|
Extending the desktop while playing video may cause problems
If you try to extend your desktop to a second monitor while Windows Media Player is playing a video on the primary monitor, you may have problems, including sound with no video, or the video stops and won’t start again. This has to do with the DirectDraw implementation in Windows XP. There are a couple of workarounds, although they’re somewhat along the lines of the old joke: “Doctor, it hurts when I do this.” “Then don’t do that.” See KB article 325771 for more info.
Troubleshooting keyboard problems
Most of the time we take it for granted, but when your keyboard stops working correctly (or at all), it’s awfully hard to get anything done on your computer. Keyboard problems can range from a total loss of functionality to more confusing happenings, such as the wrong characters appearing when you type. For help in solving your keyboard troubles, see KB article 258826.
Until next week,
Deb Shinder, MVP
Last week, for the first time, I cast my vote in a national election with no piece of paper to back up my selections. We’ve had electronic ballots for a while, but the ones I used in the past printed out a paper ballot that was then dropped into a locked box just like the old punch card or even older “X marks the spot” types were. This time, the only record of my vote was in some computer’s memory.
How did that make me feel? Well, I have to admit it made me just a little nervous. Not because I had any difficulty understanding the system or picking my candidates – just the opposite. The process was straightforward and fast, a simple touch screen interface with a big flashing red button that you push to finalize your vote. It’s hard to see how anything could be any easier than that.
But, as I discussed in my November 7 personal blog post, pushing that button felt vaguely like pulling the lever on a slot machine. I wasn’t at all sure what, if anything, would happen. Would it really be recorded properly? And if not, how would anyone ever know?
It seems I’m not the only one who sees a down side to purely electronic voting. I heard the same distrust expressed by many others – including those on the winning side. And something I found telling was that so many of those who are disturbed by the new systems are not Luddites who know nothing about computers – they’re people (like me) who are intimately acquainted with how computers work and making their livings working with them.
Of course, that may be part of the problem. Like the doctor who sees disease every day and thus never trusts an illness to be “just a cold,” or a cop who deals with criminals so regularly that he suspects everyone of having criminal intent, maybe I just see so many malfunctioning computers that my perception of their reliability is skewed toward the negative side. After all, very few clients call me out to see how smoothly their networks or running and very few newsletter readers write to tell me their software is doing everything exactly as it’s supposed to.
No, people come to me when Windows won’t boot or their Internet connection goes down or Excel isn’t calculating properly or a virus shuts down their home LANs or their important documents won’t open or disappear into thin air just when they need them most.
Of course, we trust a lot more than just our votes to computers these days. We trust our lives to them – and luckily, some of them work extremely well. Commercial airliners today depend on computers for navigation and flight control. Medical treatment now depends heavily on computers. The medical records that doctors consult to make decisions about your health care are often stored electronically. Drug prescription information may now be sent via computer instead of “called in” to the pharmacy. Surgeons can operate “long distance,” controlling robotic arms by computer. And the information in the insurance company’s computer may determine whether or not you get admitted to the hospital or your treatment is approved at all.
We also trust our money to computers – most banking transactions are done electronically now. If you use direct deposit and pay your bills online, you may never see a paper version of your money (cash or check). The day will probably come when money as we know it is a thing of the past, and electronic bits and bytes are all we earn for our hard work.
Computerized information may determine whether you enjoy your freedom or get locked up. Who hasn’t heard the horror stories about people being arrested because of a warrant that showed up when a clerk ran a criminal history check on the computer?
Our cars run on computers, climate control in our malls and office buildings run on computers, and more and more, our homes are run by computers, too. And of course our national infrastructure is completely dependent on computers. They control the electrical grids, the municipal water supplies, the public sewer systems.
Many people began to question our growing dependency on our machines prior to the turn of the century. But despite dire predictions, Y2K turned out to be a bust – planes didn’t fall out of the sky, homes and businesses didn’t lose power, banks didn’t close … pretty much nothing happened. And computers have wedged their ways even deeper into our lives since then.
But are we precariously balanced on the edge of disaster? Would a large electromagnetic pulse (EMP) render all of our fancy technology unusable? Or is that just the stuff of science fiction novels? Since it’s never happened on a large scale, nobody really knows for sure.
It’s unlikely that anything short of such a disaster will cause our world to reduce its dependency on technology. Instead, computers are likely to become more ubiquitous as time goes on, and eventually they’ll just be built into everything, rather than functioning as standalone machines. That’s already true to a large extent. How does that make you feel?
Let us know what you think. Do you trust the computers on which your livelihoods and lives depend? Do you trust some types of computers more than others? Why? What are some examples of the positive effects of increasing computerization? What are the negative effects? Do you think we’re headed for a rude awakening some day when all the computers die? Let us know your opinions.
Deb Shinder, MVP
Nothing much to see here, just some run-of-the-mill domain fraud.
Doorshot(dot)com, a porn site that serves up hardcore porno videos (funded through Zango Seekmo installs), registers itself to Bill Gates.
Domain Name: DOORSHOST.COM
Registrant:
microsoftin
gates (gateshost @ gmail.com)
bolaklava 12 st.
NY, null,36568
US
Tel. +1.5635632145
Domain servers in listed order:
ns0.hqhost.net
ns1.hqhost.net
And here’s the Seekmo install screen from one of their vids:
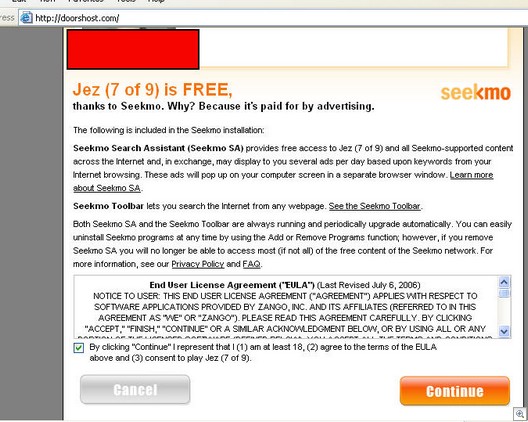
Patrick Jordan

FTC strikes again, shutting down the notorious Media Motor.
A U.S. district court has shut down an operation that secretly downloaded multiple malevolent software programs, including spyware, onto millions of computers without consumers’ consent, degrading their computers’ performance, spying on them, and exposing them to a barrage of disruptive advertisements. The Federal Trade Commission has asked the court to order a permanent halt to these deceptive and unfair downloads, and to order the outfit to give up its ill-gotten gains.
The FTC charged ERG Ventures, LLC and one of its affiliates with tricking consumers into downloading malevolent software by hiding the Media Motor program within seemingly innocuous free software, including screensavers and video files. Once downloaded, the Media Motor program silently activates itself and downloads “malware” – software that is intrusive, disruptive, and makes it difficult for consumers to use their computers.
Link here.
Alex Eckelberry
(Thanks Eric Howes)
Some new sites to look out for.
IP: 85.255.117.204
securecheck(dot)biz
IP: 85.255.117.204
yourguardonline(dot)biz
IP: 85.255.118.243
esafetypage(dot)com
IP: 85.255.118.246
eprotectpage(dot)com
IP: 85.255.118.246
esecuritypage(dot)com
Patrick Jordan
There are lots of jobs advertised out there (through spam or other means) that are just an outright scam.
A good overview of the situation is at CareerBuilder.com. Don’t fall for these “jobs”. You might end up in jail.
Lured by convenience and seemingly easy money, more and more people are falling prey to job scams. Particularly vulnerable are people who want or need to work from home and those who are looking supplement their income. Those who fall victim can suffer serious consequences including debt collection and criminal charges.
Work-at-home scams are varied and can be more difficult to detect. They come in many different forms and change regularly. To protect yourself, it’s important to be aware of the various scams lurking and what to do if you suspect you discover one.
Link here.
Alex Eckelberry
(Hat tip to Andy Meyers)
George Ou gives a good overview of this new exploit that’s been published, with the fix.
This exploit potentially affects any wireless client using the Broadcom BCMWL5.SYS device driver (this exploit has been confirmed to work on version 3.50.21.10 of the driver).
This is a serious exploit, mitigated only by the fact that someone has to get into wireless range of your PC in order to attack your system (100 to 200 feet, more with a high-powered antenna). However, this does not mean that it should be taken lightly. Follow the instructions below to patch the driver.
From the Month of Kernel Bugs site:
The Broadcom BCMWL5.SYS wireless device driver is vulnerable to a stack-based buffer overflow that can lead to arbitrary kernel-mode code execution. This particular vulnerability is caused by improper handling of 802.11 probe responses containing a long SSID field. The BCMWL5.SYS driver is bundled with new PCs from HP, Dell, Gateway, eMachines, and other computer manufacturers. Broadcom has released a fixed driver to their partners, which are in turn providing updates for the affected products. Linksys, Zonet, and other wireless card manufactures also provide devices that ship with this driver.
Link here.
Linksys has an update to the driver, here, which is believed to work with any system using the Broadcom device driver (as most of you know, it’s common in the hardware world for one company to sell software or hardware to multiple different companies).
So if you’re running the Broadcom driver, update it as soon as possible.
Alex Eckelberry
Over the whole AV thing:
When the articles and blogs started appearing, I asked the PR folks to send me a copy of the transcript of the call so I could read it over and see if I said something I didn’t mean. After reading the transcript, I could certainly see that what I said wasn’t as clear as it could have been, and I’m sorry for that. However, it is also clear from the transcript that I didn’t say that users shouldn’t run antivirus software with Windows Vista! In fact, later in the call, I explicitly made this point again, because I had realized I wasn’t as clear as I should have been. It’s important for me that our customers are using the appropriate security solutions for the right situations, whether that’s security functionality integrated in the operating systems, or add-on products.
Link here, with more at Betanews.
Alex Eckelberry
I have no beef with Allchin, but this seems optimistic:
During a telephone conference with reporters yesterday, outgoing Microsoft co-president Jim Allchin, while touting the new security features of Windows Vista, which was released to manufacturing yesterday, told a reporter that the system’s new lockdown features are so capable and thorough that he was comfortable with his own seven-year-old son using Vista without antivirus software installed.
Link here (via realtech and Jeff Nolan).
Ok, Vista is a vastly improved security model, but what about the fact that probably well over 90% of all viruses come through email? You get an email that says “Please reset your password, open the attached file”, you open it and it’s a virus. It’s the user executing a virus. How will Vista protect against that? Furthermore, what about downloading a trojan?
Alex
Yesterday, the American Bar Association gave the green light for lawyers to view metadata (extraneous information in a file such as who created it, what changes have been made, etc.). .
Lawyers who receive electronic documents are free to look for and use information hidden in metadata – information embedded in electronically produced documents – even if the documents were provided by an opposing lawyer, according to a new ethics opinion from the American Bar Association.
The opinion is contrary to the view of some legal ethics authorities, which have found it ethically impermissible as a matter of honesty for lawyers to search documents they receive from other lawyers for metadata or to use what they find, according to the ABA Standing Committee on Ethics and Professional Responsibility.
Link here (via beSpacific).
You can also see go to my previous posting on metadata, which included a link to the free Remove Hidden Data tool.
Alex Eckelberry
IP: 216.255.187.70
lightcodec(dot)com
IP: 69.50.188.104
elitecodec(dot)com
IP: 85.255.118.243
eupdatepage(dot)com
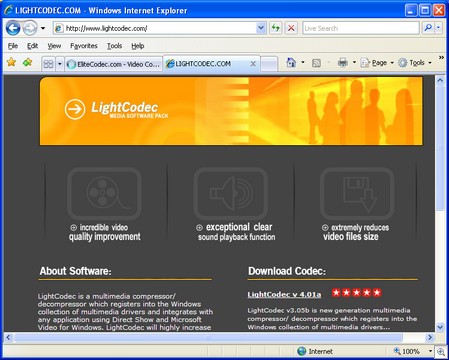
Patrick Jordan
Fake 404s for malware are not that uncommon, but check this one out from our palls at amaena(dot)com:
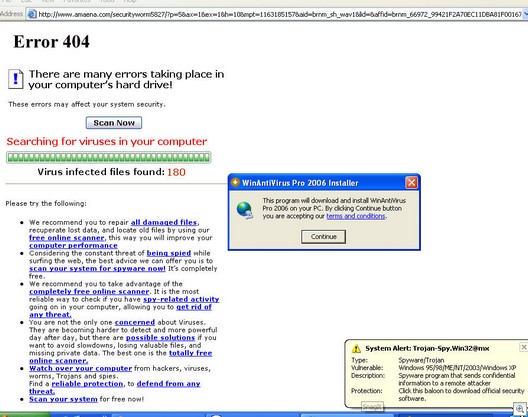
And at errorsdns(dot)com:
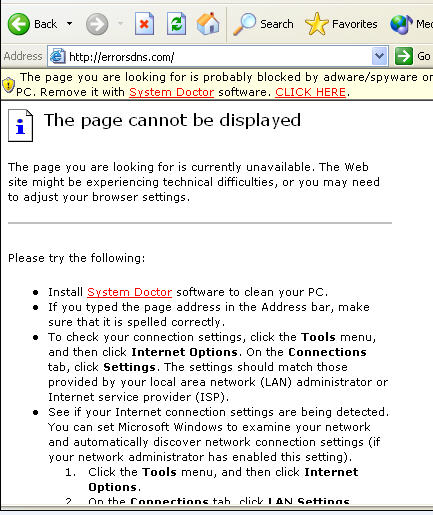
Patrick Jordan
Courtesy of Innovative Marketing…
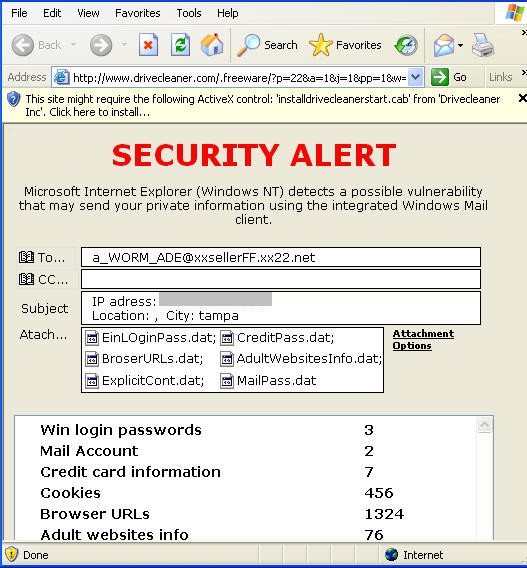
And while we’re at it, this is the group who first started with Internetantispy(dot)com (which opened the CDRom door to scare you into buying their application). Now we see amaena(dot)com using popup scare messages.
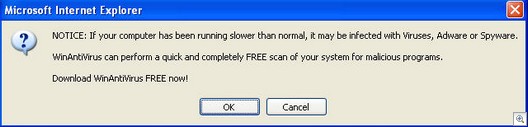
This is their latest URL: amaena(dot)com/vista, so it looks like they are getting ready to use the name Vista when Microsoft releases it.
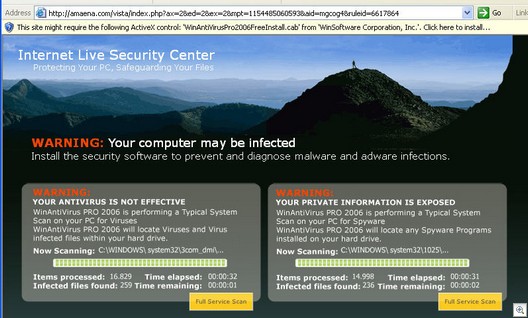
Patrick Jordan

(From the CA/B forum, the green chrome that would be in IE 7 for EV SSL)
Help for phishing? The CA/Browser forum has published a draft guidelin for Extended Validation SSL:
EV SSL is a “’voluntary ‘standard’ that would impose rigorous authentication policies via participating certificate authorities, who will be independently audited for compliance. In return, websites with EV SSL would get special treatment in the browsers, including a “green chrome” in IE7 and an expanded security report showing the owner of the website. (Existing domain validation and organisation validation certificates would retain the simple ‘padlock’ display).”
Link here.
Alex Eckelberry
Not many people know this, but you have the right and abiltiy to get certain insurance records — and correct the information if it’s wrong. If you’re interested in getting a copy of your health insurance records, you can go to the Medical Insurance Bureau and request a copy. It’s not much fun going through the firm’s voice response system, but you’ll get your file with a bit of patience. (Note that if you have not applied for individually underwritten life, health, or disability insurance over the last seven years, MIB will not have a record on you.)
You can also listen to an interview with Michael Ravnitzky on the subject here.
Alex Eckelberry
I don’t buy this study. This would indicate that out of a billion users, over 100 million have fallen for a phishing scam. While plenty of people fall victim to phishing attacks, it’s nowhere near that number.
One in 10 internet users may be lured into handing over sensitive personal information such as a credit card number, by fraudulent “phishing” emails, research suggests…
Previous studies, including a telephone survey conducted by US research company Gartner in 2004, have indicated that about 5% of all internet users have fallen for phishing messages.
But Markus Jakobsson and Jacob Ratkiewicz at Indiana University, US, suspected this was an underestimation. The reasoned that some survey participants may not have realised that they have been stung by a phishing scam, or may simply be too embarrassed to admit to it.
The research methodology is interesting: This team actually created a fake phishing site to see who would respond.
New Scientist article, link here. More at beSpacific, including a study on ethical phishing experiments.
Alex Eckelberry
Devious.
We start with a link in a post:

The link points to www(dot)logins-myspace-profiles(dot)n3t.nl, which opens an IFrame and loads the following site (www(dot)myspace-profileviews(dot)com/login/). This is a very realistic phishing site, complete with the same ads served on myspace.
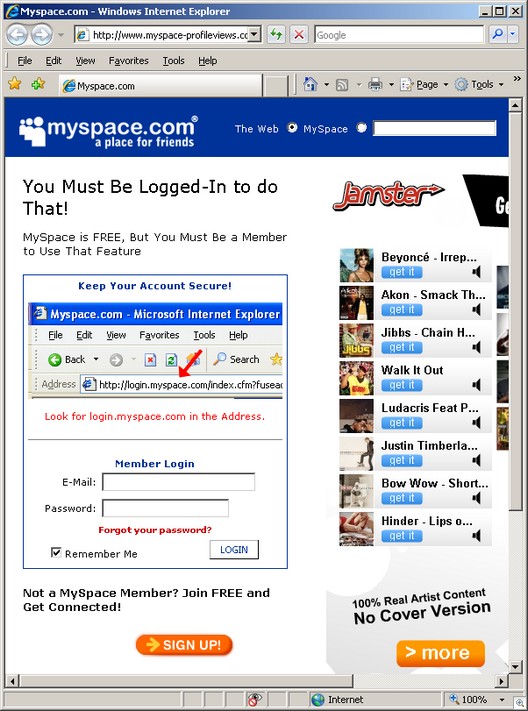
More at Todd Towles’ site (thanks Todd for sending this to me).
Alex Eckelberry
This one has been out for a while but now it’s reported in the wild.
From SANS:
Rohit from Tippingpoint adviced us that he is seeing a large number of attacks from Russia using an un-patched vulnerability in the WMIObjectBroker ActiveX control (CVE-2006-4704). He is seeing it used as part of a drive-by download. Typically, the Trojan “Galopoper.A” is load.
There is no patch available at this point. Tippingpoint and the Bleedingthreats projects have signatures available to detect this attack. Rohit mentioned that there is a metasploit module for this vulnerability.
Microsoft link here, with workarounds.
Secunia here.
CERT here.
I’ll have more news as it comes out.
Alex Eckelberry
|