Hackers usually offer their services in the underground market, chatting in private forums, hidden behind various enigmatic aliases. However, a more enterprising bunch offers their services publicly, offering to hack into email accounts, Facebook, MySpace, ICQ or even Facebook’s popular Russian clone, Vkontakte.
However, you’d be an idiot if you actually used them. Doing business with black hats isn’t always the brightest thing to do — you might very well find yourself getting the bad end of the bargain.
Some recent research into one site dedicated to hacking Facebook revealed a number of dodgy sites all under the same IP (in the Cayman Islands, not surprisingly, and with a history). Let’s take a visual tour.
First, a more “general” site on hacking:
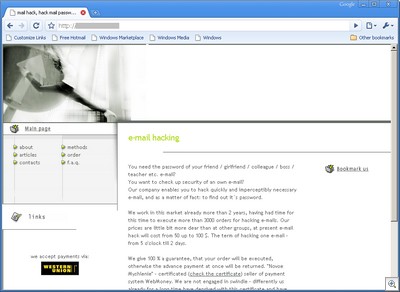
Or, hacking vkontakte:



(“vzlom” in Russian means “to break in” — of course, my Russian readers are sure to correct me.)
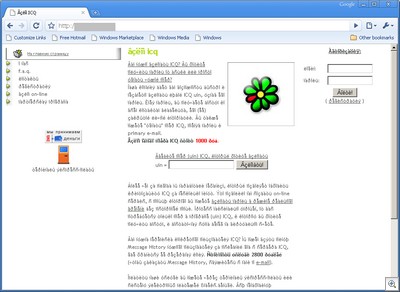
Or hacking ICQ:

MySpace:

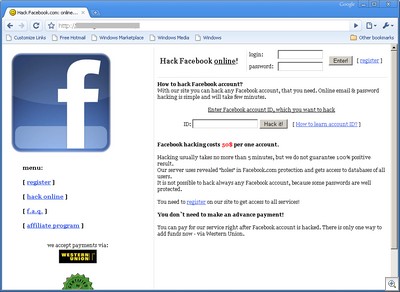
And, of course, Facebook:
But this IP has a number of other questionable domains, such as a site seen in the past delivering malware, and one which looks suspiciously like a phishing site. I can only speculate at this point on the other sites listed in the IP range (“escrow services”, etc.).
The whole dammed lot should be taken down.
Incidentally, if you use these services, please do the obvious and use complex passwords, changing them regularly.
Alex Eckelberry
(Hat tip to Patrick)


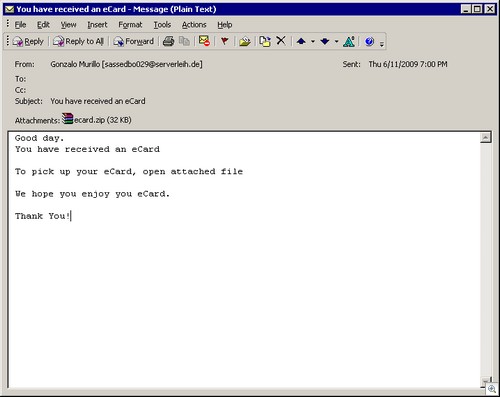
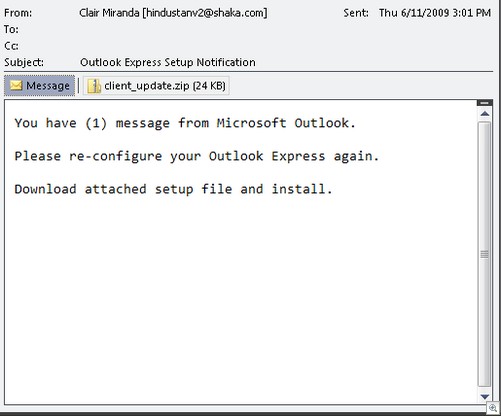
 FTC
FTC 
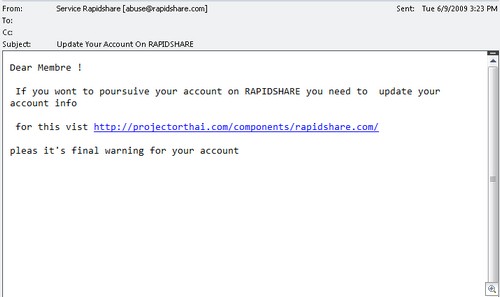

 The infected site, hxxp://an-inconvenient-truth.com, (DO NOT GO THERE!) has been registered since 2006, so, it’s probably a legitimate site that’s been taken over.
The infected site, hxxp://an-inconvenient-truth.com, (DO NOT GO THERE!) has been registered since 2006, so, it’s probably a legitimate site that’s been taken over.