New fake codec site as of 9/12/2006:
Whois Data:
85.255.118.194
strcodec.com
Marinkovic Petronije
wm @ strcodec.com
Stepojevac CS
Partick Jordan
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
The bureaucratic monolith of the Department of Homeland Security (this is an organization larger than even a superstar manager like Jack Welch could manage), put on training exercise back in February, dubbed Cyber Storm:
The results? The AP says an internal agency document shows the simulated attacks bombed or otherwise infiltrated computer servers, crashing the Federal Aviation Administration’s control system, defacing newspaper Web sites and threatening power outages. Apparently the defenders had trouble recognizing coordinated assaults and even more trouble coordinating their responses among dozens of agencies and entities who had yet to be formally introduced.
Link here.
No wonder this agency hasn’t been able to keep a cyber security czar around.
(To be fair, this is the kind of stuff you find when you do such exercises. My beef is with the idiocy of joining together a vast army of different agencies under one wing — and then expect it all to work right, whether in a hurricane or a cyber attack).
Alex Eckelberry
We love what Zango does for the MySpace community. Security researcher Brian Porter ran across this one recently. You just hit the page http://www.myspace(dot)com/82959792 and immediately get hit with a Zango installer to watch a movie.
What you get for all this is a 30 second idiotic “commercial” of a man rolling his eyes:
Nothing new, PaperGhost over at Vitalsecurity.org has been on this for some time. Just more background noise from “a small group of fixated critics”.
Alex Eckelberry

From PIRT:
1. PayPal
2. eBay
3. Bank of America
4. Fifth Third Bank
5. Wachovia
6. Nationwide
7. Bank of Scotland (Halifax)
8. Volksbank
9. e-gold
10. Barclays
11. Halifax
12. Wells Fargo
13. CitiBank
14. National Credit Union Administration
15. NAFCU
16. Commonwealth – NetBank
17. Michigan Schools and Government Credit Union
18. Chase
19. Texas Dow Employees Credit Union
20. National Australia Bank
21. Lloyds TSB
22. Bank of Scotland
23. Banesto
24. Flagstar Bank
25. IRS
26. Key Bank
27. St. George Bank
28. Banca Fideuram
29. EGG
30. Desjardins
Link here.
Remember, we always need more volunteers for phishing takedown… feel free to volunteer here.
Alex Eckelberry
Lance James is a good friend of ours and an epic guru on phishing (heck, he’s even got a book about it). He’s doing a webcast on phishing, sponsored by us.
Here’s a brief description:
WEBCAST: Phishing exposed
WHEN: Premieres September 19, 2006 – available on demand
SPEAKER: Lance James, Author, “Phishing Exposed”Information security and phishing expert Lance James exposes the world of undercover phishing operations. He reveals the sophisticated techniques used by phishers and explains how to protect your data from phishing attacks. Register for this webcast here.
Feel free to join us for this seminar!
Alex Eckelberry
Vitalsecurity follows-up on our post yesterday with more:
Well, sadly the guy who owns that site also happens to own the Paris Hilton site covered here by Sunbelt. They get you to download completely fake “videos” that actually install lots of Dollar Revenue Adware (and some other stuff, too). It’s a big, fat, fake scam and it stinks. Now that we’ve established this guy pushes Zango videos from the car-chick site, do you think I’m about to directly tie Zango in with the wonderfully deceptive Paris Hilton site? Well, take a wild guess.
Link here.
Alex Eckelberry
How to change taskbar grouping behavior
You can configure the taskbar Properties in XP to group similar items together (for instance, all open Word documents) when the buttons start to get too small. By default, the items are group in the order they were opened (the one opened first is first in the group, etc.). You can change the grouping behavior by editing the registry. Here’s how:
You have to log off and log back on before the change takes effect, and it only applies to the user account logged on when the change is made.
How to Tweak the XP Recovery Console
Here’s a very useful article that shows you how to remove the built-in restrictions on XP’s Recovery Console so you can use it to work anywhere on the hard drive, use removable media, and more, here.
This month’s Patch Tuesday looks like a light one
Patch Tuesday is today, but it appears there will only be three security updates released this month, with one of these (for Office) listed as critical. Read more here.
Running a web site on XP.
If you want want to run your own web site and host it on your XP system, you need web server software. If you’re running Windows XP Pro, you can install Internet Information Service (IIS) 5.1 through the Control Panel | Add/Remove Programs | Windows Components. IIS 5.1 has some limitations: you can only create one site, and only ten people can connect to it simultaneously. That may be sufficient for a family site. If you need a more robust site or multiple sites, you can get Windows Server 2003 Web Edition, which costs much less than the other editions of Server 2003 ($399, as opposed to $999 for standard edition) and includes IIS 6.0.
Another option is to run the open source Apache web server on XP. For more info, click here.
Finally, consider your Internet connection bandwidth and terms of service. You need a decent upstream speed (preferably at least 384Kbps) for those who visit your site to have a pleasant experience. Many ISPs throttle upstream bandwidth. Some also prohibit running servers in their TOS, so check your contract. You also need a static IP address, or you’ll need to use a service such as TZO’s dynamic DNS to map your domain name to a dynamic IP address.
But remember: When you set up your own website, you are responsible for the security of that site. All too many times, we see websites hacked to run phishing operations and malware, simply because the administrator of that website didn’t keep the web server software updated to the latest version, or didn’t put in basic security.
Error 633 when starting broadband connection
If you try to connect to your broadband service and get an error message that says “the modem (or other connecting device) is already in use or is not configured properly,” it usually means you already have an active connection. The solution is to disconnect the existing connection before trying to establish the new connection. See KB article 279658.
Taskbar appears on the wrong monitor
If you’re using multiple monitors in XP and you change the monitor you want to be primary monitor and then log off, you may find when you log back on that the taskbar appears on the secondary monitor, even though your icons are on the primary monitor. This can happen when you use a video adapter. Luckily, there’s a simple procedure for fixing the problem. Just follow the steps in KB article 905776.
Desktop icons randomly change
A common problem we hear about is when some of the icons on the XP desktop and/or on the Quick Launch bar randomly change to a different icon. This happens when the icon cache isn’t properly updated. There’s a registry edit that can fix it, but be sure to backup the registry and use caution when making changes. You can find step by step instructions in KB article 132668.
New Vista Networking Features
Microsoft completely rewrote the TCP/IP stack in Vista, making a number of improvements. Some of these, such as native support for IPv6, won’t mean much to the average home or office user. Others, like the new algorithms that should result in a considerable improvement in network speed/improvement for those with fast broadband connections, will be welcome by all.
The new Network Center, which replaces My Network Places, may take a little getting used to. I like the graphical map of the network, and it’s nice that you can use the Personalize feature to change the name and icon of a network connection. This is especially useful when connecting to wireless networks that were previously identified by their SSIDs (which was often something generic like Linksys3345).
You can read more about Vista’s new networking features here.
Deb Shinder, MVP
From getting married to running for office, it seems you can do just about everything online these days. Childbirth, memorial services and almost everything in between – they’re all turning up on the web. We’ve talked before about how important the Internet has become in doing everyday tasks like paying our bills and keeping in touch with our friends and families. Now we’re also marking many of the big milestones of our lives on the ‘Net, too.
Last weekend, our local paper did a feature on the phenomenon of online weddings (link).
It seems that for a price (ranging from a few hundred to a couple thousand dollars) you can broadcast a live feed of your wedding ceremony over the Internet, so that those who aren’t able to make it in person can be there not just in spirit, but in virtual reality, too. The video can also be saved and posted for a period of time following the wedding, so that your guests not only don’t have to travel, they don’t even have to be free at the time of the wedding.
I can see how this is useful when you have elderly relatives who aren’t able to physically get to your wedding location, and it could certainly save folks a lot of money (virtual guests don’t even need to worry about getting dressed up to attend), but I don’t know – to me, it’s just not the same as being there. I hope it remains a supplement to, and not a replacement for, the “real thing.”
If saying your vows in front of a virtual audience “out there” somewhere isn’t exhibitionist enough for you, we’ve also heard of a few mothers “going live” with the video of their babies’ births. I guess this is the natural extension of recording the birth (something I did with my own homebirth); I just hope these folks are putting password protection on those web files. I’d hate to know that just any stranger could stumble across such video.
Politicians are using the Internet to their advantage more and more, finding it a relatively cheap and effective way to reach voters. Back in the 80s when I ran for city council, I had to rely on ads in the local newspaper, yard signs, flyers and good old-fashioned door-to-door handshaking. Today you could theoretically get elected to public office without ever leaving the comfort of your home.
Even at the end of life, the ‘Net is still there. Memorial web sites are becoming a popular service for funeral homes. For example, Lifestorynet (www.lifestorynet.com) is a site on which funeral homes post a biographical web presentation with photos and text of the deceased. Online-Funeral (www.online- funeral.com) provides “live” coverage of the visitation room at the funeral home and saved video footage of the funeral service, as well as a family website where you can send messages to the family, and sells CDs of the funeral. Many major newspapers now include online guest books in their obituaries section where friends and families can share memories and express condolences. An example is here.
What do you think about this “cradle to grave” Internet archiving of our lives? Is it a great new way to share important life events with more people and extend our families, or does it constitute an invasion of the little privacy that we have left? Would you want your wedding, birth of your baby, or funeral services to be available online?
Deb Shinder, MVP
Adam Thomas in our spyware research team caught two more security scam codec sites right after I posted my blog.
icodecpack(dot)com
85.255.118.13
Nikita Englund Freecodecs ltd
nik @ freeecodecs.net
Albany NY US
playercodec(dot)net
216.255.176.178
Hilary Reed
webmaster @ playercodec.net
Bastad SE
Alex Eckelberry
DollarRevenue, a fruitful source of malware, just keeps having fun with users.
First, we search for “sexy paris hilton” in Google, and get a hit — the first one.
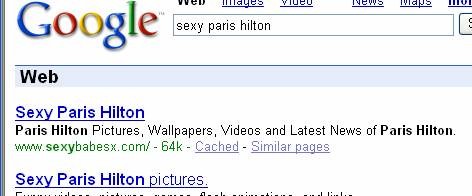
Then we click on the video picture to view it.
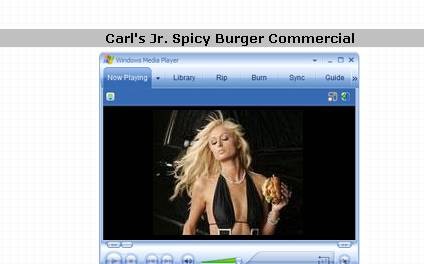
We get an install box. No EULA appears and to the casual surfer, it just seems like you’re installing the video.
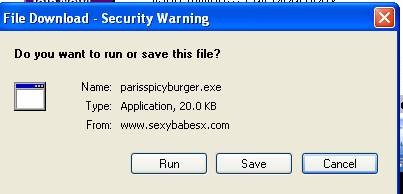
The installer, sexybabesx(dot)com/parisspicyburger.exe (Virustotal) actually calls the loader file from promo.dollarrevenue(dot)com/bundle/loader.exe. And your life, at that point, is no fun at all.
You can see a movie, here.
Alex Eckelberry
(With copious acknowledgement to Patrick Jordan in our spyware research team)
A new fake code site, movscodec(dot)com, hosted (not surprisingly) by the infamous Intercage/Atrivo.
These fake codecs are bad news and this one is no better. A user recently told us:
“This disgusting program installed itself when I was told I needed to install a codec to view a movie about my stocks. I was prompted to buy tons of programs and my computer hasn’t been successfully cleaned since.”
Movscodec is even blatant about what they do in their EULA:
SOFTWARE INSTALLATION: Components bundled with our software may report to Licensor and/or its affiliates the installation status of certain marketing offers, such as toolbars, and also generalized installation information, such as language preference and operating system version, to assist Licensor in its product development. No personal information will be communicated to MEDIA-CODEC or its affiliates during this process. Licensor may offer additional components through our version checking/update system. These components include:
(a) “Internet Explorer Security Plugin 2006”: Internet Explorer toolbar that protects your computer while you browse by setting high level of security for suspicious hosts.
(b) “Public Messenger ver 2.03”: Popup advertising module that opens Internet Explorer ad windows when you are connected to internet.
(c) “Internet Security Add-On”: your Internet Explorer homepage will be changed.
(d) Security software: antivirus/antispyware application.
Other similar sites include:
dvdcodec(dot)net
emcodec(dot)com
emediacodec(dot)com
emediacodec(dot)com
imediacodec(dot)com
Intcodec(dot)com
media-codec(dot)com
mediacodec(dot)net
media-codec(dot)net
movscodec(dot)com
mpgcodec(dot)com
nvidcodec(dot)com
nvidcodec(dot)com
pcodec(dot)com
svideocodec(dot)com
vcodec(dot)com
V-codec(dot)com
vcodecdownload(dot)com
vcodec-download(dot)com
vcodecget(dot)com
vcodec-get(dot)com
vcodecpull(dot)com
Vicodec(dot)com
Vidcodec(dot)com
vidscodec(dot)com
zcodec(dot)com
Alex Eckelberry
(Thanks to Sunbelt researchers Patrick Jordan and Adam Thomas)
Free AD browser
Nice Windows freeware AD browsing with self-service and optional chat. Easy to deploy via GP Software Installation and ADM template. Link here.
Process killer
This little tool shows you which process locks a file and allows you to kill that process. Quite useful! Appropriately named “Who Lock Me”. Link here.
Expert Q&A: Virtualization.info Founder Shares Thoughts
In this expert interview, read the thoughts of Alessandro Perilli, the Internet’s most well-known virtualization advocate and author of the popular virtualization.info blog. Learn what he had to say about the next big technology shifts in the virtualization arena, what Xen has to do to compete with VMware and ways to learn more about virtualization. At SearchServerVirtualization.com.
Top 10 SQL Server Security Tips
Password cracking and SQL Server hacking tips topped the list of favorites on SearchSQLServer.com during the first half of 2006. View all of the top 10 tips that piqued reader’s SQL Server security interests. Some of the tips you will find include: ten hacker tricks to exploit SQL Server systems, discover and lock down vulnerable SQL Server services, and password cracking tools for SQL Server. At SearchSQLServer.com (free registration required).
Add Gigabytes By Reducing Disk Space For XP’s System Restore
Perhaps the fastest way to a few gigabytes more on a disk is to reduce the amount of disk space devoted to XP’s System Restore feature. Learn more in this tip.
VMware On Mac Will Do Little To Ease Desktop Management Pain
VMware Mac product will not impact desktop management or help standardize platforms in heterogeneous shops. Read more in this article.
When ActiveSync Won’t Download Mailbox Items To Mobile Devices
One of the toughest problems to troubleshoot is when Exchange ActiveSync won’t download mailbox items to a portable device. In this tip, contributor Serdar Yegulalp outlines the potential causes. At the SearchExchange site.
New: Draft Guidelines on Electronic Mail Security
The Computer Security Division of the National Institute of Standards and Technology has come out with a number of draft publications. One of these, SP 800-45A, “Guidelines on Electronic Mail Security,” is intended to aid organizations in the installation, configuration, and maintenance of secure mail servers and mail clients.” It’s a 143-page document with an awesome amount of really useful information. Link here.
Microsoft, Cisco Release NAP/NAC Roadmap
Microsoft and Cisco released plans on just how they would make their competing security architectures interoperable. At the Security Standard conference in Boston this week, they demonstrated an architecture that will enable interoperability between Cisco’s Network Admission Control and Microsoft’s Network Access Protection technology. The two had promised interoperability between their network access security offerings two years ago. They plan beta testing of the architecture by the end of the year. General availability is expected in the second half of 2007, following the launch of Microsoft’s “Longhorn” Server. More at SearchWinIT.com.
Stu
Earlier we showed Microsoft’s security solutions being pushed in Vista. Now we see the same thing in Exchange 2007 (beta 2), right from the console, thanks to some pictures forwarded to me by a faithful blog reader.
In this first image, you can see a page in the console. Note the link that says “Secure your Exchange Servers from viruses, worms and other malware.”
The next picture shows the dialog you get when you click the link.
And then this picture shows the download site you’re taken to when clicking on the download link.
Combine this type of activity with ruthless price undercutting, and you just have to say: “where’s the love, people?”
Alex Eckelberry
A lawsuit against Zango was dismissed.
Zango crows:
“We are pleased, but frankly not too surprised, by the voluntary, with-prejudice dismissal of the lawsuit by the plaintiffs,” said Ken McGraw, Zango’s executive vice president, general counsel and chief compliance officer. “We have maintained from its inception that this case had no merit. The dismissal vindicates that position.”
Note that detractors from Zango’s model are a “small group of fixated critics”.
“Despite occasional distractions like this unfounded lawsuit and the background noise of a small group of fixated critics, I’m very proud of the fact that our desktop advertising business continues to grow and progress nicely…”
This was the lawsuit by the cool-handed, gun-slinging firm of Collins Law, which has been active in the space, having also sued companies such as Direct Revenue and eBates.
What’s the real story? The case was dismissed with prejudice because Collins Law asked that it be. There was no court decision, or impending decision, that played any role. The Judge did not order this dismissal. It was voluntary.
The case involved only three individuals as plaintiffs. It was not a class action lawsuit. This case has no impact on the ability of other people who want to bring a lawsuit against 180Solutions/Zango.
Collins asked to dismiss the case because they did not believe that this particular case stood a good chance of being approved by the court as a class action. The hope for a class action was why they brought the case in the first place.
Vitalsecurity weighs in, not charitably to Zango’s case.
What can I say? I’ve said my share already.
Alex Eckelberry
Doug Barney at Redmonmag preaches:
What should you do? Don’t blindly buy bigger and bigger Microsoft stacks. Just because it’s integrated doesn’t mean it’s best in the long run. Remember, the chief advantage of any monopoly is price control.
Support third parties. Don’t let Microsoft have it all, or you’ll have to live with it when they do.
(I’m so obviously biased I won’t even bother to add further commentary. )
Link here.
Alex Eckelberry

Text in a message is interpreted as a blank attachment by Outlook Express
When you use certain versions of Microsoft’s Outlook Express email client, you may find that some messages or newsgroup postings are incorrectly interpreted as blank attachments. This happens when the message body contains invalid attachment headers or footers. There’s a workaround to the problem, which you can find out about in KB article 898124.
How to Start and Run the XP Recovery Console
The Recovery Console is a tool built into Windows XP that will allow you to repair problems when your XP computer won’t start. Here’s how to start it:
You can use the Recovery Console commands to change file/folder attributes, run batch files, change the boot configuration, run chkdsk to repair disk problems, copy and delete files, disable and enable services, manage disk partitions, overwrite the boot sector, repair the Master Boot Record, format drives, and more. For a complete list of Recovery Console commands, click here.

Using the New and Improved Vista Search Feature
The new search functionality in Vista makes it far easier to find what you’re looking for, whether that’s a document, program, picture or song. For instance, if you don’t want to click through the Programs menu to find an application such as Corel PhotoPaint, just type “Corel” in the search box on the Start menu and you might see several lists: one labeled Programs with any Corel programs you have installed, one labeled Files showing any files that contain the word “Corel” and one labeled Favorites and History that list any URLs you’ve visited on the corel.com web site.
If you click Search on the Start menu and then click the Advanced Search button on the Search dialog box, you can set very specific search parameters, including the types of finds you want to search (email, documents, pictures, music, contacts, games, instant messages, and many, many more), the location(s) to search, file sizes, dates, authors, filenames, or tags. You can save your searches, too, to prevent having to conduct the same searches over again. For more info about Vista search, click here.
Uninstalling Vista from a dual-boot configuration.
Uninstalling Vista from a dual boot machine is relatively straightforward – most of the time. Nonetheless, we recommend that you back up everything before you start. Then follow these steps:
Vista RC1 is out
As you probably know, Vista build number 5600, Release Candidate 1, was posted on the Microsoft web site on September 1. This code is said to be pretty much what we’ll see in the final commercial release. We’ll be testing RC1 this week and reporting back to you on our experiences. Meanwhile, Amazon posted the availability dates of Vista and Office 2007 as January 30, 2007, although Microsoft has not confirmed those dates. You can read more here.
Deb Shinder, MVP
Last week I did a bit of traveling from Dallas to San Diego and back, and had two of the most pleasant flights I’ve had in years. There were no snakes in sight, but there were other reasons that flying was so much less of an ordeal than usual. It was due in equal parts to the piloting skills and/or good weather that resulted in zero turbulence, the less-than-crowded plane that allowed two of us to spread out across three seats, and all my nice little electronic toys that occupied my mind and made the time pass quickly.
I had, in my nifty vertical briefcase that’s so much easier to haul down narrow airplane aisles than a traditional horizontal one, my extremely lightweight and compact Sony TX series laptop and my Samsung i730 Pocket PC phone. My son, who was traveling with me, had his own laptop and a Creative Zen Vision M portable media player. Looking around the plane after we reached cruising altitude, I noticed that about half the passengers were plugged in to their MP3 players, portable DVD players or electronic games, or were working on their computers.
I had to wonder how much of the peace and quiet in the cabin could be attributed to all those electronic gadgets. If deprived of my tech toys, I’d probably just read a book, but lots of people these days aren’t readers, and would probably be talking, drinking, etc. if they weren’t involved in their music, movies or work.
On the flight out, across the aisle and one row up from us was a young mother with a small baby. Unlike on a recent flight to Las Vegas where a crying baby went on and on for almost two hours (eventually reducing the mom to tears, too), we never heard a peep out of this one. I overhead the mother showing her seat mate that she had an earbud up next to the baby’s ear, and she explained that she was playing soft classical music to the baby. It certainly seemed to be working.
I was disappointed to read a couple of weeks ago that Boeing is dropping the Connexion onboard wireless Internet service because most passengers found the $9.95 per hour charges ($26.95 for the entire flight) too expensive. I had hoped the service would spread to domestic airplanes and that the cost would come down. I’d love to be able to surf the Web and send and receive email while I’m in the air.
Even without the ‘Net, though, there’s plenty I can get done with my gadgets. Putting business before pleasure, first I fired up Word on the laptop and finished an article I was writing. While I worked, I was also listening to a talk radio show I’d recorded previously. I had about fifteen hours of radio on the SD card in my PPC phone, and I can listen to them on that device or by popping the card out and inserting it into the built-in SD card reader on the laptop. After finishing the article, I opened up Microsoft Streets and Trips and looked up the route from the car rental agency to my destination in San Diego. All that out of the way, I shut off the radio show and decided to watch a movie. Despite it’s tiny size (under 3 lbs. and under 1 inch thick), the Sony has a built in DVD drive.
Listening to music, radio shows or movies is a great experience with my Shure sound-isolating earphones. They’re a little pricier than other brands, but the sound is fantastic; it’s like being right there in the middle of the movie or sitting onstage with the band. If I’d had them on that flight to Las Vegas, the crying baby might not have been an issue.
On the flight back, I was in the mood to read a book. Thanks to my electronics, though, I didn’t have to lug a heavy hardback or even a paperback onto the plane. Instead, I brought twelve novels – all ebooks that fit on that same 2 GB SD card along with my music and talk programs, and plenty of free space to spare. It’s easy to read on the Pocket PC without even having to break out the laptop. My husband prefers audio books, and you can store plenty of them on an SD card, too. My son spent most of the flights watching past episodes of “House” on the Zen. If only we’d had that in-flight Internet service, I could have used Orb to connect back to my Media Center PC and watch all the programs it had recorded, or even live TV. Oh, well.
One thought struck me as I watched so many of those around me using their own electronics, though. Being the obsessive-compulsive type that I am, I’m always careful to put the phone on flight mode as soon as I board the plane, and the Sony has a convenient switch for turning wireless on and off without opening the lid. Of course, the flight attendants always include a warning to turn off your devices in their standard spiel. But I’ve always wondered how many people ignore or forget those instructions – and just how much of a hazard that really poses to the plane’s navigational systems.
There have been a number of documented cases where pilots got erroneous instrument readings that were tracked down to computers, cell phones and even hearing aids. That’s why FAA rules restrict the use of portable electronic devices during takeoff and approach/landing. Use of cell phones and wi-fi is prohibited at any time during flight by most airline policies. Link here.
Despite all this, there has been an effort by some passengers and members of the cell phone industry to get the rules relaxed banning cell phone calls during flight, in particular. We saw during the September 11 terrorist attacks that many of Flight 93’s victims used their cell phones to find out from people on the ground what was going on. On the other hand, cell phones and other portable electronics can easily be adapted to detonate explosives devices, too.
But the more insidious threat is perhaps the unintentional interference posed by signals emanated by our tech toys. David Watrous, president of the RTCA (Radio Technical Commission for Aeronautics), who testified in July 2004 before a U.S. House of Representatives subcommittee on aviation hearing about the use of cell phone on aircraft, said that all portable electronic devices have the potential to interfere with avionics (radio navigation signals), especially when the plane is close to the ground. You can read his testimony here.
There have also been some “air rage” incidents that occurred when passengers were told to turn off their electronics. It appears that some of those “electronics addicts” take their habits very seriously. There are probably many other passengers who think they’re complying when they aren’t. With some devices, it’s not at all clear when they’re completely off and when they’re just in standby mode.
And even if allowing cell phone calls during flight doesn’t pose a risk to our safety, it certainly carries a potential threat to our peace of mind. Do you really want to listen to your fellow travelers babbling endlessly to their friends while you try to work or sleep? We already have to put up with that in grocery stores and restaurants.
Hmmm … it’s beginning to look as if electronics on planes could be as scary as snakes. MSNBC is running a poll on which you’d rather see on your next flight: snakes or cell phones. So far, the snakes are way out ahead. You can cast your vote here.
What do you think about electronics on planes? The best thing to happen to flight since the Wright Brothers, or a menace that should be eradicated? What electronic devices do you use on the plane? Do you always remember to turn off your devices when you’re supposed to? Have you seen other passengers using their cell phones or other prohibited electronics in flight? Do you think it really poses a safety threat or are the experts just being overly cautious? Would you like to see the ban on cell phone calls during flight lifted?
Deb Shinder, MVP
Investigative complications because of ancient computer:
Maj. Gen. Gerhard Lang of the Federal Criminal Investigations Bureau said kidnapper Wolfgang Priklopil, who killed himself by jumping in front of a train within hours of Kampusch’s escape on Aug. 23, relied exclusively on a Commodore 64 computer — a model popular in the 1980s but now considered an antique.
Link here (with a hat tip to Ferg).
Alex Eckelberry
We’ve been holding seminars on spyware (our next seminar is in Pittsburgh). One blogger went to our event in Seattle and wrote a nice blog entry about it, complete with a picture!
The overall presentation of the seminar was great, and Eric shared his insights into the antispyware space and its challenges, and the attendees’ participation helped in raising valid points about the state of the industry. Though I will not probably have the chance to use the enterprise management tool that was mentioned and demo-ed in the presentation, the apparent ease of use and managability of such a tool did give me some points to ponder about future enhancements to the system I’m managing.
Link here.
Alex Eckelberry