Ah, Tumblr. It calls itself a microblogging site but it’s not exactly like Twitter, nor is it a Facebook or a YouTube. It does a little bit of all three, actually, and for many Tumblr is in a league of its own.
What makes this site so awesome is its Reblog feature, where it allows users to post content—from text, images, videos, links, and audio files—to their own Tumblr walls with the greatest of ease. Reblogged posts are displayed in a way that shows a link to the content source (if specified) and the name of the Tumblr account where the post was reblogged from. Clicking a post allows one to view the number of people who overtly liked the post and who reblogged it from whom.
Such quick and efficient sharing normally does not exceed two clicks on a mouse—a function already being implemented by both Twitter and Tumblr—it is fairly easy for anyone to cook up something phony and tell everyone all about it. And as we all know, phony posts can spread like wildfire. Fake viral posts can be popular on social networking sites, which don’t have an easy reblog functionality (see the Simon Ashton spam posts from 2009), making a service like Tumblr a prime target for scams and viral spam.
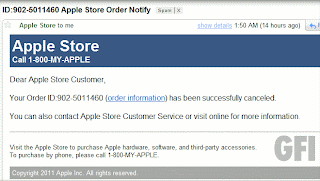
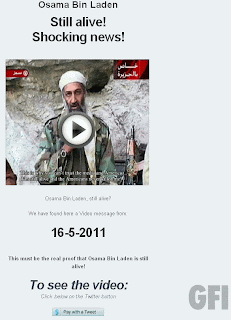
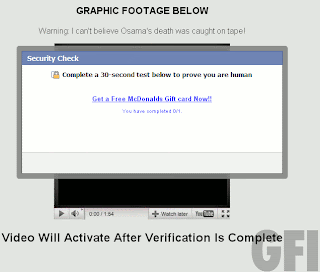
Case in point, we recently came across a Tumblr post claiming to have originated from the Tumblr staff’s own blog. The post said something like this:
Tumblr is testing for inactive blogs so the URLs can be deleted and reused by new members In order to not lose your blog, you must reblog this post so that your name will be on the safe list.
Thank you for your cooperation,
David Karp, CEO
Notice how many times this had interacted with in some way—137,848 notes (which includes both comments and reblogs)—and it is still very much being passed around as we speak. Many of the original posts have since been deleted, but it’s going to keep coming back to life for a while.
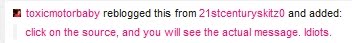
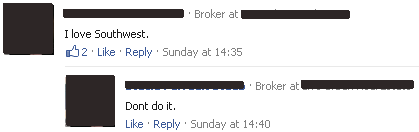
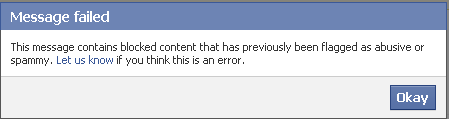
Thankfully, some users figured out this scam sooner, but those individuals were firmly in the minority. Even then, those users had to reblog the message so they could leave their “This is fake” comment—a Tumblr restriction, you usually have to reblog to leave a comment—which doesn’t exactly help matters:
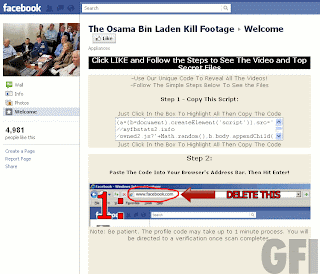
Clicking the source link found below the post actually leads to a short thank-you post for the community’s contribution to Tumblr’s own Japan relief efforts, not a “Dear John” note from David Karp himself. Just when you think you’re trying to be helpful, right? Well, it’s 100% fake.
Using Google to have an estimate of how many of these posts are currently floating around on Tumblr yields a number by the thousands still, which is sad indeed.
Click to Enlarge
Pro tip: Never panic over something you have not checked the validity of first. This, I think, has become an unspoken universal rule that applies to everything you see and read online, because it is foolish to do otherwise.
We urge you to be wary of such scams and always check the original source.
Jovi Umawing