wrong: The AskJeeves toolbars are NOT adware or spyware. They are arguably relatively innocuous additions to the browser. However, methods of current and past distribution, notice and disclosure are of concern. After reviewing the results, one has to ask oneself the question: If an AskJeeves toolbar is on a user’s system, did they really want it on there in the first place? Did they even know they were getting it?
When AskJeeves’ products are downloaded and installed directly from AskJeeves’ own web sites, notice and disclosure of the products and their functionality is generally good, though there is room for improvement in some cases (e.g., the failure to describe FunWeb Products as browser toolbars). However, several of AskJeeves’ products are plagued with poor installation practices when distributed by third-parties or when advertised at third-party web sites. Putting aside concerns about aggressive advertising practices (treated at length in the whitepaper), we found issues with the following:
Poor notice and disclosure with software bundlers. AskJeeves bundling in software bundlers like Grokster and Kazaa, where poor notice and disclosure are provided. The worst case we observed was a bundle with the Bald Eagle Screensaver which installed MyGlobalSearch Toolbar even after the user cancelled the installation. You can see the video taken August 28th of exactly this occurring here.
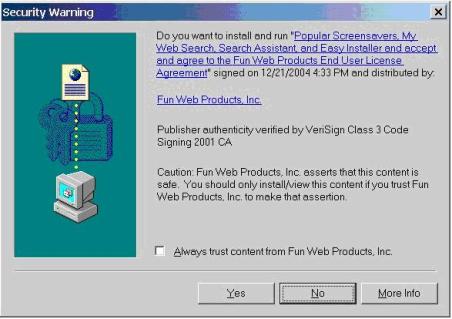
Installation through ActiveX controls.While Internet Explorer’s user notification about ActiveX controls has improved measurably since the release XP Service Pack 2, there is still an issue with these types of downloads. AskJeeves’ products have been installed through automated ActiveX installations that initiate when users land on third-party web pages. These ActiveX popups, which launch without warning in arguably confusing circumstances, can prove bewildering to users. For example, this ActiveX popup was found on Smiley Central:
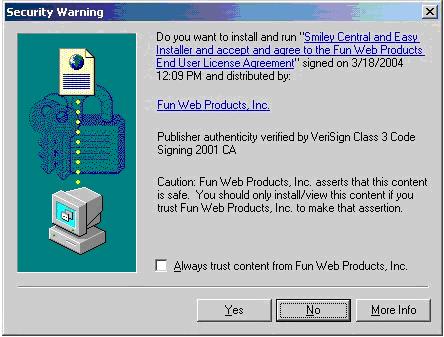
Examples of ActiveX installations of AskJeeves’ software include IOWrestling.com (Sept. 2004), Letssingit.com (Apr. 2005), and Prowrestling.com (Apr. 2005).
Past installation through Windows Media Player exploit. While not as relevant today, an issue several months ago was the installation of software through Windows Media Player files (the Microsoft Digital Rights Management feature, or DRM, allowed publishers to re-direct viewers of a file to a 3rd party website — this was being used by unscrupulous vendors to attempt spyware/adware installations).
In testing during January 2005 with one such WMP file (aria_giovanni_full7.wmv), an ActiveX install prompt for Popular Screensavers/MyWebSearch toolbar was encountered amidst a series of other installation prompts for XXXToolbar (IST), “Free Jenna Jameson Screensaver” (ABetterInternet), and “Video Secret & Chat” (ABetterInternet).
Force installs through security exploits. By far the worst documented installation practices for AskJeeves’ products have been the past force-installs of AskJeeves toolbars through security exploits, as reported by Ben Edelman back in May.
Changes to the CounterSpy database.
Products that have been marked by problematic installation practices through third-party advertising and distribution include My Global Search, My Global Search, My Search Bar, Need2Find Toolbar, and My Speedbar; as well as variants of MyWebSearch Toolbar which include CursorMania, FunBuddyIcons, HistorySwatter, MyFunCards, My Mail Signature, My Mail Stationary, PopSwatter, Popular Screensavers and Smiley Central. These will all be listed in the CounterSpy database.
We found no issues with AskJeeves Bar, Excite Speedbar, and iWon Co-Pilot and hence they will not be included unless unless and until hard evidence emerges that these products are being distributed or advertised in ways that trip Sunbelt’s Listing Criteria, as AskJeeves’ other products do.
My Global Search or Need2Find toolbars are not currently detected and will be added, and a number of housekeeping changes will be made to the database to put all the offending programs into the correct taxonomy and labeling standards we have established.
Our whitepaper goes into great and exhaustive detail on all of these points, and I would recommend reading it here.
eWeek writes about it here. Internet Week here.
Alex Eckelberry
Addendum: AskJeeves says that with the FasterXP install documented in the whitepaper, the toolbar “implodes” after installation. That’s true. After installed, the toolbar’s buttons are disabled and it only has an “uninstall” button.