Grokster had pulled their adware advertising supported version, offering only a paid-for version. Now, the adware advertising supported version is back, offering loads of fun for all users.
I thought maybe Grokster got religion. After all, they lost with the Supreme Court. People have been upset about adware in Grokster for quite some time.
Wrong.
First, the text on the free download page is a totally confusing. It says: “In order to download the free version of Grokster, you must agree to install all of the adware listed below during the Grokster install” (it also classifies this adware as “valuable downloadable software”).
However, you can un-check the boxes, which gives you the impression that you can take these little adware components off.
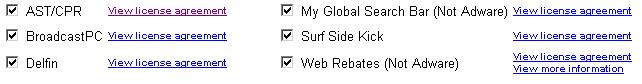
Well, uncheck away, because it doesn’t seem to matter. There’s this little thing at the end of the page:
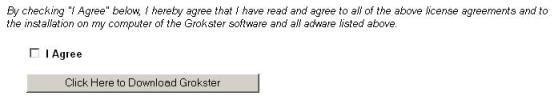
Now, here’s what’s odd. It doesn’t seem to actually install these components, even though it tells you it will. You get other stuff though (like WinFixer), but not nearly as much as you see above.
Maybe they want to leave that as an option in the future.
At any rate, after the install you get presented with some pop-up about installing Crystal Palace. You also get directed to a start page (http://client(dot)grokster(dot)com/us/start/?c=af&ver=265 which instantly pops up an installer for another piece of adware.
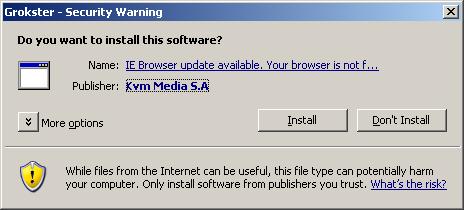
Going back to that same page, you get an active/x prompt (which looks like this under XP SP2)

Clearly, they have a bit of a ways to go…A lot of the problem seems to revolve around the client.grokster site.
Maybe it doesn’t matter, because prominent images linking to Music pages goes to Mediafeast, which is well, out of business.
Alex