It’s the time of year to make predictions. I only have one: in 2010, governments around the world will BEGIN to increase their efforts to do something about the massive malware threat that every Internet user on the planet faces.
It’s going to be controversial and difficult legally and technically. It’s going to cost serious tax money, political capital and diplomatic work to counter this crime wave that is like nothing the world has ever known.
At this point, 90 percent of email is spam, organized crime groups commonly siphon cash from the bank accounts of individuals and businesses on other continents, search engines are regularly harnessed to lure those browsing the web into purchasing fake security products and malicious applications are being created faster than legitimate software.
China has made two huge, stumbling attempts. One, Green Dam-Youth Escort, unfortunately was mixed up with state censorship and sullied by a sleazy company whose idea of software development was “borrowing” a U.S. company’s code. The other, China’s attempt to require “on-paper” domain registration and limiting them to registered businesses, possibly could make it harder to set up malicious sites, but, it too is drastically flawed.
The U.S. Federal Trade Commission has had some noteworthy successes against spammers. European governments are seriously going after digital pirates and Nigeria has arrested a few dozen 419 scammers and promises a lot more.
So, there is motion.
. . .
There is no shortage of predictions this month.
Other people in the computer security sector have been making a lot more predictions and posting them. I thought it would be interesting to sort them by topic and compare them. I’ve summarized them as briefly as possible and listed the URLs of the original texts at the bottom of this blog post.
Application level attacks
— Adobe software, especially Acrobat Reader and Flash, will become top hacking targets. [McAfee]
Banking Trojans
— Banking Trojans will become more sophisticated. [McAfee]
Botnets
— Fast flux botnets will increase [Symantec]
— Botnet controllers will switch to less vulnerable methods for command-and-control (such as peer-to-peer networks). [McAfee]
— Botnets are becoming more self-sufficient. [WebUser]
— “Malware will not evolve.” Botnets will not get any more sophisticated, there will be no mass outbreaks and highly targeted attacks will remain on the fringe. [Cooper/Verizon]
— There will be a shift in botnet-related crime from black markets to grey markets with more partner programs for DoS attacks and malware distribution. [Kaspersky]
CAPTCHA
— CAPTCHA technology will improve. Businesses in emerging economies will hire people to defeat it and generate accounts for spammers. [Symantec]
Cyber crime
— There will be more successes in the fight against all forms of cybercrime in 2010. [McAfee]
— Breaches will increase, especially against mid-sized businesses. [Cooper/Verizon]
— Microsoft’s legal efforts will pay off with at least one major arrest. [Cooper/Verizon]
— China will continue to be blamed for everything. [Cooper/Verizon]
File sharing networks
— There will be a shift from attacks via the web and applications to file sharing networks. [Kaspersky]
Malware development
— Malware will become more sophisticated and remain one step ahead of increasingly sophisticated security programs that will be developed to deal with it. [Kaspersky]
Operating system exploitation trends
— Mac and mobile malware will increase. [Symantec]
— HTML 5 and Google Chrome OS will make opportunities for malware writers. [McAfee]
— Google Wave will be exploited extensively but Google’s Chrome OS will not. [Kaspersky]
— Specialized malware will increase (i.e. ATMs, voting machines, public telephone voting connected with reality television shows and competitions). [Symantec]
— iPhone and Android (and related third-party software) will be malware targets. [Kaspersky]
— Nothing significant will happen to non-PC devices such as telephones, PDAs and Macs. [Cooper/Verizon]
Phishing
— Spear phishing will increase. [McAfee]
— URL-shortening services will be used extensively for phishing. [Symantec]
Reputation-based security
— Reputation-based security will come into prominence. [Symantec]
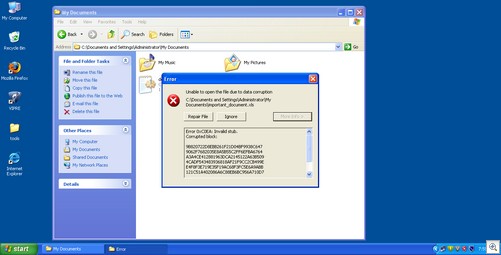
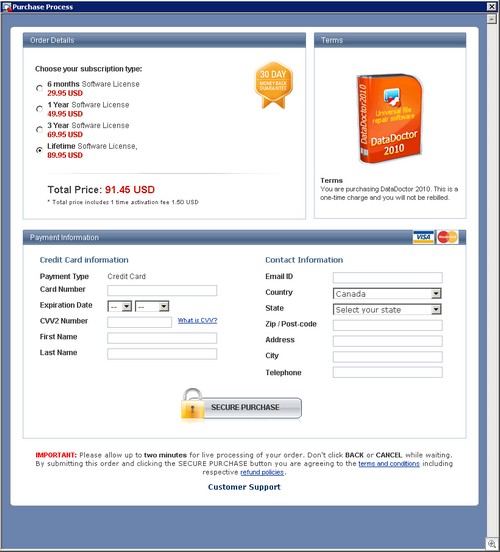
Rogue security software
— Rogue security software vendors will expand their distributions. [Symantec]
— There will be a decrease in the number of rogue security product schemes. [Kaspersky]
Social engineering
— Social engineering will become the primary attack vector. [Symantec]
— There will be an increase in the level of security consciousness among consumers. [Cooper/Verizon]
Social networking services
— Social networking third-party applications will be targets for fraud. [Symantec]
— Social networking sites will face more sophisticated threats as user bases grow. [McAfee]
— An increased number of applications on social networking services will be exploited because of the level of trust between friends. [McAfee]
— Facebook, Google, Twitter, TinyURL and other services will gain more control over criminal content. [Cooper/Verizon]
Spam
— More organizations will begin selling unauthorized email address lists to spammers. [Symantec]
— Spam volume will fluctuate. [Symantec]
— Instant messaging spam and attacks will increase. [Symantec]
Virtualized environments
— Virtualization will not be a target. [Cooper/Verizon]
Windows 7
— Windows 7 will be a major hacking target. [Symantec]
— Windows 7 (though not IE8) will be more robust than expected. [Cooper/Verizon]
— New vulnerabilities in Windows 7 as well as third-party software (i.e. Adobe and Apple) will be the main cause of exploitation. Although, if Win7 is secure, it will be a quiet year. [Kaspersky]
Kaspersky Lab 2010 cyber threat forecast
http://www.kaspersky.com/news?id=207575980
McAfee
http://mcafee.com/us/local_content/white_papers/7985rpt_labs_threat_predict_1209_v2.pdf
Symantec
http://www.symantec.com/connect/blogs/don-t-read-blog
Verizon business services (Russ Cooper, creator of NTBugtraq)
http://securityblog.verizonbusiness.com/2009/12/15/2010-security-predictions/#more-434
WebUser (UK):
http://www.webuser.co.uk/news/blog/cammjones/436323/what-will-the-web-bring-in-2010
Tom Kelchner