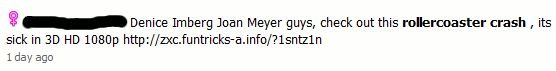Delicious cake – for years, the symbol of a reward never to materialise.
This sad trend continues with the upcoming release of Portal 2, which – as you would expect – is prompting a rash of utterly fictitious cake designed to lure the unwary into mind bending puzzles of a three dimensional nature, or at least some surveys and a slice of malware.
Over the last few days, Twitter users have reported a huge wave of Portal spam.and this will no doubt continue to be an annoyance as excitement builds over the release. Much of the spam makes no sense, or mashes up random Portal related comments and lines.
See if you can spot the cake mention (yes, this cake was a lie too):
A lot of these spambots were directing users to a “Portal 2 Loader” (hat tip to MrTom), which has been downloaded roughly 4,000+ times and appears to be a Portal 2 crack.
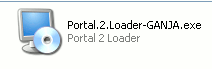
We’re still taking a look at this one, but personally I’d steer clear.
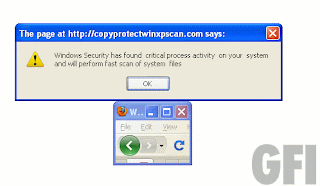
Elsewhere, we have dubious search results. Simply looking for “Portal 2 Still Alive” (you know, the catchy ditty sung by the smiley death robot at the start of the writeup) will bring you a liberal scattering of this:
And also some of that:
Many of the sites are currently down, but there’s a lot of dubious results in there so be careful (you can also bring up a bunch of them by searching for the songwriter, the awesome Jonathan Coulton). In a nutshell, any searches involving songs and a state of being alive may serve up some bad vibes in your general direction.
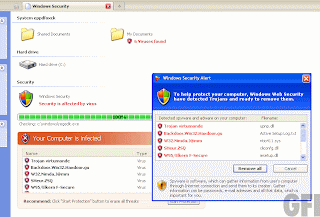
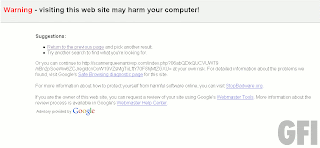
Are those “this site may harm your computer” warnings useful or what?
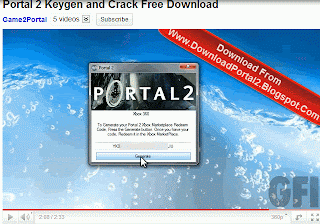
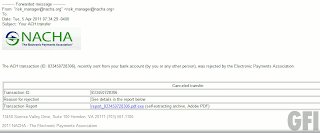
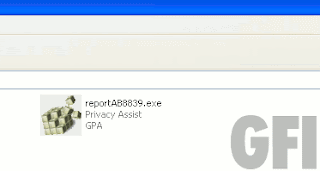
Anyway, we also have the usual Youtube suspects in the form of endless “Portal 2 keygen / crack” videos:
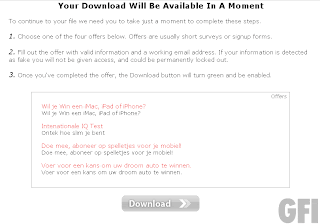
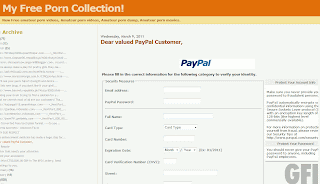
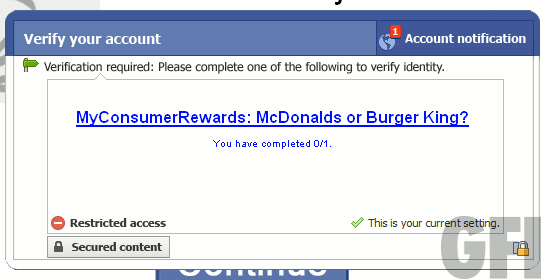
Without fail, they’ll all dump you on cookie cutter blogs and file upload sites that want some surveys filling in:
Needless to say, filling in these surveys won’t give you a working crack – it’ll be a non functional dummy file or an infection.
I can tell you this much for certain, there definitely won’t be any cake.
There never is.
Christopher Boyd