The last few weeks, discussions have been bouncing around IRC in relation to a “guaranteed Twitter headshot”. While the downloads linked to were protected by a Sharecash gateway (think “useless survey”), it wasn’t too hard to find a version uploaded elsewhere. Depending on the mood of the individual controlling the infection file, you’ll either fall victim to a random annoyance or a few hours of face punching horror. Shall we take a look?
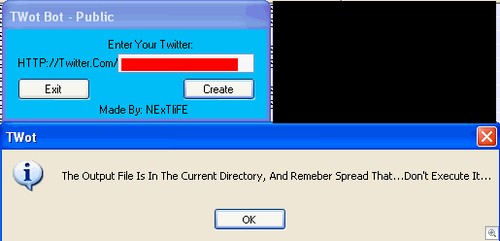
Presenting…the TWot Bot Builder.
As you can see, these days it’s all about the Twitter. “TWot Bot” consists of a very straightforward builder that lets you enter your Twitter name, then hit the Create button. You’ll end up with a file called “Server.exe”, which contains the Twitter username you entered into the builder.
The file is sent to the victim(s), and assuming they run the executable the attacker simply has to fire up their Twitter account and send some instructions to the compromised PC.
Server.exe accepts just two commands – “Shutdown” and “Destroy”.
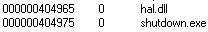
As you’ve probably guessed, Shutdown attempts to shutdown the PC. Destroy is rather nasty, attempting to delete the file hal.dll.
You don’t want to delete hal.dll.
If you don’t have a recovery CD, it could be a bit of a pain to get hold of your data and put it somewhere safe (you do have backups, right?)
Curiously, the infection file lists both your Twitter Username and one seemingly inactive Chinese account. While this account could theoretically take control of every infected machine, it is still sitting around doing nothing – not that I’m complaining!
Shall we take a look at detections? The infection file comes up as 5/42 on VirusTotal, which unfortunately is a bit on the low side. The Builder program shows as 1/42 (that would be us), so if you have someone playing around with it on your network it’ll be stomped into the ground. Keep your eyes peeled for Backdoor.Win32.Twotbot.A!
Christopher Boyd