We hear so much about stealth tactics, data theft and covert ops where malware is concerned these days that we often forget about the time when it was more about how many popup windows the attacker could throw onto the screen along with a couple of dancing monkeys and a spangly toolbar.
Here, then, is something a little retro that takes a form of infection more known for stealth (parite) and turns it into an overt rip roaring rampage of revenge, but mostly broken computers.
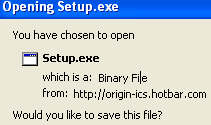
Promoted as a music player based around popular cartoon Aqua Teen Hunger Force, the following file(Win32.booty.exe) should be avoided at all costs:
Shortly after running the executable, hidden files and folders start to scatter themselves liberally across the PC in both the System32 Folder and the Temp Directory – in this case, 10.tmp containing a file called but!.exe, thrown together with the aid of what was probably the HotFusion file binder:
From there, another folder then appears (called 12.tmp) which contains the main payload files:
Worm.exe, Zombie.bat and chimes.wav.
So far, this is reasonably similar to a regular Parite infection (two folders in the temp directory, the promise of wormy action to come) but at this point we start to move away from the notion of Parite stealth to…well….take a look for yourselves.
Let’s check out Zombie.bat:
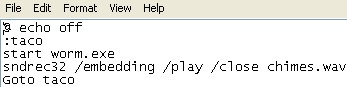
As you can see, the commands tell Worm.exe to spring into action and the .wav file (“Chimes”) starts to play.
What happens now?
Well, we prepared a little video demonstration for you (there’s sound, so you might want to put on some headphones):
http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/paritebooty/
….yes, it made no sense to us either. The Task Bar vanishes and the victim loses the ability to open up Task Manager to kill the rogue processes. Any programs opened up once the infection takes hold will generally auto close seconds after opening.
Meanwhile, a file called BoOtY_Call starts spreading itself into every folder it can find, with the intention of jamming up the machine until it collapses in a crying, blubbering heap – with a song blasting out the joys of “booty” through your speakers, naturally.

If the victim manages to open up a folder and go on a deletion rampage, it doesn’t matter…BoOtY_Call keeps respawning and eventually triumphs in a blaze of malware glory.
This is pretty malicious stuff and throwing in a song about loving booty while a similarly named file proceeds to drive a wrecking ball through your hard drive is a surreal and comical contrast to the otherwise ruthless beating the PC is taking.
Given my earlier ramble, you may not be surprised to find we detect this as a variant of Parite (an infection that traditionally tries to infect EXEs and SCR files on PCs in a very quiet fashion, losing you hard drive space in the process), which is an interesting twist given how, er, loud this is. Probably not what the creators of Parite had in mind when they came up with it, but hey – that’s evolution, baby.
Sort of…
Chris Boyd