(Adam Piggott of Proactive Services originally found this mess, contacted Suzi Turner at SpywareWarrior who got him in touch with one of our spyware researchers, Adam Thomas.)
Discussions about botnets in the security community are quite active these days. And there’s a reason: They’re out there and they’re very nasty. Here’s one in action that’s live today.
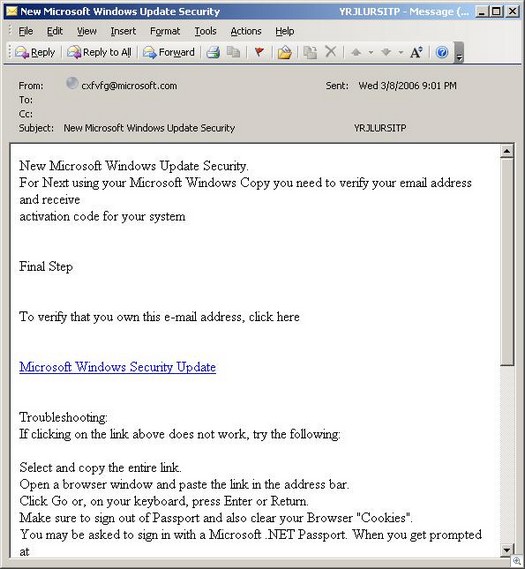
Take this innocent piece of spam (it looks better normally, but the website they are pulling the pictures from is down).
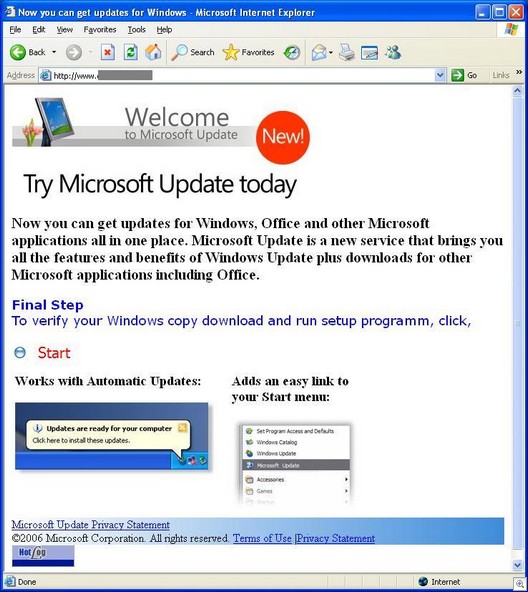
A spam like this will take you to a fake Windows update site:
If you visit the site, they will attempt to run a WMF exploit (video of a related site by Suzi Turner here). If you are patched with the January 5 security update from Microsoft (or have decent AV protection) but still fall for clicking on the “Start” link, you will download a trojan installer, wusetup.exe, which sets up the machine to be controlled in a botnet (virustotal.com results for this trojan here).
The wusetup.exe loads files that turn your machine into a proxy server – you are becoming a member of a bot-net. It brings down these files:
ieschedule.exe ib7.dll smss.exe harvest.exe ieserver.exe loader.exe
There’s also remote control and keylogging involved. You get a copy of Famatech’s Remote Server (part of Famatech Radmin) — r_server.exe. And last night, Adam Piggott tipped us off about an affiliate site which installs, through an old Windows help file exploit, a variant of the Winldra keylogger. And the site shown above is directly implicated.
What happens after this is all installed?
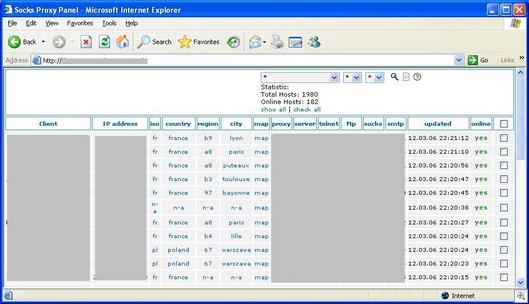
It all comes down to a botnet controller, which probably looks similiar to this one (this controller I’ve pictured is actually live right now so I’ve obscured sensitive information):
In this controller, you can access a person’s hard drive and perform other tasks.
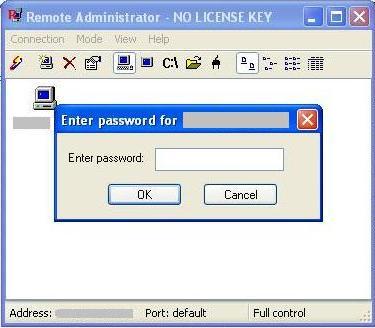
And since apparently most, if not all, of these machines have Remote Server on them, you can access them through Radmin, which I tested just now against one of the infected systems. The “password” dialog box below means the system is running Remote Server.
Famatech Remote Administrator (Famatech Radmin) is also sold as an OEM version by Sunbelt as Sunbelt Remote Administrator (Sunbelt Radmin). It is a normal remote control program but used in the wrong hands can be quite nasty, because it has the unique property of being able to operate in “stealth” mode — the tray icon can be hidden. It’s one reason why we detect Radmin ourselves in CounterSpy as a potential risk.
Alex Eckelberry (Thanks to Sunbelt spyware researcher Adam Thomas and Adam Piggott for his diligent work and for providing us a copy of the spam message you see above)