Guess what? A new site, Downloadmalware com, offers free malware.
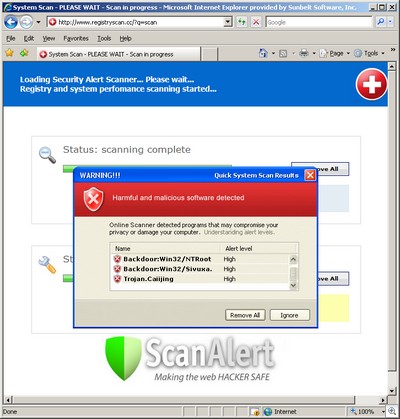
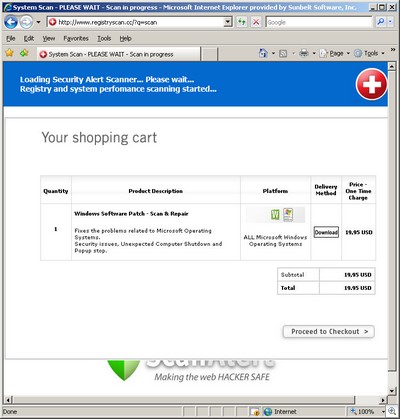
No. Really. What you get is a Vondu/Virtumonde trojan.
There’s full-disclosure on the site:
Commence Tomfoolery
Everyone knows that it’s no fun getting a virus, and viruses can be obtained by doing basically anything on the internet. That’s why we created Malware, in order to finally put a stop to constant viral infections on your personal computer. We have many competitors, and they may be more popular than us, but at some point in this company’s career, we will surpass them. It’s all about persistence and determination, and I would know because I just wrote an essay about that.
personal computer. We have many competitors, and they may be more popular than us, but at some point in this company’s career, we will surpass them. It’s all about persistence and determination, and I would know because I just wrote an essay about that.
Our Approach: As stated on the main page, our methods of preventing viruses are very similar to how the common flu is prevented. We inject your computer with a small ‘virus‘ so that your computer can build up an immunity to all viruses in general. In the past, technology was incapable of developing a program like this, but thanks to new dreamweaver technology by adobe, millions of users around the world are now protected from the most deadly computer viruses.
To, Delve into the Situation Further: Our malware program includes a packaged installer. This packaged installer contains two separate files. One of these files is full of little bits of viruses, and the other package contains the white blood cells of nanotechnology. After the virus is installed, the Wano Cells (White-Nano-Cells) are released into the computer’s data stream. The Wano’s are programmed to seek, analyze, and destroy any form of virus that your computer might have. This super advanced sense of analysis is almost like human instinct, and is the future of virus prevention and removal!
At the bottom of the page, he says:
Warning, this is actually a program that causes popups on your computer… I’m pretty sure it’s harmless but I don’t think you should try and find out. If you download this program you’re dumb! This post is a joke.
Well, it’s not a little piece of malware. Vondu/Virtumonde is anything but.
The author admits to feeling some guilt about putting up a website that openly delivers malware, but feels justified in that he feels anyone stupid enough to actually download the malware kinda deserves it.
This is my attempt at a sort of viral website. It could be seen as a “youfail” sort of site that forum users point to when someone asks a dumb question. I’m not really sure but I’m hoping it works.
I made it blatantly obvious that the file up for download is malware, so anybody who does download and install the program I have uploaded is retarded (nothing against retarded people). The catch is, it’s the affiliate adware from luxecash so I get money every time someone actually does download and install it.
I don’t know whether or not I should deck the site out with ads, or if I should keep it ad free to legitimize the product. I guess I’ll just have to wait and see if there are any people out their who would bite. I’m under the impression that people without a lot of computer knowledge would actually believe it.
It sort of makes me feel like a dick, but since I clearly state that it’s malware… it’s better than uploading it to a torrent site saying it’s msn messenger or something right?
And his own blog post, he has this to say:
…I decided that instead of taking the conventional approach to making money, I would make up my own way. I realized that spending hours uploading files to torrent websites would be just like me actually going to work for a few hours in order to make money. Now, not that I’m against doing a little bit of work for the money, but the only way to make good money requires that you do some illegal things, and work.
So I came up with downloadmalware.com, where people can voluntary download my adware. People like my mother (who will eventually read this post) are really the only people I can expect to download the adware from that site. One would have to be some un-saavy with computers it would be rather disturbing. Not only would you be displaying your lack of computer-vocab, but an extremely huge amount of gullability. For that purpose, I don’t feel so bad knowing that I’m giving someone popups, and I’m also glad what I’m doing isn’t illegal.
I’ll update this with some info on how the site works out for me… but I’ll have to give it some time to saturate in there with the big Goog.
Someone asked in a comment what the malware was, the malware is simply the luxecash affiliate program installer. I’ve never tried installing it on my own computer, but I’m pretty sure it’s just adware… so you get popups every once in a while.
Ok, I have a sense of humor. I get it.
But this is not funny at all.
I hope this enterprising fellow takes this crap down as soon as possible.
Alex Eckelberry