Our analyst Adam Thomas came across this ugly new social engineering technique when he analyzed the DefenceLab rogue security product.
It does the usual scare-ware stuff: a fake scan and fake “Windows Security Center” alert:


Then it directs the potential victim to a Microsoft Support page, but injects html code into the page in his or her browser to make it appear as though Microsoft is suggesting the purchase of the rogue.
This is the real Microsoft page:

This is what it looks after DefenseLab changes it:
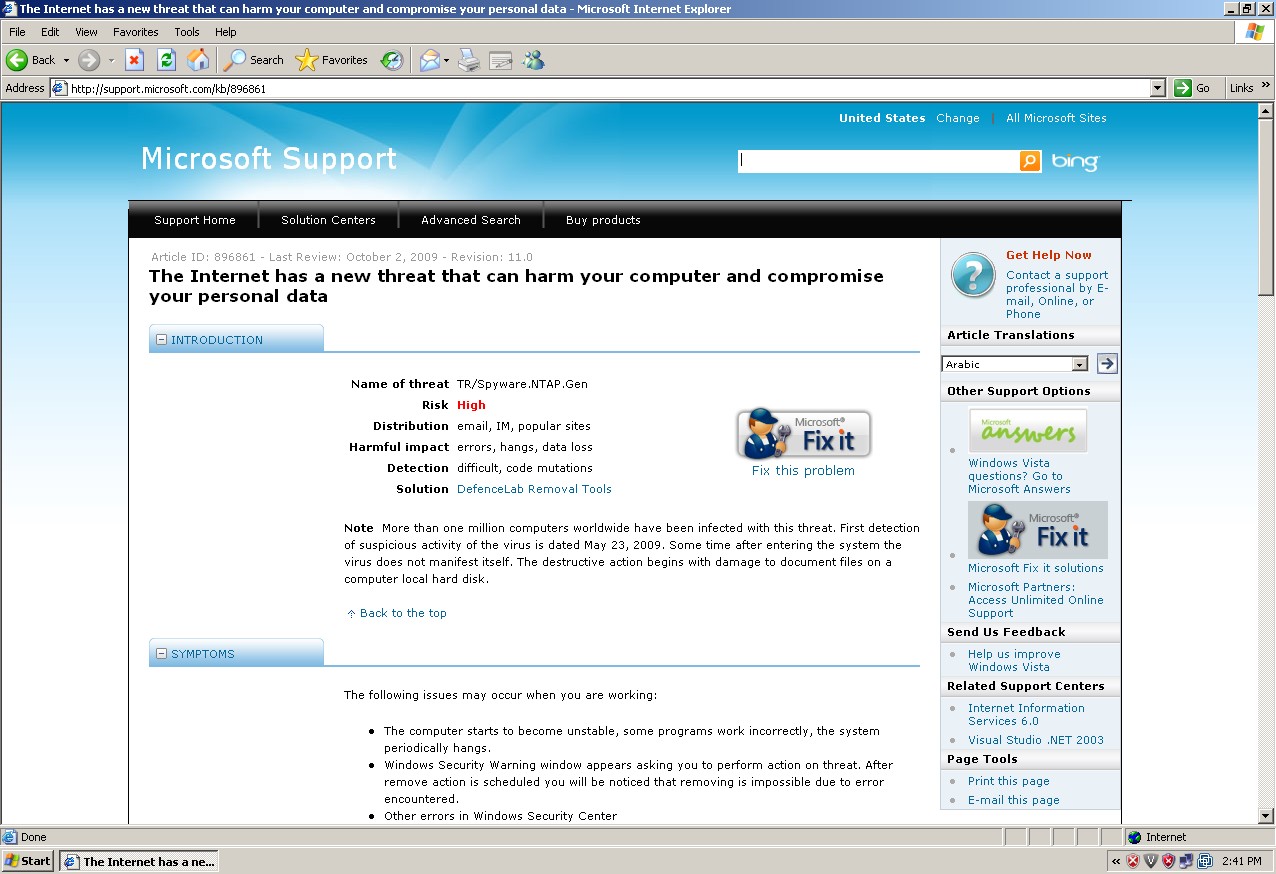
Thanks Adam
Tom Kelchner
