DC Universe Online is an upcoming MMORPG for Playstation 3 and PC which lets you punish evildoers alongside the likes of Batman, Superman and a large collection of other DC Comics superheroes. As you might imagine, interest levels are high and this is turning into an attractive piece of bait for scammers everywhere.
I mean, one look at the fancypants cinematic trailer and you can see why people are getting excited over it:
As a result, there are numerous Youtube videos (what else!) and blogs popping up promising entry to the Beta test. Here’s just a few from the last day or so, there are many more:
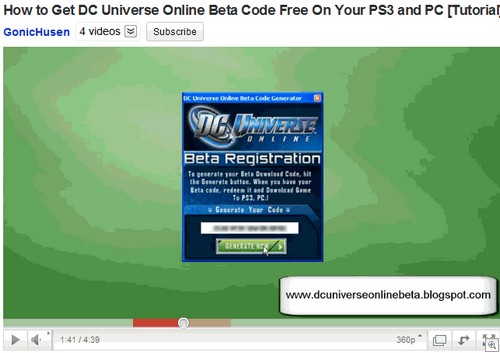
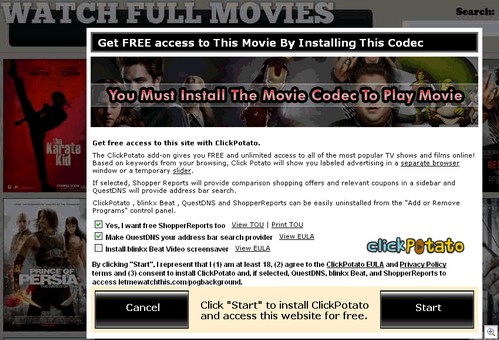
Almost all of the videos point to the same spamblog, although we’re now seeing the contents of said blog being lifted and used by other scammers (which link to their own downloads, naturally). Here’s a screenshot of a typical video:
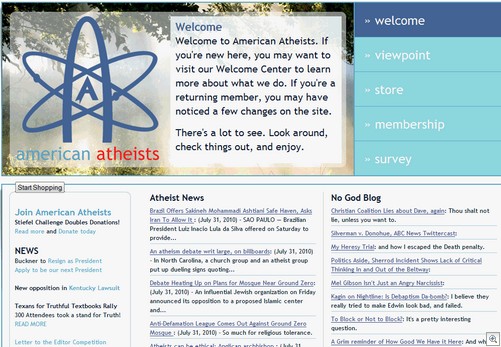
I did consider embedding one of the videos, but as most of them autoplay bad 90s techno or feature some rapper guy singing about his 40 ounce and his bling bling hubcaps I thought the screenshot was the safer option. Anyway, the main spamblog here is dcuniverseonlinebeta(dot)blogspot(dot)com which looks like this:
Due to increased promotion, the site has had 52 visits today with a total of 357 visitors since the site launched – I imagine that number will continue to rise. What they want you to do is download a “DC Universe Online Beta Registration” program, which generates a code to give access to the Beta testing.
If you want to place your bets that this is a fakeout, now is the time to do it.
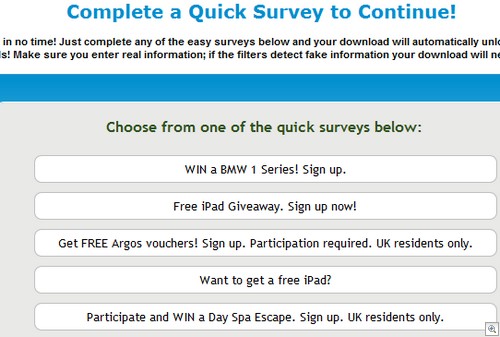
Hitting the download link takes you to that favourite of scammers everywhere, the multiple survey popup:
Hand over your personal information to a random third party, and you’ll be able to download this executable:

Oh, the excitement. Fire it up and you’re presented with this admittedly slick looking interface:
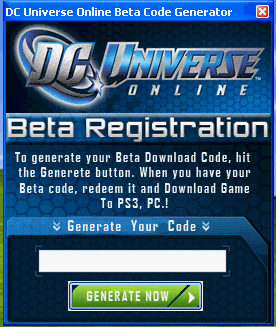
Hitting “Generate Code” gives you a Beta key that is absolutely the most useless Beta key in the history of anything. All the program does is display the same short list of non random codes over and over again, every time you fire it up. Predictably, this doesn’t help very much when trying to join the Beta.
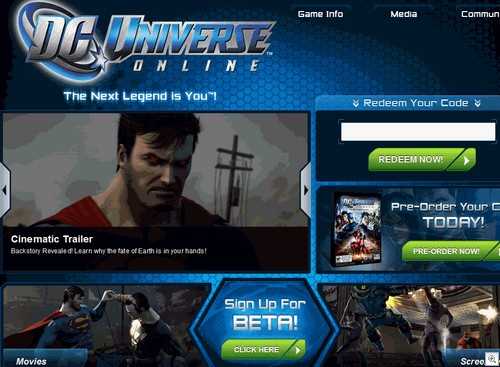
Cue a lot of soon to be dashed hopes and signing up on the DC Universe Online website:
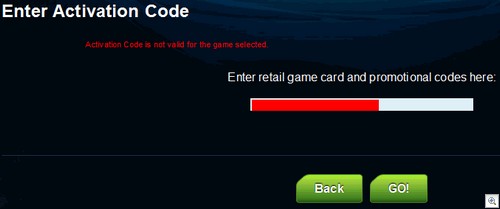
“Redeem your code”. Well, if we had a code that actually worked we might get somewhere. As it is, prepare to wave goodbye to your dreams of punching Lex Luthor in the face:
ADVANTAGE: EVIL.
Anything that takes place after you’ve filled in the survey is just filler – the story ends once you’ve filled in a survey and the scammer has generated affiliate cash. All you’re left with is a (non infectious) fake application, a bunch of non working Beta keys and a grumpy Activation Code page telling you off for repeatedly entering fake codes.
You have to admire the chutzpah of one particular scammer who claims to have 10 whole sets of codes for you to download and use. Amazingly (or not) each and every one is protected by a survey.
Click to Enlarge
Gee, I wonder if those codes are fake too.
You don’t have to be Batman to work out that random promises of Beta keys involving dubious spamblogs and executables are not going to deliver. Other downloads further down the line could easily be infection files instead of fake code generators, and at the very least you’re giving underserved cash to people who by rights should be tasting the business end of Superman’s fist.
Up, up and run away…
Christopher Boyd