From Deb Shinder:
It’s not just that the amount of spam is increasing lately (over the last few weeks, I’ve gone from getting 5-10 spam messages in my Inbox each morning to 20-40). Thank goodness for iHateSpam (on a recent typical Monday, over 3000 spams were caught by our server-level filters, addressed to either my husband or me, or to nonexistent addresses in our domain, before they ever reached our mailboxes). The really bad part is that the “quality” of the spam that gets through is deteriorating.
Now maybe “quality” is a contradiction in terms when you’re talking about spam, but here’s the point: in the past, the majority of spam messages that got through my filters were attempts to sell something, similar to the junk mail that we get in our physical mailboxes. Annoying, but not infuriating. My mail filters caught the blatant porn spam and other offensive messages.
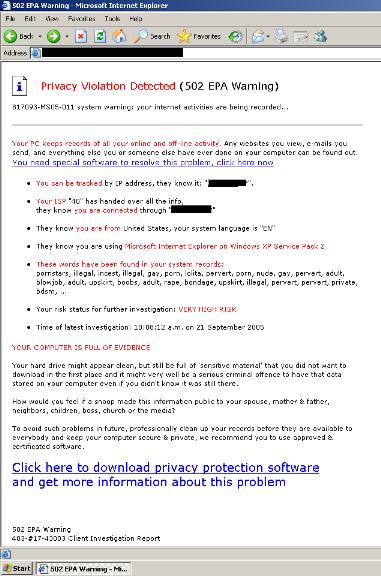
The past month has seen a big increase in spam scams of all kinds. Part of this is undoubtedly the natural tendency of con men rushing in where angels fear to tread after a natural disaster like Hurricane Katrina – I’ve seen a few of the fake charity solicitation spam with links that most likely lead to phishing Web sites. These sites are dangerous. It would be bad enough if the only problem were that the unsuspectingly person who enters credit card information to supposedly donate to the charity has those funds diverted to the scammer’s use, but it gets worse. The credit card info itself is often used to steal the person’s identity and make other, unauthorized charges. This is, in my opinion, the lowest of the low. Federal and state governments are cracking down on these scammers. Read more here.
Another spam scam I’ve been seeing regularly is from an organization that calls itself SPAMIS, which is supposed to stand for “Strategic Partnership Against Microsoft Illegal Spam.” I started getting these months ago, and found it pretty ironic that these claims that Microsoft sends unsolicited and unwanted e-mail were being sent as … unsolicited and unwanted e-mail.
The more recent messages from SPAMIS have gone far afield of the “spam” claims against Microsoft, and started making other accusations. The latest one, which I got last Thursday, is titled “Microsoft plans to stop supporting the American economy by outsourcing more than 10,000 jobs over 10 years to China.” When you dig deeper into this story, you find that the source of those numbers appears to be Kai-Fu Lee, the Microsoft executive who left to work for Google and is being sued by Microsoft for breaching the non-compete agreement that he had signed. Not exactly an unbiased source.
But whether or not the outsourcing numbers are true, it’s highly unlikely that the company has any plans to “stop supporting the American economy.” And if they did, what does that have to do with spam (which is supposedly SPAMIS’s purpose for existing)? It has become very clear, if it wasn’t already, that SPAMIS is not an anti-spam organization like CAUCE (the Coalition Against Unsolicited Commercial Email), but is in fact an anti-Microsoft organization that uses spam to further its campaign against the company.
To confirm even further that SPAMIS is a spammer, their most recent messages – like so many other spam messages – disguise who the message is from by placing the recipient’s own e-mail address in the “from” field. Thus, when their messages show up in my mailbox, it looks as if they came from me. Gosh, why would a legitimate organization do that? Obviously lots of other folks are onto their scam and blocking mail from their own domain.
According to several sources on the Web, the driving force behind SPAMIS is none other than Robert Soloway, who is a well-known spammer and seller of mailing list addresses. According to Spamhaus, a popular register of known spam operations, rumor has it that Soloway has hired virus writers to create spam zombies. You can read more about Soloway here.
It comes as no surprise that Soloway was one of the spammers Microsoft sued for illegal spamming. He has recently mounted a campaign against Microsoft’s Sender ID framework, a technology that’s designed to stop spam by verifying the IP addresses of email senders and comparing them to the registered addresses for the purported sending domain to authenticate senders’ identities – you can read more about Sender ID here.
I’m also getting lots of spam these days in other languages, including those in Cyrillic and Asian alphabets. Don’t know what they’re trying to sell me, but at least those are easy to tag as spam.
What about you? Have you noticed any new patterns in the spam you’re receiving lately? Are any of the new spam messages particularly annoying to you? Are you seeing more scam spams than usual? Are your filters having a hard time keeping up as the spammers change their domains and methods? Feel free to comment.
Deb Shinder