They contacted us with a cease and desist letter, asking us to change the naming of their adware programs in their database.
So be it. Here is our response.
Alex
(Still scratching my head)
The Great Years: 2004-2010
They contacted us with a cease and desist letter, asking us to change the naming of their adware programs in their database.
So be it. Here is our response.
Alex
(Still scratching my head)
Click here . Note that this may only be a temporary measure.
Ben Edelman documented some of their practices with Truste here and here.
To wit:
The TRUSTe ‘Click-to-Verify’ seal was placed throughout the site, and, where it appeared on the privacy statement, had not been properly implemented. TRUSTe requires that the ‘Click-to-Verify’ seal may only be placed at the top of the privacy statement and must link to the TRUSTe validation link.
The site was violating restrictions on the TRUSTe seal appearing on any pages offering downloadable software.
Finally, when used on a Web page, the TRUSTe Trust Mark must always link to the TRUSTe-approved privacy statement. On this Web site this was not always the case.
Alex
(Thanks to Ben Edelman)
A new antispyware coalition has been announced.
Before reading anything more, remember that the primary people screaming for standards in defining spyware are the adware vendors.
I was immediately suspicious at the spyware conference a few weeks ago when all the spyware vendors were talking about “the need to create standards”, and a journalist I met kept saying to me that there needs to be standards. “Oh no,” I thought. “They’d gotten to him.”
Ok, so this one doesn’t have any spyware/adware guys in it, thankfully (unlike the past attempt at a coalition, COAST).
But I’m concerned. One reason is that spyware/adware vendors don’t like to be listed in antispyware product databases. It means end-users uninstall their stuff. They do legal threats against people like us. And if there is some new standard that has been agreed to, all they have to do is simply point to the standard. It gives them a way out.
It’s also what’s a bit unnerving about some of the upcoming legislation. Same reason. “Your application listed us as spyware but we don’t fall into the definitions in the law”.
The idea of a democratic process defining something as sensitive as spyware is dangerous. Spyware fighting is not a consensus-based approach.
So their charter:
…the Anti-Spyware Coalition, plans to publish proposed guidelines later this summer that define spyware, best practices for desktop software development, and a common lexicon, people involved with the group told CNET News.com.”
Is this a path to hell?
We are presently standing aside on this coalition. We are concerned about our ability to serve our consumer and enterprise customers the way they want to be treated–not based on agreements between other antispyware vendors.
They want standards? Read our listing criteria , arguably the best set of standards in the business. I mean it. Read them and see for yourself. We’ve covered the bases. Just copy and paste, you’ve got your standards. Move on.
This isn’t Betamax vs. VHS. If I label abetterinternet as “directrevenue.abetterinternet” vs. “dr.abetterinineter”, who cares? It’s not important. It’s just a naming standard.
Or a better example: If my database flags Hotbar as a threat, but another vendor doesn’t, who is the better vendor? The consumer, armed with independent reviews by authoritative publications, makes that choice.
The problem is spyware/adware definitions have a lot of gray areas. It’s not like viruses, which are black and white.
Here’s an example. Look who has delisted Hotbar (according to Hotbar): Microsoft. Lavasoft. SpywareDoctor. McAfee. Panda.
Then look at the comments from users when we got our Cease and Desist letter from Hotbar. These people are pissed (and see our response to Hotbar here.)
Who served their customers best by giving in to Hotbar’s pathetic threats?
Then look at who is on the new antispyware coalition:
Members:
Aluria Software
America Online
Computer Associates International (PestPatrol)
EarthLink
Hewlett-Packard
Lavasoft (Ad-Aware)
McAfee
Microsoft
Safer Networking (Spybot)
Symantec
Tenebril
Trend Micro
Webroot Software
Yahoo
Business Software Alliance
Cyber Security Industry Alliance
Also involved:
National Consumer Law Center
Canadian Internet Policy and Public Interest Clinic
Berkeley Center for Law & Technology
Consumers Union
Center for Democracy & Technology
Missing are some of the major superstars of antispyware research. Ben Edelman. Eric Howes and Suzi Turner of Spyware Warrior. Wayne Porter. Andrew Clover of Doxdesk . Paperghost. Dave Methvin of PC Pitstop. Jan 2006 update: A lot has changed since I wrote this post. Many of these folks mentioned will be panelists at the upcoming ASC conference in February 2006. See the ASC webpage for all the latest news.
Now, that’s not to invalidiate all the people who are members. There are some major league players that I have tremendous respect for, people like Ari Schwarts of the CDT, and the people at Webroot. But is this just it?
Maybe I’m too much of a hardliner. Yes, this fight is very real and very visceral for me. I don’t know how many other software company CEOs have spent late nights de-infesting a friend’s machine. I have and I’m pissed. And my primary business is selling to the enterprise, and they have decidedly hard views on security threats.
I wish the best to any group trying to solve the mess of spyware. We will stand by the side and see what happens.
Alex Eckelberry
An interesting and somewhat depressing report by the Annenberg Public Policy Center . Read it here.
The study, entitled “Open to Exploitation: American Shoppers Online and Offline“, has tidbits like this:
The study indicates that many adults who use the internet believe incorrectly that laws prevent online and offline stores from selling their personal information.
They also incorrectly believe that stores cannot charge them different prices based on what they know about them. Most other internet-using adults admit that they simply don’t know whether or not laws protect them.
The survey further reveals that the majority of adults who use the internet do not know where to turn for help if their personal information is used illegally online or offline.”
Then check these stats out:
• 75% do not know the correct response—false—to the statement, “When a website has a privacy policy, it means the site will not share my information with other websites and companies.”
• 64% of American adults who have used the internet recently do not know it is legal for “an online store to charge different people different prices at the same time of day.” 71% don’t know it is legal for an offline store to do that.
(If you’ve ever shopped at Dell, you know what I mean. We had one situation recently where I was shopping a laptop with a co-worker, who happened to be on another machine. His price was $50 higher than mine!)
• 68% of American adults who have used the internet in the past month believe incorrectly that “a site such as Expedia or Orbitz that compares prices on different airlines must include the lowest airline prices.”
• 49% could not detect illegal “phishing”—the activity where crooks posing as banks send emails to consumers that ask them to click on a link wanting them to verify their account.
• Consumers are also vulnerable to subtle forms of exploitation online and offline.
• 72% do not know that charities are allowed to sell their names to other charities even without permission.
• 64% do not know that a supermarket is allowed to sell other companies information about what they buy.
They suggest three policy initiatives:
• The Federal Trade Commission should require websites to drop the label Privacy Policy and replace it with Using Your Information.
• U.S. school systems—from elementary through high school—must develop curricula that tightly integrate consumer education and media literacy.
• The government should require retailers to disclose specifically what data they have collected about individual customers as well as when and how they use those data to influence interactions with them.
Worth a read. And as always, caveat emptor.
Alex Eckelberry
(Thanks to BeSpecific)
This is a redirect page. To get to the original post, click here.
Paul Roberts of eWeek writes about the AOL Netscape 8 Trust Rating.
In a surprising move, Sean Sundwall, Senior Corporate PR Manager at Microsoft, is taking the job of Director of Corporate Communications at 180Solutions/Zango.com.
Yup. It’s really true. He starts next Monday.
Alex Eckelberry
An update of my prior blog on this issue.
The LA Times recently wrote (reg. required) about more privacy consequences of this law which will have a significant effect on your privacy.
From the article:
“But once the law takes full effect three years from now, it will also give many more bureaucrats access to personal information on people nationwide. And it will add more data to each file  including digital copies of documents with birth and address information.
“It’s a gigantic treasure trove for those who are bent on obtaining data for the purpose of creating fake identities,” said Beth Givens of the nonprofit Privacy Rights Clearinghouse. Armed with a stranger’s name, Social Security number and date of birth, it’s not hard for fraudsters to take out bogus loans that can wreck a victim’s credit record.
Critics predict the standardization will prompt many more merchants to scan customer licenses and then pass on the information to such data brokers as ChoicePoint Inc. and LexisNexis. The databases of both ChoicePoint and LexisNexis have been exploited by identity thieves.”
The large amount of personal information that has already been compromised through the LexisNexis and Choicepoint breaches is disturbing enough. So we have a law which might, ironically, make it easier for these breaches to occur.
To the commenter on my prior blog who extolled the benefits of ID cards, I urge you to enjoy life in your country. In the States, privacy advocates are actually trying to hold on to the last of our rapidly disappearing freedoms.
Alex
Read it here.
Alex
Hot off the presses: Ben Edelman just posted a detailed writeup.
Why the big deal? AOL Netscape (nee Netscape) is assigning a trust rating based on certifications. Certifications are useless for trust ratings, because all they do is certify what they are supposed to certify–such as “is the traffic in a SSL browser session secure?”. They are not ways to actually determine the validity of a site in general.
In short, the new Netscape 8 apparently will assign a trust rating to sites like abbeterinternet.com, hotbar.com, Ezula.com, mywebsearch.com and others.
Alex
(Part one in an informal series on the absolute uselessness of current certifcation practices…more later).

The new Netscape has a trust rating, explained here.
According to their website:
The Netscape Browser is equipped with a web site rating system called “Trust Ratings” which is driven by lists of sites provided by our trusted security partners. The intent of this system is to automate browser security and site compatibility on an automated basis by identifying the following:
• Verified sites which are safe for entering personal and/or financial information
• Malicious sites intended to steal your information (aka Phishing sites)
• Sites which attempt to inject malicious programs or code onto your system (Spyware, Adware, Trojans, and viruses)
Looking a bit further, one sees their “Trusted Security Partners”: Verisign (for light reading on Verisign, see Ben Edelman’s writeup here), Truste (whose “sealholder” list includes abetterinternet.com, direct-revenue.com and others), and Paretologic (makers of Xofspy, a former member of the Rogue/Suspect Spyware list).
Update: Suzi at SpywareWarrior.com just ran with the story. You can see her blog entry here.
Alex
(Thanks Suzi, Eric, Ben)
This just out. Morgan Stanley’s report on the spyware market. Read it here.
Note: We have not reviewed the material to determine accuracy, a quintillion disclaimers apply, etc.
Abetterinternet has just send us a Cease and Desist letter. You can see it here.
As with all of these types of legal issues, I have fowarded it to our high priced lawyers and a response will be sent in due course.
The letter basically asks us not to label BetterInternet (aka Direct Revenue) as spyware, but instead list it as adware.
Oh, and for those waiting for our response to Hotbar, we should have a response up by the end of the week.
Alex Eckelberry
If you haven’t read this story in the Washington Post, it’s worth a quick read.
It went something like this:
-A small group of hackers sent out a bunch of porn spam with a virus/keylogger attached.
-A police officer opened one of the emails, and then subsequently logged onto Seisint, a LexisNexis subsidiary. Of course, the keylogger was on the system and everything the officer did was recorded.
Then:
“The young hacker said the group members then created a series of sub-accounts using the police department’s name and billing information. Over several days, the hacker said the group looked up thousands of names in the database, including friends and celebrities. The law enforcement source said the group eventually began selling Social Security numbers and other sensitive consumer information to a ring of identity thieves in California. washingtonpost.com has not been able to reach the young source to seek comment about the sale of personal information.”
Then check this out:
“LexisNexis disclosed on March 9 that records on 32,000 individuals were downloaded by an unknown person or persons who gained access to the company’s database using compromised user accounts. A month later, the company said it determined that 310,000 personal records had been accessed over a series of weeks…
What’s the lesson? This is basic security!! Everything that could have stopped this attack is commercially available and not even that expensive. A friggin free desktop firewall with inbound and outband protection would have obviated most, if not all of the breach. Layer that with a good AV with robust attachment filters.
Then throw in some employee training about social engineering (i.e. “don’t open attachments unless they are from a trusted, known source that you know is supposed to be sending something”, etc.).
Alex Eckelberry
(Thanks to BeSpecific)
Word is spreading that Sunbelt is being attacked by Hotbar.
Lots of interesting comments from our previous post.
Our crack legal team will be writing a response, which we will post for public viewing in the next week or so. For an example of a prior letter, see our letter to iDownload.
However, some new developments.
1. We found this action by Hotbar against Lavasoft. It is unknown what happened, but it possibly explains this snippet from their letter to us:
2. Spyware guru Ben Edelman has just done a detailed look at Hotbar’s installation practices.
Quote:
“This article examines one such installation, its (purported) license agreement, and its effects. Notable characteristics:
• Installation at a site targeting kids.
• License agreement not affirmatively shown. Unhelpful section headings, convoluted language.
• Installation confirmation screen lacks a button or option to cancel installation.
• Intrusive advertising, not specifically disclosed in prior on-screen text, including ads in toolbars, pop-ups, pop-unders, auto-opening sidebars, and desktop icons.”
Alex Eckelberry
NOTICE: Hotbar® and Hotbar.com® are Reg. U.S. Pat & TM Off.
Many haven’t seen our research paper on this matter we wrote back in March. Here is a link to our whitepaper on Firefox.
In summary, over the past few months security experts have speculated that we could see new spyware and adware crafted for Mozilla Firefox
Until now most of this speculation has centered on the potential for security holes in Firefox that could be exploited by spyware and adware creators. But such speculation is arguably misguided. In fact, we already have seen instances of spyware and adware that can be installed through Mozilla Firefox.
These cases have only received little attention, however, largely because researchers have been too focused on security exploits instead of the more run-of-the-mill methods through which spyware and adware are typically delivered to users’ desktops: namely, social engineering techniques that spring unwanted software on confused users who aren’t careful enough about what they click.
Alex Eckelberry
Hotbar sent us a Cease and Desist letter yesterday. Read it here.
I have forwarded it to our high-priced lawyers and an appropriate response will be filed in due course.
Of course, we won’t remove them from our database under any circumstances. Clearly, the folks at Hotbar didn’t read our listing critieria.
Here’s what’s odd about all of this. Hotbar is what we label “low-risk adware”. We list them in our database, we display them in the scan results, but we tell the user “This is not a big deal” and we put the default action as “ignore” (as opposed to “remove” or “quarantine”). While Hotbar is clearly adware, it is not nearly as destructive to the system as something like CoolWebSearch.
So we are telling the user it’s on their system, but we’re letting the user decide if we should remove it or not.
Now check out this little snipped from their letter:
Click to enlarge
As most people know, we get spyware database updates from Microsoft. We did notice a while back that Microsoft had removed Hotbar, but we didn’t remove them from our version of the database. We figured Hotbar had gone after them and now we can see that it looks like they really did.
You know, you can get farther with a bit of with molasses than a lot of vinegar.
Contrast Hotbar’s vehement attack with WeatherBug’s kindler, gentler style. The WeatherBug Chief Privacy Officer Dan O’Connell and I had a respectful interchange (and we both blogged on the matter of listing WeatherBug). They didn’t like the fact that we were listing them in our database, but respected our position. While we continue to list them, at WeatherBug’s request, we are making changes in our UI to help users understand that having WeatherBug is not the end of the world.
In other words, a little bit of molasses sure is better than a lot of vinegar.
Alex Eckelberry
If you’re a privacy advocate, you’re familiar with the various analogs for slow destruction of civil liberties. The light-dimmer effect is one, something I heard years ago from Arthur Maren.
Here’s how it works: You go into a room, and someone turns the light-dimmer down just a few notches every few minutes. After a while, it’s dark, and you haven’t even noticed what happened.
And so it goes with our civil liberties and our privacy in the US. The dimmer just got turned a notch.
From the News.com article:
“The so-called Real ID Act now heads to President Bush, who is expected to sign the bill into law this month. Its backers, including the Bush administration, say it’s needed to stop illegal immigrants from obtaining drivers’ licenses.
If the act’s mandates take effect in May 2008, as expected, Americans will be required to obtain federally approved ID cards with “machine readable technology” that abides by Department of Homeland Security specifications. Anyone without such an ID card will be effectively prohibited from traveling by air or Amtrak, opening a bank account, or entering federal buildings.“
This thing was sleazily put into a larger bill.
Wired article here.
Alex Eckelberry
Ari Schwartz of the CDT is testifying before the Senate Committee on Commerce, Science, and Transportation on “Spyware” today. The link to the webcast is here.
He has some great information in that testimony. If you’re a dedicated spyware fighter, it’s worth scanning. Those who were at the CNet Antispyware Workshop will be familiar with much of this information.
But briefly, here are some pics from the testimony.
It all starts with this simple model:
Advertisers (either directly or through brokers) pay money to adware companies for impressions or clicks or whatever. Distributors get the adware on people’s machines.
Like this:

Click to enlarge
(Image courtesy of the CDT)
So here is another theoretical slide as to how that works. It looks monstrously complicated, but it’s still based off the same simple idea. Advertisers (either directly or through brokers) pay money to adware companies. Distributors get the adware on people’s machines.
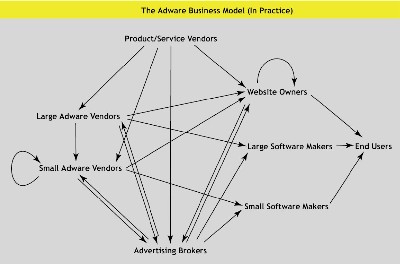
Click to enlarge
(Image courtesy of the CDT)
It is Byzantine but understandable if you look at it long enough.
Now, this slide shows the truly pernicious behavior of Seismic Entertainment (Seismic is being sued by the FTC).
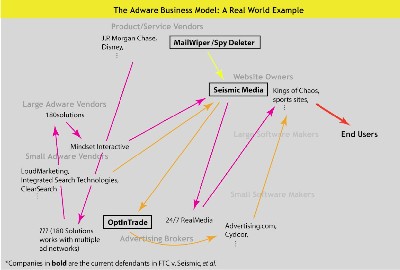
Click to enlarge
(Image courtesy of the CDT)
What was Seismic doing? Nasty, nasty, nasty stealth installs.
Ok, those with weak stomachs turn away (don’t worry, it’s not nasty pictures, it’s just typical run-of-the-mill criminality exposed):
Here is an email from Seismic:
From:
To: jared@optintrade.com
Date: Sat, Mar-6-2004 4:51 PM
Subject: I DID IT
I figured out a way to install an exe without any user interaction. This is the time to make the
$$$ while we can.
Here is another fun one:
From:
To: jared@optintrade.com
Date: Fri, Nov-28-2003 12:37 PM
Subject: strategy
I do my sneaky shit with adv.com today through Sunday — everyone’s off anyway…. You
then send an email to your contact early Monday AM saying the advertiser was unethical and
pulled a switch and you are no longer doing business with them… Then we stop buying
adv.com through you in any way.
All of these pics and the emails I got from Ari Schwartz’ testimony. (Thanks Suzi for forwarding the link).
Hats off to the CDT and to Ari for this.
Alex