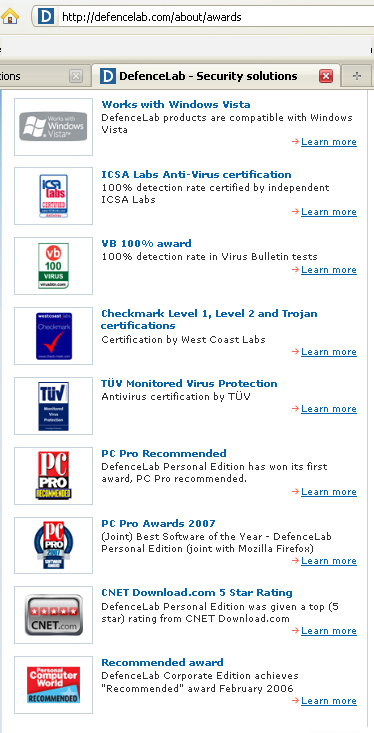
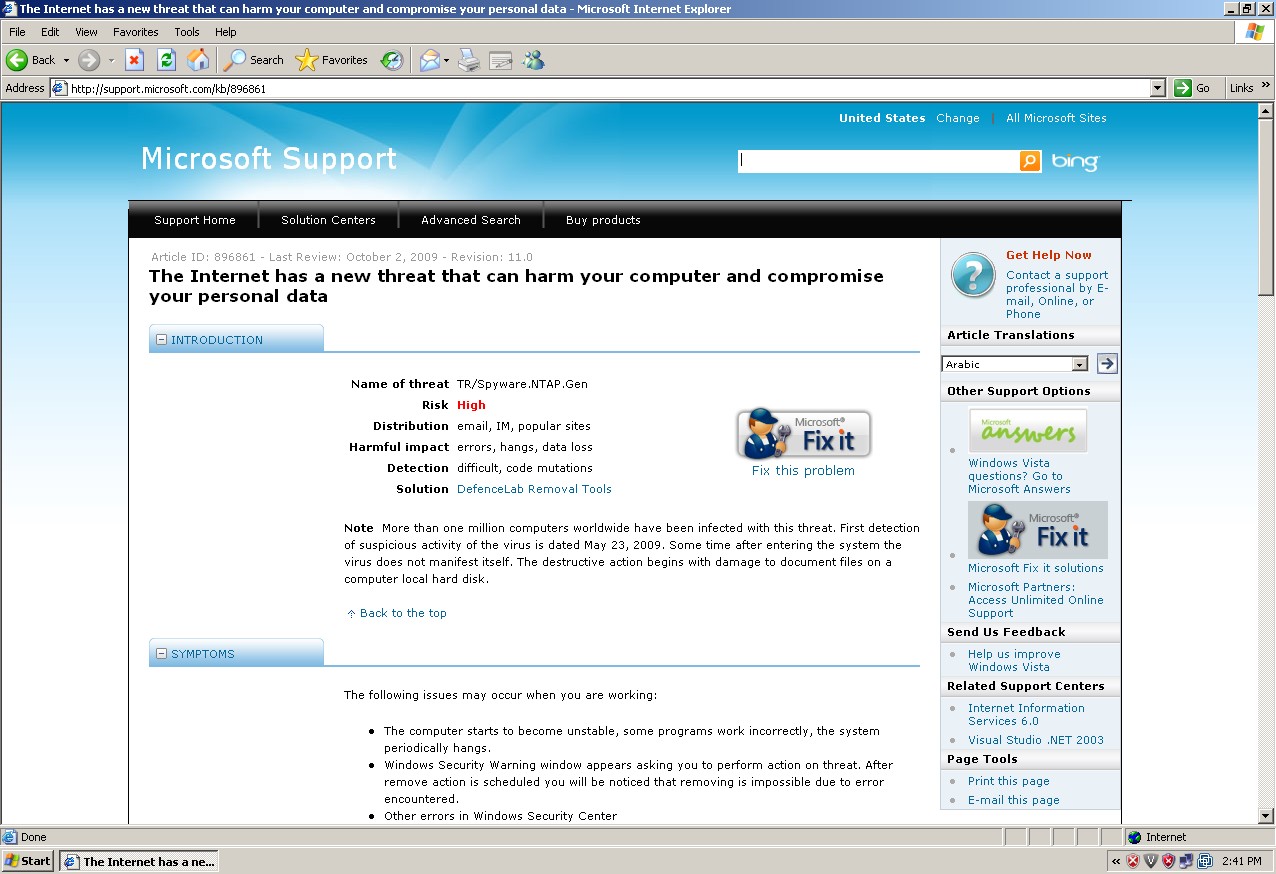
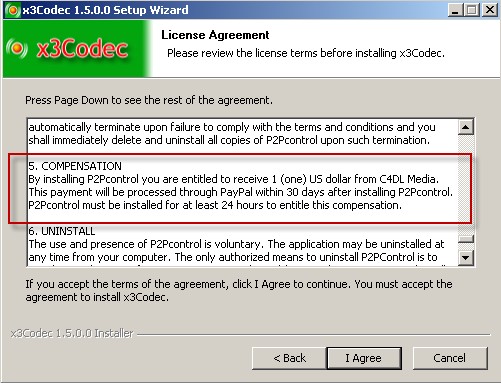
Yes, that’s right: 3.6 zettabytes!
A report entitled “How Much Information” by the University of California in San Diego, released today, said the average person in the U.S. consumes 34 gigabytes of content and 100,000 words of information in a single day. That’s just at home.
The number of bytes we consumed increased at six percent per year from 1980 to 2008, the report said.
TV and video games are responsible for a big chunk of that. People are reading more too, since browsing the web is considered reading.
The report says “We estimate that an average American on an average day receives 11.8 hours of information a day.”
The project was funded by AT&T, Cisco Systems, I.B.M., Intel, LSI, Oracle and Seagate Technology, with early support from the Alfred P. Sloan Foundation.
The report didn’t mention security, but, basically a lot of that data needs some kind of security protection. “Ten years ago 40 percent of U.S. households had a personal computer, and only one-quarter of those had Internet access. Current estimates are that over 70 percent of Americans now own a personal computer with Internet access, and increasingly that access is high-speed via broadband connectivity,” the report said.
Yep, 3.6 zettabytes per year – that’s a 36 with 20 zeros. It really puts the security issue into perspective (if you can wrap your head around the concept of a “zettabyte.”)
NYT story here.
Univ. of Calif. study report here.
Tom Kelchner