SSA-Keylogger cleaner has been updated to reflect some new variants. Link here.
Alex Eckelberry
Update: Information on the types of systems infected here.
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
Update: I just spoke with Mike Wood, VP of Research at Lavasoft— this is not the same variant of the trojan as we found (they have also updated their database to the one we have been discussing). However, they have some really interesting data so we are hoping to collaborate.
Very interesting, a comfirmation (finally) of the kind of stuff we found. Lavasoft just posted a research note on a trojan and a server which look very similar to the one we found. Good stuff and well done to these guys. We’re pinging Lavasoft (currently closed as they are in Sweden) to find out more. Different variant or the same one? We should hopefully know more soon.
Alex Eckelberry
President
Update: Click here for more information on the types of systems infected.
Press release here.
Update: Most AV vendors have this thing now.
As we’ve written before, this keylogger was identified as a result of one of Sunbelt’s lead spyware researcher’s earlier discovery of a massive online identity theft ring in which thousands of unsuspecting computer users’ personal data had been compromised.
In a sense,
CounterSpy EnterPrise 1.5.x – 217
CounterSpy Consumer Beta 1.5.x – 217
Update: Fix and new data here. Also, to understand the types of systems infected (all of them were unpatched XP systems, click here).
Ok, we have the latest on this identity theft ring. And it’s pretty interesting.
Remember that all we found was the cache of data from the thieves — we didn’t have the actual keylogger that was responsible for it. We had a keylogger we had found that was similar and provided us some clues, but not this specific one that was reporting all this data back.
So we had to find the keylogger. That entailed trying to actually get a hold of a machine.
Last night, we finally got an infected machine and were able to figure out what’s going on.
Briefly:
– It’s footprint is extremely small — about 26k.
– It seems related to the CoolWebSearch gang, but that is still not certain.
– It is related to the Dumador/Nibu family of trojans. The keylogger executable is winldra.exe.
– It runs under Internet Explorer (IE), so for the average user, it will generally go undected if you’re using a software or hardware firewall. So much for my ranting about the need to run a software firewall.
– It turns off the Windows firewall.
– It steals data in the IE Protected Storage area.
– It steals data from the Windows clipboard
– As is normal with Dumador/Nibu variants, it steals logins and passwords from a number of programs: WebMoney, Far Manager and Total Commander; and modifies the host file to stop access to Trend Micro, Mcafee.com, Symantec.com, Etrust/Computer Associates, AVP, Kaspersky, F-secure, etc.
Since one thing it does is steal the IE Protected Storage Area, you can protect this data by turning off all the AutoComplete stuff in IE.
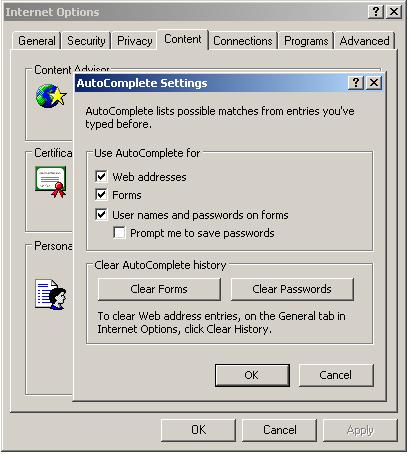
So far as we know, this keylogger is not detected by a number of the major AV companies. We are coming out with a fix in the next several hours which will be available a) to customers running CounterSpy (or the free trial) and b) through a free application we will make available.
Of course, we will be sharing data on this keylogger with AV vendors and antispyware companies, so definitions should start to propagate out from a number of other sources as well.
I will keep this blog updated as we get more data.
Alex
Update: See latest blog entries to get the latest info on this little bugger.
I’ve got some people asking me what to do to verify that they don’t have this keylogger.
The FBI is acting very aggressively on the matter, which then puts us in the odd position of needing to remain quiet about the details. This is a different type of trojan than others, because of the fact that researchers were able to see the data coming in.
So get a software firewall in place that has outbound protection. Try Sygate’s free one. Most antispyware or antivirus programs will not likely have caught this thing (as of 8/10, Symantec, McAfee and Panda don’t detect it, but there are a number of others that do, like Kaspersky and BitDefender. Lavasoft may have a fix as well, and we have shared the data with WebRoot and other security companies).
Then, update to the latest patches in WindowsUpdate. We’ve found that your chances of getting infected go up dramatically if you’re not patched.
Note that a software firewall is not a guarantee, due to the way this thing operates.
This keylogger is not CoolWebSearch. It was discovered during a CoolWebSearch (CWS) infestation, but it actually is its own sophisticated criminal little trojan that’s independent of CWS.
An antispyware or antivirus program will likely not catch it—and to our knowledge, there are none out there that can detect this thing through a scan of the system. So if you think I’m trying to sell CounterSpy through this news, find another conspiracy story to go after. We had one infected user we found who was quite sophisticated and ran all kinds of scans with various products, to no avail.
Anyway, we’re working on a free fix to get out to people which will be ready in the next 24 hours. But really, for the time being, just get a software firewall in place. It really will help block this thing from being able to do anything (with the caveat noted above).
If you find you’re infected, turn off the computer and start calling your banks, paypal, eBay, credit card companies, whatever.
Oh, and for AV? If you’re on a budget, just use Grisoft’s free one.
Alex Eckelberry
The new AIM beta shows BIG ADS!

Ah well.
Alex Eckelberry
This article in CNET discusses ways that Microsoft will be optimizing Vista to make computers run like new.
The big ideas? Background defragmentation and pre-loading commonly used components into memory.
Are you kidding?
I’ve spent years in the PC utilities space and from my experience: Defragmentation alone doesn’t do the trick and pre-fetching commonly used components won’t do the trick. Might help but it’s no magic bullet.
In my opinion, defragmentation is largely useless with the speed of today’s hard drives, unless maybe you have a he fragmentated system. To me, the problem has little to with hardware or caching. The problem has to do with all the junk that people install on their systems.
Users download smiley icons for their email or some adware program. Or, they install one of these antivirus suites (aka 10 pounds of crap in a five pound bag) and get an immediate performance hit.
A billion items in the tray icon are good indicators that the user is on a mission to slow their system down.
Of course, some bloat you just can’t control, like cookie or history bloat. That’s normal.
A re-architecting of Windows might help, but it’s way too late for that. I admit to being a little nostalgic for the old DOS days, but that’s wishful thinking.
The biggest barrier to Windows operating smoothly is software developers. I remember when coders would rejoice at saving a few k in memory in a program. Elegance was in the craftsmanship and artistry of programming (when I was Borland, Philippe Kahn used to refer to it as “software craftsmanship”). Now, with most of the big software companies outsourcing their stuff offshore with huge teams of programmers working in high level languages—or new programmers entering the workforce who have only really been exposed to VB or C#, you’re going to get bloat.
So there’s a tradeoff—speed of application development against elegance. Not all is bad, because fast hardware is so cheap.
We used to have a joke when I was working in performance utillities. Create a Windows speed booster with a simple mission: It would wipe the drive clean and reainstall Windows. Performance gains could be guaranteed.
Not a bad idea, after all.
Update: I got an email from a friendly fellow who said that I was unduly criticizing defragmentation — that he notices a slowdown in a week if he doesn’t defrag. He says I should say defragmentation is “relatively insignificant”
Hmm… I’m a wee skeptical, although I will agree that significantly fragmented systems should see some speed improvement with defragging. See this article from PC World a couple of years ago (“The PC World Test Center’s tests reveal that defraggers don’t actually improve performance. And Steve Gibson, president of PC consulting firm Gibson Research Corporation, confirmed our findings”).
What do you think? Post a comment.
Alex Eckelberry
Update: Information on the types of systems infected here. Information on the fix here.
Apologies that we couldn’t post more information — we simply ran out of time. This has been a pretty intense project and in the middle of it, I also had to go out of town. I am currently blogging from a remote location.
Computer World got the scoop on the story, and the author is largely correct. InformationWeek also got it.
We also shared this information with a very small number of trusted security experts, including Suzi Turner at Spywarewarrior. You can see her reaction here.
Here is a quick idea of what happened: Patrick Jordan, our most senior CoolWebSearch (CWS) expert, was doing research on a CWS exploit. During the course of infecting a machine, he discovered that a) the machine he was testing became a spam zombie and b) he noticed a call back to a remote server. He traced back the remote server and found an incredibly sophisticated criminal identity theft ring. (Jordon, previous to being employed by Sunbelt, was known to the security community as WebHelper)
Note that we are still trying to ascertain whether or not this is directly related to CWS.
The scale is unimaginable. There are thousands of machines pinging back daily. There is a keylogger file that grows and grows, and then is zipped off and then the cycle continues again (note that while thousands of machines are pinging back, the amount that are being logged into the keylogger file is less than that, but still significant). The server is in the US, but the domain is registered to an offshore entity.
It is very sophisticated, however, we aren’t sharing a lot of data for obvious reasons. We are in contact with the FBI.
The types of data in this file are pretty sickening to watch. You have search terms, social security numbers, credit cards, logins and passwords, etc.
In a number of cases, we were so disturbed by what we saw that we contacted individuals who were in direct jeopardy of losing a considerable amount of money. One particularly poignant moment was a family in Alabama whom I contacted personally last night and warned them of what was going on. This was a family where the father had just had open heart surgery, and they had very little money. Everything personal was recorded in the keylogger — social security numbers, their credit card, DOBs, login and password info for their bank and credit card companies, etc. We were able to warn them in time before they were seriously hurt.
But there is only so much we can do without bringing in extensive external resources. The scale of this thing is massive. As I’ve mentioned before, the keylog file itself grows and grows and then is removed, only to replaced by a new one. So we are taking down the files as rapidly as possible to save the information. Maybe some law enforcement group can use this information to warn people.
People who ask me what to do get a simple answer: Get a software firewall in fast. Just any decent free one will do the job.
I may be posting samples of the keylog files later but the effort is in the redaction…
Alex
An update on the massive identity theft ring we discovered earlier. The FBI has responded to us and they are working on the case. It looks like they were working on the case when after we sent originally sent the data in, but we didn’t get any response from them at the time indicating they had received our data.
I will be providing more later as well as some (redacted) samples of what the files look like.
This was discovered by Patrick Jordan, a senior staff researcher here. Patrick is a veteran of spyware, and even he admits to never having seen something like this before. It’s pretty staggering.
Alex Eckelberry
Update: Fix here. And information on the types of systems infected here.
In some recent research into a spyware exploit, our research team has discovered a massive identity theft ring.
We also found the keylogger transcript files that are being uploaded to the servers.
This is real spyware stuff — chat sessions, user names, passwords, bank information, etc. We have confirmed that this data is valid. Highly personal information, including even one fellow who has a penchant for pedophilia — all logged in detail and returned a webserver.
Note that there is a LOT of bank information in here, including one company bank account with over US$350,000 and another small company in California with over $11,000 readily accessible. This list goes on and on and on. Of course, there’s also eBay accounts and much more.
We have notified the FBI, but no response just yet. We have notified a few of the parties involved. (Update: It looks like they were working on the case when after we sent originally sent the data in, but we didn’t get any response from them at the time indicating they had received our data.)
If anyone has any other ideas, send ’em to us. Right now, we’re sitting upon literally thousands of pages of stolen identities that are being used right now.
Alex Eckelberry
Well, the user community seems to think so. By clicking on the results of our SunPoll, you can see that about 80% of the people who clicked on the survey felt that WeatherBug should be detected by antispyware programs. Note that this survey is totally unscientific.
(You can vote yourself by going to our front page and going to the SunPoll).

Blog Herald writes about spyware being hosted on Blogspot blogs (Blogspot is the public view of Google’s Blogger). Ben Edelman wrote about this months ago as well.
Yes, we’ve seen this as well. However, I want to make it clear that this does not mean Blogger hosts spyware or that having a blog will create spyware or any other such nonsense. Blogger just hosts a blog, and people can put all kinds of junk on it.
How can you get a spyware from a Blogger site? Just press NextBlog on the navigation bar on a Blogspot blog. NextBlog randomly goes to another blog, and if you’re lucky, you’ll hit one with a spyware payload! Couple of spyware sites we found are http://everiimoment(dot)blogspot(dot)com/ or http://3verlastin9lov3(dot)blogspot(dot)com/ (don’t go there unless you’re in a VMware session).
Note that a recent check of NextBlog (which is actually just a link to the URL www.blogger.com/redirect/next_blog.pyra?navbar=true) didn’t give us any spyware activity on a number of tests. We were seeing it last week but not this week. Go figure.
Here’s what these pages might look like:
However, a lot of what you see when you press Next Blog on Blogger is junk search engine sites, whose whole purpose is to create links that increase search engine results or to get people into a Blogger site and present Google adwords.
Like this:
My suggestion to the Blogger folks is to perhaps have a button on the Navbar panel which says “Report site”. This would be useful for reporting any type of naughty site.
Note that there’s spyware out there, but then there’s mental diarrhea like this site.
There’s no accounting for taste.
Anyway, just be aware and I would caution people from using the NextBlog button.
Update: The venerable Andrew Clover makes a very good point in the comments here.
Alex Eckelberry
This is great news. Spyblast was being marketed by Advertising.com with spyware built in! The FTC got a bit grumpy and now there is a settlement.
Check this out:
“The FTC complaint charged that Advertising.com, Inc., and its co-founder, John Ferber, distributed ads stating that because a consumer’s computer was broadcasting an Internet IP address, it was at risk from hackers. Consumers who clicked on one of the ads were shown an Active X “security warning” installation box, with a hyperlink describing SpyBlast as “Personal Computer Security and Protection Software from unauthorized users” and telling them, “once you agree to the License Terms and Privacy policy – click YES to continue.” The hyperlink did not indicate the nature and significance of the terms of the licensing agreement – namely that adware would be installed on their computers. Consumers were not required to read the agreement before installing the software. If consumers had read the agreement, they might have seen a statement saying that by accepting the software, they agreed to receive marketing messages, including pop-up ads, based on their Internet browsing habits.
…the SpyBlast software was bundled with a software program that collected information about consumers, including the URLs of pages they visited, that was used to send them advertisements.”
The consent order is here.
Alex Eckelberry
(Thanks Eric)
Web marketing folks are worried about the state of cookies — because antispyware programs are whacking them.
WebAnalytics makes the point that 3rd party cookies are dying, but the sky is not falling. It’s an outstanding article and well worth reading.
To wit: “The people who are most badly affected by monthly cookie cutting are the ad-delivery networks. These are the companies placing ads in many sites, and tracking exposure to the same users across all these sites. Third-party cookies are the life-blood of these agencies, and it seems 40 percent of the internet population doesn’t like them.”
Cookies are actually valuable on a first-party basis — meaning when they are only used for you and the website you’re visiting, without consideration to other sites.
The internet is inherently “stateless”. A website simply doesn’t remember or know who you are, and the minute you refresh a page, it thinks you’re a brand new visitor. That’s why cookies were invented years ago by Netscape and are so useful. You login to a site and it will remember who you are from that point on—and the site owner knows it’s you and not a new visitor. It creates a sort of persistent web experience.
Marketing people like Doubleclick soon realized that you could use cookies to track online habits of users and then serve specifically tailored ads. That’s a third-party cookie.
So you can go radical and proclaim “The internet should be stateless! All cookies should be banned”. Or you can look at real issue that people have, which is these third party cookies.
Alex Eckelberry
(Thanks Eric)
As I’ve blogged earlier, the Ignore option in our database is a way to deal with programs that people may actually want.
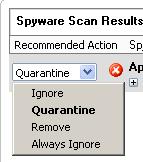
I’ll give you an example: Kazaa is a program that people usually care to keep (along with all of their MP3 files in the Kazaa directory).
What people don’t usually care for is the adware that comes with it. So we might put Kazaa as “Ignore” and the adware applications bundled with it as “Quarantine”.
We also use Ignore with programs like WeatherBug, which are programs that people may want to keep on their system.
It doesn’t mean we won’t remove Kazaa or WeatherBug. It means that we present “Ignore” as an option, giving people the choice to remove or not remove the program.
Unfortunately, it’s a highly misunderstood wording. To some people, “Ignore” might translate into “this program is not being detected”, which is an understandable, but incorrect perception.
We have thought of a number of alternatives. They are:
1. Quarantine everything. Bad idea, since then you’re toasting programs like Kazaa and WeatherBug, which people may actually want.
2. Put only adware bundlers on the Ignore list. That still leaves you with the problem of what to do about programs like WeatherBug… but does it matter?
3. Give people the option to default everything to Quarantine or Remove. Well, we sort of have this already but it’s not a well understood feature.
4. Change Ignore to “Choose”. That way, a user is presented with the potentially offensive application, and clearly given the option to make a choice. Personally, my favorite. Example:
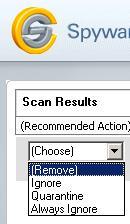
5. Change everything to Ignore and make people decide for each program. Eek, I don’t like that, people routinely like cleaning out cookies and it’s a hassle to click and choose each program or cookie to remove.
Please feel free to comment on this blog or send me an email directly. I’m curious to know your thoughts.
Alex Eckelberry
There’s been plenty of press over the last many months on some antispyware companies delisting or reducing the threat level of various adware programs.
So what is the state of detections? Who lists what, who doesn’t? Whom can you trust?
Sunbelt consultant and SpywareWarrior contributor Eric Howes has come up with the definitive test of the state of adware detections in the industry.
Six adware vendors were tested:
The tests were run against twelve antispyware apps:
Alex Eckelberry
(This subject was posted on separately in a different form earlier. My apologies for any confusions.)
If you didn’t catch the Slashdot post last night on this, here is the ZDNet Australia article on eBay’s security.
The /. post is here.
Alex Eckelberry
New York Times article on Mark Seiden, hacker for hire.
“Tell me the things you most want to keep secret,” Mr. Seiden challenged a top executive at the bank a few years back. The executive listed two. One involved the true identities of clients negotiating deals so hush-hush that even people inside the bank referred to them by using a code name. The other was the financial details of those mergers and acquisitions.
A week later, Mr. Seiden again sat in this man’s office in Manhattan, in possession of both supposedly guarded secrets. As a bonus, he also had in hand a pilfered batch of keys that would give him entry into this company’s offices scattered around the globe, photocopies of the floor plans for each office and a suitcase stuffed with backup tapes that would have allowed him to replicate all the files on the bank’s computer system.
MP3 interview also available, here. Thanks to beSpacific.
Alex Eckelberry
Big article by Mitch in InformationWeek. Read the article Claria Software Seeks Legitimacy, and the sidebar “Claria—Unsafe at any speed”.
Highlights:
-Claria is trying to shed its image as a spyware company.
-They disagree with assertions that their software is spyware. According to Claria marketing honcho Scott Eagle, “Users know they have our software. They use it hundreds of millions of times. We expose our terms of service; all roads lead to full exposure. They know we have pop-up ads.”
-Their new behavior analysis technology is touted as the future of advertising on the internet (Claria: “In five to ten years, all marketing will be behavior marketing,”)
-They are launching a new downloadable program, called PersonalWeb, which will generate a personalized home page based on the user’s behavior (why would anyone want this?).
-InformationWeek tests two Claria applications to see if they are, in fact, legit. The results? Insufficient disclosures on the types of data collected and confusing EULAs. Read the analysis here.
Lots more in the two articles.
Alex
Interesting perspective by Eric Goldman on New York Attorney General Elliott Spitzer’s recent enforcement action against adware vendor Intermix Media and how it has opened up a new front in the battle against this type of software.