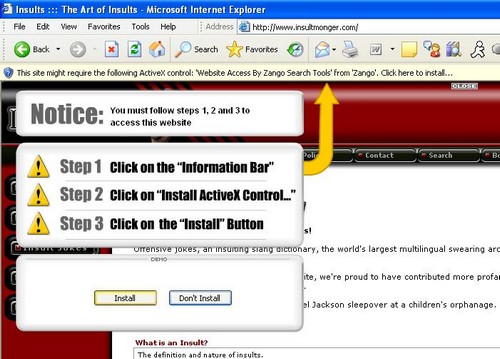
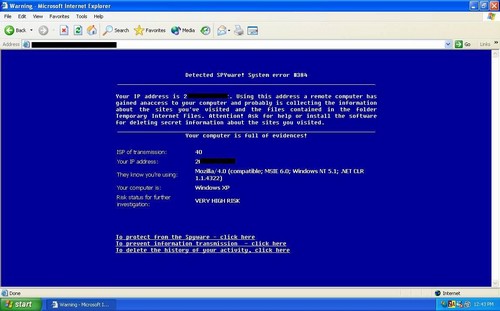
As I’ve written earlier, I often joke that some of these Internet security suites are worse than spyware. A nasty spyware application does a number of notable things: It pummels you with popups and slows your system down. Internet security suites pummel you with popups (aka security warnings) and slow your system down. But worse, they have the audacity of charging you an arm and a leg. See Security on the Cheap for my thoughts on the whole matter.
Rob Pegoraro’s latest article in the WashingtonPost proves the point:
…the complexity of the Symantec and McAfee suites seems to cause them to fail in ugly and destructive ways, according to readers who have written in to complain about these problems week after month after year…Most important, the latest McAfee and Symantec suites just don’t work all that well.”
(By the way, I disagree with Rob’s positive assessment of the Windows firewall in his article, but that’s a different issue.)
When Microsoft announced that they would be getting into the antivirus client-side business earlier this year, one major security company CEO was quoted as saying “we’re going to give Microsoft a whoopin!”. My first thought was “wow, that is going to be one large can of whoopass—I mean literally”. Some of these suites are just appalling in their size and bloat.
Microsoft getting into security software is really not cool. They are hurting their developer ecosystem, and I am tired of Microsoft constantly pushing its way into the space of its developers on one hand while gland-handing on the other (see this video for what I mean).
Now, Stu Sjouwerman has this to say in our enterprise-focused newsletter W2knews, commenting on the business market for antivirus:
“So Redmond is going head-to-head with the AV community at last. Well, they are going to have a tough time. Basically everyone is already AV-equipped so this is a replacement market. They will have to be a LOT better than existing AV players, and that is going to be hard. And they cannot drop their prices too much, as that will cause the antimonopoly lawsuits to come out of the closet. Good luck Redmond. You are going to need it. More about Ballmer’s announcement at MS PressPass.”
Microsoft may have a tough time of it on the business side, but on the consumer side, some of the companies making security suites are just giving Microsoft a helping hand. Security companies, mine included — rally, circle the wagons, hide the children, get out the big guns and write the best damned code that you can.
Alex Eckelberry